
30 June 2025

During our investigation, we are used to work with a wide variety of artifacts. Some of them are well documented, for some others analysis is more complicated, little research exists on the topic and known existing tools do not always work. One of those artifacts is the Windows Defender Detection History (WDDH) file. This file is generated by Windows Defender (on Windows 10 and later) upon threat identification and contains some valuable information such as threat file hash, associated users, file path and initiating processes. Depending on the identified threat the detection can contain full malicious command line- or registry key access. These files can be found at the following path:
C:\ProgramData\Microsoft\Windows Defender\Scans\History\Service\DetectionHistory\[0-9]{2}\{GUID}.Some information found on these files may also be present in other defender logs, but depending on the situation WDDH artifact can provide a nice complement of information.
The following example shows information found on samples from the DFIRArtifactMuseum, as displayed by the WDDH cli tool developed after our analysis.
{
"threat_id": 2147714397,
"threat_name": "HackTool:Win32/Vigorf.A",
"threat_status": "RemoveFailed",
"domain_user": "DESKTOP-TMKU40H\\TestUser",
"domain_user_group": "NT AUTHORITY\\SYSTEM",
"process_name": "C:\\Windows\\explorer.exe",
"initial_detection_time": "2022-03-10T19:49:23.577669+00:00",
"remediation": "2022-03-10T19:49:57.686672+00:00",
"ressources": [
"file C:\\Users\\TestUser\\Downloads\\APTSimulator_pw_apt\\APTSimulator\\test-sets\\credential-access\\mimikatz-1.bat",
"file C:\\Users\\TestUser\\Downloads\\APTSimulator_pw_apt\\dist\\APTSimulator\\test-sets\\credential-access\\mimikatz-1.bat"
],
"misc": {
"ThreatTrackingSha256": "c3e757436c8afbb69d5adf68cb8d6c4abcbf70a49cbcaf39d3a6f4a7ce30df2e",
"ThreatTrackingSigSeq": 42226927648562,
"ThreatTrackingId": "778C3896-112C-4205-A6EF-AE7145ED837B",
"ThreatTrackingStartTime": 132914153734223440,
"ThreatTrackingThreatName": "HackTool:Win32/Vigorf.A",
"ThreatTrackingSha1": "15c8ecf4e91a523333193e95f7a5b9729ea6142c",
"ThreatTrackingSigSha": "3f120c9f146a2524f873e07e8877165f18614730",
"ThreatTrackingSize": 847,
"ThreatTrackingMD5": "8b9a58c02cd1e931c961ea1cee62d459",
"ThreatTrackingScanFlags": 3,
"ThreatTrackingIsEsuSig": false,
"ThreatTrackingThreatId": 2147714397,
"ThreatTrackingScanSource": 0,
"ThreatTrackingScanType": 0
}
}
Investigation on this topic started following errors when we were processing this artifact on samples collected during a particular investigation and the will to better understand this artifact. Furthermore, as only little public research was available, we found that more research on this topic could be valuable, even if it only validates previous work on the matter. Research goals were identifying artifact data structure and providing a small, dedicated tool allowing to dump information founds on this file. This article will give more details on the analysis methodology, then going into artifact working details.
Even if some research has previously been done on the inner data format, documented in libyal/dtformats and available inside log2timeline/plaso source code, analysis was started from scratch, without considering these previous results. This allows for a more critical consideration of previous works.
Due to lack of documentation from Microsoft on this topic, reverse engineering was required to understand the data format. As the Windows code base is wide, we needed to identify binaries or DLLs where these files are created or manipulated. Two methods were tested:
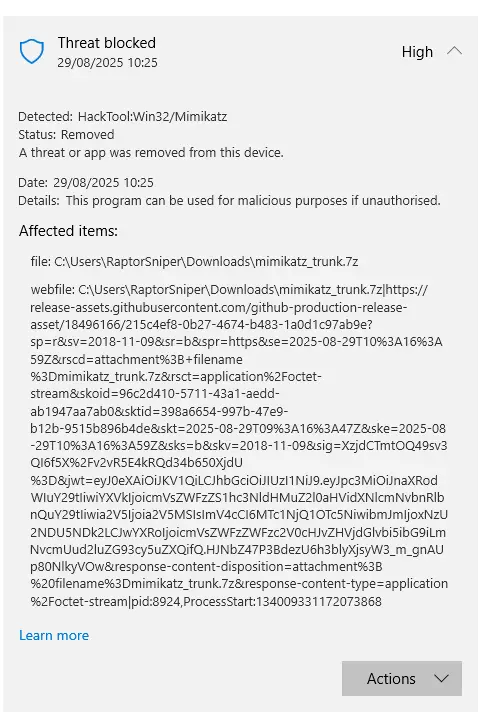
The first method was to use procmon.exe to monitor for file access within the folder C:\ProgramData\Microsoft\Windows Defender\Scans\History\Service\DetectionHistory and download a well-known offensive tool such as Mimikatz in order to trigger the creation of one of those files. As seen in the following screenshot, MsMpEng.exe binary, which is (unsurprisingly) the binary associated with Microsoft Defender, manipulated one of the files upon detection. Quick reverse engineering of MsMpEng.exe did not allow to identify the part of the code where these files were manipulated.
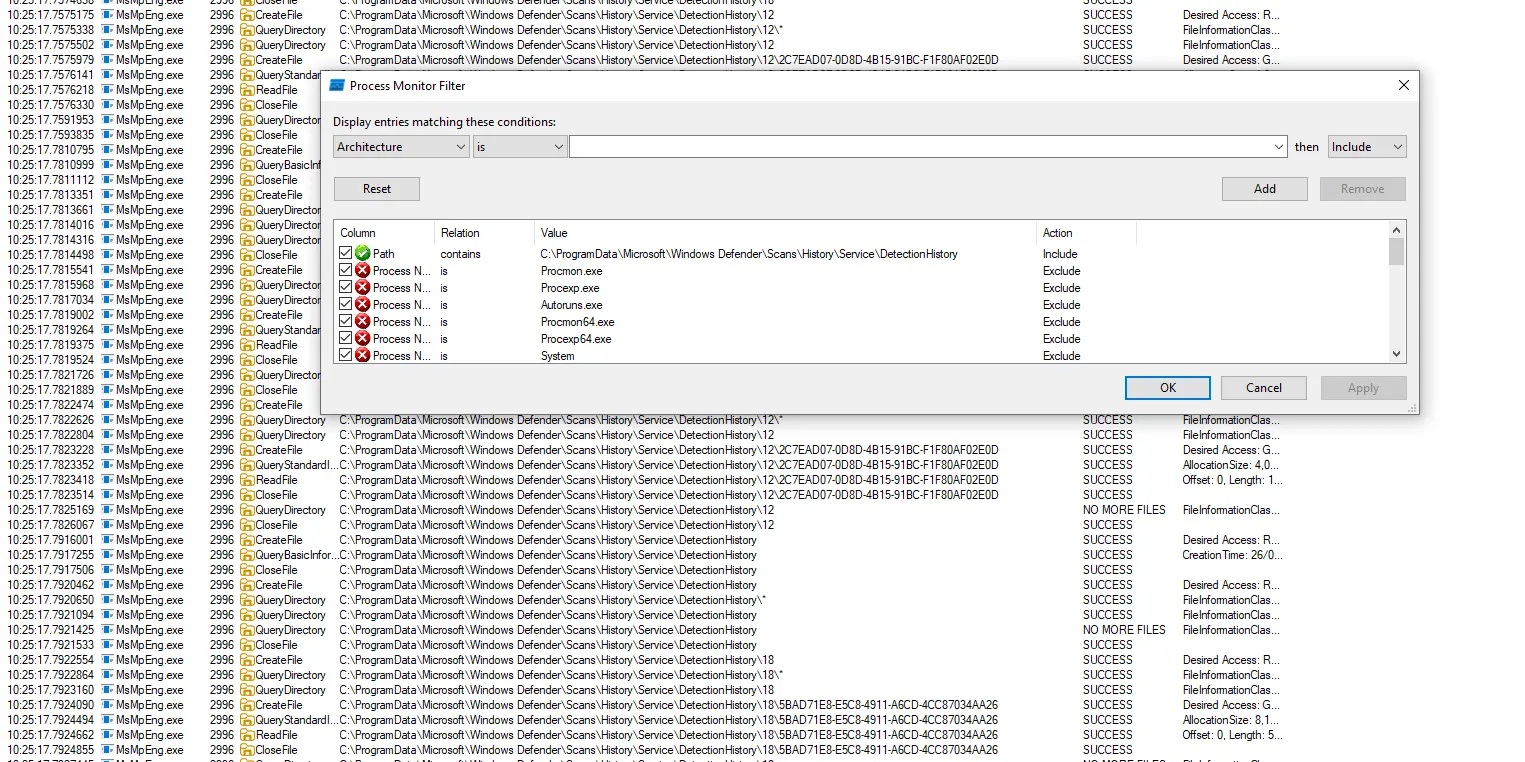
The second method involved using Ripgrep (enhanced grep). We attempted to identify certain files containing references to the artifact path. As MsMpEng.exe is located under the path C:\ProgramData\Microsoft\Windows Defender\Platform\<version> the search was conducted only in the C:\ProgramData\Microsoft\Windows Defender folder.
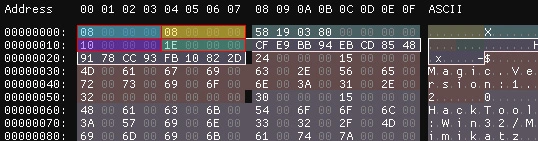
Furthermore, examination of some samples using a hexadecimal editor shows the string Magic.Version: as being present. We can also expect presence of this string in code related to this artifact:
00000000: 0800 0000 0800 0000 5819 0380 0000 0000 ........X.......
00000010: 1000 0000 1e00 0000 cfe9 bb94 ebcd 8548 ...............H
00000020: 9178 cc93 fb10 822d 2400 0000 1500 0000 .x.....-$.......
00000030: 4d00 6100 6700 6900 6300 2e00 5600 6500 M.a.g.i.c...V.e.
00000040: 7200 7300 6900 6f00 6e00 3a00 3100 2e00 r.s.i.o.n.:.1...
00000050: 3200 0000 0000 0000 3000 0000 1500 0000 2.......0.......
00000060: 4800 6100 6300 6b00 5400 6f00 6f00 6c00 H.a.c.k.T.o.o.l.
00000070: 3a00 5700 6900 6e00 3300 3200 2f00 4d00 :.W.i.n.3.2./.M.
00000080: 6900 6d00 6900 6b00 6100 7400 7a00 0000 i.m.i.k.a.t.z...
00000090: 0400 0000 0600 0000 0000 0000 0000 0000 ................
000000a0: 0400 0000 0600 0000 0400 0000 0000 0000 ................
000000b0: 0400 0000 0600 0000 2200 0000 0000 0000 ........".......
000000c0: 0400 0000 0600 0000 5700 0000 0000 0000 ........W.......
000000d0: 0400 0000 0600 0000 0400 0000 0000 0000 ................
000000e0: 0400 0000 0600 0000 0300 0000 0000 0000 ................
000000f0: 0400 0000 0600 0000 0300 0000 0000 0000 ................
00000100: 0400 0000 0600 0000 0200 0000 0000 0000 ................
00000110: 0400 0000 0600 0000 0300 0000 0000 0000 ................
00000120: 0400 0000 0600 0000 0600 0000 0000 0000 ................
00000130: 0400 0000 0600 0000 0100 0000 0000 0000 ................
00000140: 2400 0000 1500 0000 4d00 6100 6700 6900 $.......M.a.g.i.
00000150: 6300 2e00 5600 6500 7200 7300 6900 6f00 c...V.e.r.s.i.o.
00000160: 6e00 3a00 3100 2e00 3200 0000 0000 0000 n.:.1...2.......
00000170: 0a00 0000 1500 0000 6600 6900 6c00 6500 ........f.i.l.e.
00000180: 0000 0000 0000 0000 4c00 0000 1500 0000 ........L.......
00000190: 4300 3a00 5c00 5500 7300 6500 7200 7300 C.:.\.U.s.e.r.s.
000001a0: 5c00 5200 6100 7000 7400 6f00 7200 5300 \.R.a.p.t.o.r.S.
000001b0: 6e00 6900 7000 6500 7200 5c00 4400 6f00 n.i.p.e.r.\.D.o.
000001c0: 7700 6e00 6c00 6f00 6100 6400 7300 5c00 w.n.l.o.a.d.s.\.
000001d0: 6100 2e00 7a00 6900 7000 0000 0000 0000 a...z.i.p.......
000001e0: 0400 0000 0600 0000 0100 0010 0000 0000 ................
000001f0: 0400 0000 0600 0000 0905 0000 0000 0000 ................
The following command allows to identify the presence of the string DetectionHistory and Magic.Version in the file C:\ProgramData\Microsoft\Windows Defender\Platform\<VERSION>\MpSvc.dll:
❯ rg -o --encoding UTF-16 -i -uuu -aaa '(.){0,10}(DetectionHistory|Magic\.Version)(.){0,10}' <Path/to/Windows Defender>
<Path/to/Windows Defender>/Platform/4.18.25070.5-0/MpSvc.dll
1201:愐聏�耕Magic.Version:1.2庈聏
1201:lDelayDetectionHistoryMp
1288:rge] PurgeDetectionHistory failed.
1302:torInitDetectionHistoryManagerIn
1302:rShutdownDetectionHistoryManagerSh
1302:initializeDetectionHistoryManagerUn
1327:y\Service\DetectionHistory%ls\Sca
❯ rg -o -i -uuu -aaa '(.){0,10}(DetectionHistory|Magic\.Version)(.){0,10}' <Path/to/Windows Defender>
<Path/to/Windows Defender>/Platform/4.18.25070.5-0/MpSvc.dll
15671:.?AVCDetectionHistoryContext@Mp
15671:.?AVCMpDetectionHistoryManager@Mp
UTF-16 being widely used on the Windows environment, the search was also forced using this encoding.
With this finding we now have an idea of where this file may be generated and processed and were we need to look.
Using a disassembler/debugger such a Ghidra, we were able to find where the Magic.Version string was referenced.
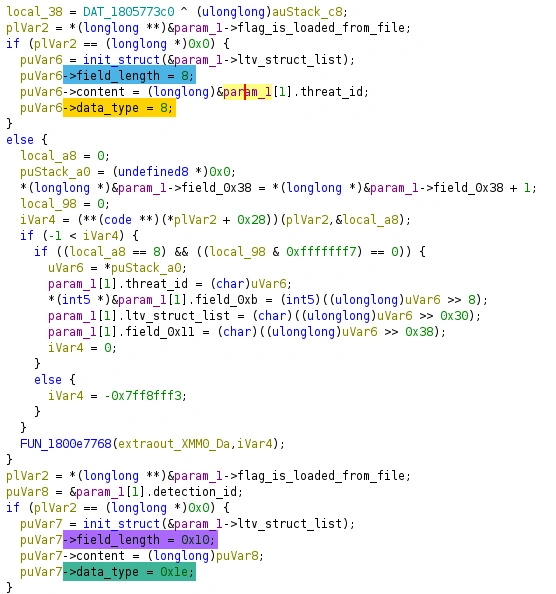
We won't go into all structure details but reversing this function shows that the file format is mainly a sequence of Length - Type - Value. This means that 4 bytes contain the value length, 4 bytes are an enumeration allowing to know the value type and the following bytes are the value. In the tools public repository, a documentation file contains the full list of identified types and the order of these values.
For example, the following capture shows the decompiled code associated with the two first sections (threat id and detection id), and the hexadecimal representation of an artifact file.
One of the file sections is kind of a dictionary sequence, which is mostly human-readable and that contains most of the interesting data. This section does not seem to be generated inside this DLL, and understanding of the data format was mainly based on sample observations. Further analysis shows that this section uses another data structure, in format Type – Value (without the length this time), but for some data types, such as wide str, a 4 bytes value containing length is prepended to the values. This section contains mainly string values; a simple use of the strings tool may allow retrieving part of them.
Using the identified data structure, a first version of the WDDH tools was developed in Python, allowing to process artifact files and dump all related information.
One of the limits of this kind of analysis/reversing is that data structure may change, and it would be a bit time-consuming to retrieve then reverse every version of Windows Defender. It is therefore necessary to find some file to ensure data structure is valid amongst different Defender versions. The following approach was used in order to validate research.
Additionally, as documented by jklepsercyber in the original tool defender-detectionhistory-parser, it's possible to query these files using the following WMI query
Get-WmiObject -Namespace "root\Microsoft\Windows\Defender" -Class MSFT_MpThreatDetection.This is an example of the Query output :
__GENUS : 2
__CLASS : MSFT_MpThreatDetection
__SUPERCLASS : BaseStatus
__DYNASTY : BaseStatus
__RELPATH : MSFT_MpThreatDetection.DetectionID="{94BBE9CF-CDEB-4885-9178-CC93FB10822D}",ThreatID="2147686744"
__PROPERTY_COUNT : 16
__DERIVATION : {BaseStatus}
__SERVER : DESKTOP-O8964S4
__NAMESPACE : root\Microsoft\Windows\Defender
__PATH : \\DESKTOP-O8964S4\root\Microsoft\Windows\Defender:MSFT_MpThreatDetection.DetectionID="{94BBE9CF-CDEB-4885-9178-CC93FB10822D}",ThreatID="2147686744"
ActionSuccess : True
AdditionalActionsBitMask : 0
AMProductVersion : 4.18.24090.11
CleaningActionID : 2
CurrentThreatExecutionStatusID : 1
DetectionID : {94BBE9CF-CDEB-4885-9178-CC93FB10822D}
DetectionSourceTypeID : 3
DomainUser : DESKTOP-O8964S4\RaptorSniper
InitialDetectionTime : 20250128164451.243000+000
LastThreatStatusChangeTime : 20250128164506.220000+000
ProcessName : C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
RemediationTime : 20250128165216.241000+000
Resources : {file:_C:\Users\RaptorSniper\Downloads\a.zip}
ThreatID : 2147686744
ThreatStatusErrorCode : 0
ThreatStatusID : 3
PSComputerName : DESKTOP-O8964S4
Using a hexadecimal editor we were then able to modify some file bytes, and using the WMI query for identifying if the field modification has an impact on displayed values. These tests allow identifying field meanings that we were unable to understand using reverse engineering. For example, when modifying the content of an integer using a hexadecimal editor, the result of the following WMI query shows that the ThreatStatusErrorCode value is modified to this value. So we can assume that this integer represents the ThreatStatusErrorCode.
To use the tool, simply provide a file path using the -i/--in option flag. The -s/-short flag allows to only display most important fields. It can be removed in order to dump the whole file structure.
❯ wddh -s -i samples/original/94BBE9CF-CDEB-4885-9178-CC93FB10822D | jq '.'
{
"threat_id": 2147686744,
"threat_name": "HackTool:Win32/Mimikatz",
"threat_status": "Quarantined",
"domain_user": "DESKTOP-O8964S4\\RaptorSniper",
"domain_user_group": "NT AUTHORITY\\SYSTEM",
"process_name": "C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe",
"initial_detection_time": "2025-01-28T16:44:51.243160+00:00",
"remediation": "2025-01-28T16:45:06.220888+00:00",
"ressources": [
"file C:\\Users\\RaptorSniper\\Downloads\\a.zip"
],
"misc": {
"ThreatTrackingSha256": "7accd179e8a6b2fc907e7e8d087c52a7f48084852724b03d25bebcada1acbca5",
"ThreatTrackingSigSeq": 24633990908277,
"ThreatTrackingId": "DC97D2FF-71EA-44A3-BED5-851EC71A1073",
"ThreatTrackingStartTime": 133825562912428260,
"ThreatTrackingThreatName": "HackTool:Win32/Mimikatz",
"ThreatTrackingSha1": "4112ef95386ea4d1131be7c600d49a310e9d8f5b",
"ThreatTrackingSigSha": "690c01740c8b5e15fb8f56402cdd51d18e31faac",
"ThreatTrackingSize": 1206166,
"ThreatTrackingMD5": "d2d3e1f8023b12fb89e400c7e8ecd7db",
"ThreatTrackingScanFlags": 17,
"ThreatTrackingIsEsuSig": false,
"ThreatTrackingThreatId": 2147686744,
"ThreatTrackingScanSource": 3,
"ThreatTrackingScanType": 0
}
}
The tool can also recursively parse a directory:
wddh -D samples
[21ms]__init__:74 | WARNING - Do not find expected type at offset 0x4. Expected : TLVTypeEnum.UINT64, Found : TLVTypeEnum.MISSING
[21ms]main:129 | WARNING - Fail to parse samples/search_threat_id/note.md : unpack requires a buffer of 8 bytes
[21ms]__init__:74 | WARNING - Do not find expected type at offset 0x4. Expected : TLVTypeEnum.UINT64, Found : TLVTypeEnum.MISSING
[21ms]main:129 | WARNING - Fail to parse samples/action_id/note.md : unpack requires a buffer of 8 bytes
[21ms]__init__:74 | WARNING - Do not find expected type at offset 0x4. Expected : TLVTypeEnum.UINT64, Found : TLVTypeEnum.MISSING
[21ms]main:129 | WARNING - Fail to parse samples/ts_modified/note.md : unpack requires a buffer of 8 bytes
{"header": {"threat_id": 2147686744, "detection_id": "94bbe9cf-cdeb-4885-9178-cc93fb10822d", "magic_version": "Magic.Version:1.2", "threat_name": "HackTool:Win32/Mimikatz"}, "flag_section": {"flag_1": 0, "flag_2": 4, "flag_3": 34, "flag_4": 87, "flag_5": 4, "threat_status_id": "ThreatStatusID.Quarantined", "flag_list_len": 3, "flag_list": [2, 3, 6], "alert_detail_count": 1}, "alert_details": [{"magic_version": "Magic.Version:1.2", "ressource_type": "file", "ressource_location": "C:\\Users\\RaptorSniper\\Downloads\\a.zip", "flag_1": 268435457, "blob_len": 1289, "blob": {"ThreatTrackingSha256": "7accd179e8a6b2fc907e7e8d087c52a7f48084852724b03d25bebcada1acbca5", "ThreatTrackingSigSeq": 24633990908277, "ThreatTrackingId": "DC97D2FF-71EA-44A3-BED5-851EC71A1073", "ThreatTrackingStartTime": 133825562912428256, "ThreatTrackingThreatName": "HackTool:Win32/Mimikatz", "ThreatTrackingSha1": "4112ef95386ea4d1131be7c600d49a310e9d8f5b", "ThreatTrackingSigSha": "690c01740c8b5e15fb8f56402cdd51d18e31faac", "ThreatTrackingSize": 1206166, "ThreatTrackingMD5": "d2d3e1f8023b12fb89e400c7e8ecd7db", "ThreatTrackingScanFlags": 17, "ThreatTrackingIsEsuSig": false, "ThreatTrackingThreatId": 2147686744, "ThreatTrackingScanSource": 3, "ThreatTrackingScanType": 0}}], "metadata": {"last_threat_status_change": "2025-01-28T16:45:06.220888+00:00", "threat_status_error_code": 0, "flag_1": 0, "unknown_uid": "80031958-0000-0000-862b-597c89800a50", "current_threat_execution_id": 1}, "optional": null, "metadata_2": {"flag_1": 2, "domain_user": "DESKTOP-O8964S4\\RaptorSniper", "flag_2": 3, "process_name": "C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe", "flag_3": 3, "flag_4": 1, "flag_5": 0, "initial_detection_time": "2025-01-28T16:44:51.243160+00:00", "flag_6": 0, "remediation": "2025-01-28T16:45:06.220888+00:00", "flag_7": 0, "unknown_1": "<L:4|T:0|V:b'\\x00\\x00\\x00\\x00'>", "flag_8": 0, "domain_user_group": "NT AUTHORITY\\SYSTEM", "flag_9": 0, "count_following_information_section": 0}, "alert_details_2": [], "footer": {"unknown_1": "<L:4|T:0|V:b'\\x00\\x00\\x00\\x00'>", "flag_1": 0, "flag_2": 0, "flag_3": 0, "flag_4": 1}}
{"header": {"threat_id": 2147686744, "detection_id": "94bbe9cf-cdeb-4885-9178-cc93fb10822d", "magic_version": "Magic.Version:1.2", "threat_name": "HackTool:Win32/Mimikatz"}, "flag_section": {"flag_1": 0, "flag_2": 4, "flag_3": 34, "flag_4": 87, "flag_5": 16, "threat_status_id": "ThreatStatusID.MISSING", "flag_list_len": 3, "flag_list": [2, 3, 6], "alert_detail_count": 1}, "alert_details": [{"magic_version": "Magic.Version:1.2", "ressource_type": "file", "ressource_location": "C:\\Users\\RaptorSniper\\Downloads\\a.zip", "flag_1": 268435457, "blob_len": 1289, "blob": {"ThreatTrackingSha256": "7accd179e8a6b2fc907e7e8d087c52a7f48084852724b03d25bebcada1acbca5", "ThreatTrackingSigSeq": 24633990908277, "ThreatTrackingId": "DC97D2FF-71EA-44A3-BED5-851EC71A1073", "ThreatTrackingStartTime": 133825562912428256, "ThreatTrackingThreatName": "HackTool:Win32/Mimikatz", "ThreatTrackingSha1": "4112ef95386ea4d1131be7c600d49a310e9d8f5b", "ThreatTrackingSigSha": "690c01740c8b5e15fb8f56402cdd51d18e31faac", "ThreatTrackingSize": 1206166, "ThreatTrackingMD5": "d2d3e1f8023b12fb89e400c7e8ecd7db", "ThreatTrackingScanFlags": 17, "ThreatTrackingIsEsuSig": false, "ThreatTrackingThreatId": 2147686744, "ThreatTrackingScanSource": 3, "ThreatTrackingScanType": 0}}], "metadata": {"last_threat_status_change": "2025-01-28T16:45:06.220888+00:00", "threat_status_error_code": 0, "flag_1": 0, "unknown_uid": "80031958-0000-0000-862b-597c89800a50", "current_threat_execution_id": 1}, "optional": null, "metadata_2": {"flag_1": 2, "domain_user": "DESKTOP-O8964S4\\RaptorSniper", "flag_2": 3, "process_name": "C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe", "flag_3": 3, "flag_4": 1, "flag_5": 0, "initial_detection_time": "2025-01-28T16:44:51.243160+00:00", "flag_6": 0, "remediation": "2025-01-28T16:45:06.220888+00:00", "flag_7": 0, "unknown_1": "<L:4|T:0|V:b'\\x00\\x00\\x00\\x00'>", "flag_8": 0, "domain_user_group": "NT AUTHORITY\\SYSTEM", "flag_9": 0, "count_following_information_section": 0}, "alert_details_2": [], "footer": {"unknown_1": "<L:4|T:0|V:b'\\x00\\x00\\x00\\x00'>", "flag_1": 0, "flag_2": 0, "flag_3": 0, "flag_4": 1}}
{"header": {"threat_id": 2147686744, "detection_id": "94bbe9cf-cdeb-4885-9178-cc93fb10822d", "magic_version": "Magic.Version:1.2", "threat_name": "HackTool:Win32/Mimikatz"}, "flag_section": {"flag_1": 0, "flag_2": 4, "flag_3": 34, "flag_4": 87, "flag_5": 4, "threat_status_id": "ThreatStatusID.Quarantined", "flag_list_len": 3, "flag_list": [2, 3, 6], "alert_detail_count": 1}, "alert_details": [{"magic_version": "Magic.Version:1.2", "ressource_type": "file", "ressource_location": "C:\\Users\\RaptorSniper\\Downloads\\a.zip", "flag_1": 268435457, "blob_len": 1289, "blob": {"ThreatTrackingSha256": "7accd179e8a6b2fc907e7e8d087c52a7f48084852724b03d25bebcada1acbca5", "ThreatTrackingSigSeq": 24633990908277, "ThreatTrackingId": "DC97D2FF-71EA-44A3-BED5-851EC71A1073", "ThreatTrackingStartTime": 133825562912428256, "ThreatTrackingThreatName": "HackTool:Win32/Mimikatz", "ThreatTrackingSha1": "4112ef95386ea4d1131be7c600d49a310e9d8f5b", "ThreatTrackingSigSha": "690c01740c8b5e15fb8f56402cdd51d18e31faac", "ThreatTrackingSize": 1206166, "ThreatTrackingMD5": "d2d3e1f8023b12fb89e400c7e8ecd7db", "ThreatTrackingScanFlags": 17, "ThreatTrackingIsEsuSig": false, "ThreatTrackingThreatId": 2147686744, "ThreatTrackingScanSource": 3, "ThreatTrackingScanType": 0}}], "metadata": {"last_threat_status_change": "2025-01-28T16:45:06.220888+00:00", "threat_status_error_code": 7, "flag_1": 0, "unknown_uid": "80031958-0000-0000-862b-597c89800a50", "current_threat_execution_id": 5}, "optional": null, "metadata_2": {"flag_1": 3, "domain_user": "DESKTOP-O8964S4\\RaptorSniper", "flag_2": 3, "process_name": "C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe", "flag_3": 3, "flag_4": 1, "flag_5": 0, "initial_detection_time": "2025-01-28T16:44:51.243160+00:00", "flag_6": 0, "remediation": "2025-01-28T16:45:06.220888+00:00", "flag_7": 0, "unknown_1": "<L:4|T:0|V:b'\\x00\\x00\\x00\\x00'>", "flag_8": 0, "domain_user_group": "NT AUTHORITY\\SYSTEM", "flag_9": 0, "count_following_information_section": 0}, "alert_details_2": [], "footer": {"unknown_1": "<L:4|T:0|V:b'\\x00\\x00\\x00\\x00'>", "flag_1": 0, "flag_2": 0, "flag_3": 0, "flag_4": 1}}
{"header": {"threat_id": 2147686744, "detection_id": "94bbe9cf-cdeb-4885-9178-cc93fb10822d", "magic_version": "Magic.Version:1.2", "threat_name": "HackTool:Win32/Mimikatz"}, "flag_section": {"flag_1": 0, "flag_2": 4, "flag_3": 34, "flag_4": 87, "flag_5": 4, "threat_status_id": "ThreatStatusID.Quarantined", "flag_list_len": 3, "flag_list": [2, 3, 6], "alert_detail_count": 1}, "alert_details": [{"magic_version": "Magic.Version:1.2", "ressource_type": "file", "ressource_location": "C:\\Users\\RaptorSniper\\Downloads\\a.zip", "flag_1": 268435457, "blob_len": 1289, "blob": {"ThreatTrackingSha256": "7accd179e8a6b2fc907e7e8d087c52a7f48084852724b03d25bebcada1acbca5", "ThreatTrackingSigSeq": 24633990908277, "ThreatTrackingId": "DC97D2FF-71EA-44A3-BED5-851EC71A1073", "ThreatTrackingStartTime": 133825562912428256, "ThreatTrackingThreatName": "HackTool:Win32/Mimikatz", "ThreatTrackingSha1": "4112ef95386ea4d1131be7c600d49a310e9d8f5b", "ThreatTrackingSigSha": "690c01740c8b5e15fb8f56402cdd51d18e31faac", "ThreatTrackingSize": 1206166, "ThreatTrackingMD5": "d2d3e1f8023b12fb89e400c7e8ecd7db", "ThreatTrackingScanFlags": 17, "ThreatTrackingIsEsuSig": false, "ThreatTrackingThreatId": 2147686744, "ThreatTrackingScanSource": 3, "ThreatTrackingScanType": 0}}], "metadata": {"last_threat_status_change": "2025-01-28T16:45:06.220888+00:00", "threat_status_error_code": 0, "flag_1": 0, "unknown_uid": "80031958-0000-0000-862b-597c89800a50", "current_threat_execution_id": 1}, "optional": null, "metadata_2": {"flag_1": 2, "domain_user": "DESKTOP-O8964S4\\RaptorSniper", "flag_2": 3, "process_name": "C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe", "flag_3": 3, "flag_4": 1, "flag_5": 0, "initial_detection_time": "2025-01-28T16:44:51.243160+00:00", "flag_6": 0, "remediation": "2025-01-28T16:52:16.241905+00:00", "flag_7": 0, "unknown_1": "<L:4|T:0|V:b'\\x00\\x00\\x00\\x00'>", "flag_8": 0, "domain_user_group": "NT AUTHORITY\\SYSTEM", "flag_9": 0, "count_following_information_section": 0}, "alert_details_2": [], "footer": {"unknown_1": "<L:4|T:0|V:b'\\x00\\x00\\x00\\x00'>", "flag_1": 0, "flag_2": 0, "flag_3": 0, "flag_4": 1}}
This research allows to confirm what was already identified in the dtformat documentation, as well as confirming some field affectation and identifying some edge case notes previously documented.
A standalone tool, allowing to process this artifact outside of plaso was also developed. It can be found on GitHub (https://github.com/cert-orangecyberdefense/wddh-parser) as well as on pypi (https://pypi.org/project/wddh/). Code was tested under Windows and Linux environments, but as being pure Python it should work on all platforms. Don’t hesitate to test it and open an issue if you encounter any problems!
Plaso artifact parser and libyal documentation regarding data format:
https://github.com/log2timeline/plaso/blob/main/plaso/parsers/windefender_history.py
https://github.com/libyal/dtformats/blob/main/documentation/Windows Defender scan DetectionHistory file format.asciidoc
Previous work on this topic:
https://github.com/jklepsercyber/defender-detectionhistory-parser
https://www.sans.org/blog/uncovering-windows-defender-real-time-protection-history-with-dhparser/
Some artifacts sample: https://github.com/AndrewRathbun/DFIRArtifactMuseum

30 June 2025

28 April 2023

30 May 2024

23 January 2024