
1 June 2021
Today, companies have to manage a new type of organization that is both a hybrid and extended one.
Digital transformation has accelerated in the form of; a growing hybrid workforce, continued migration to the cloud, and the transformation of security operations. The strategic business decisions, such as opening new channels, mergers and acquisitions, or using new suppliers, are adding complexity with new systems that need to be integrated and, new users wanting access to data..
Companies do not have the resources and skills internally to keep up with ever‑changing environments and protect them.
Watch our webinar
At a strategic level, learn how to define your Zero Trust posture referring to your context and needs.
At a tactical level, rely on technologies, such as encryption, multifactor authentication, identity and, access management together with governance processes to apply our tactical mode. In the end, make your zero trust model operational by monitoring it.
The combination of these 3 levels, driven by intelligence, ensures the Zero Trust architecture is managed and remains adaptive to the latest threats.
Read our White Paper on Zero Trust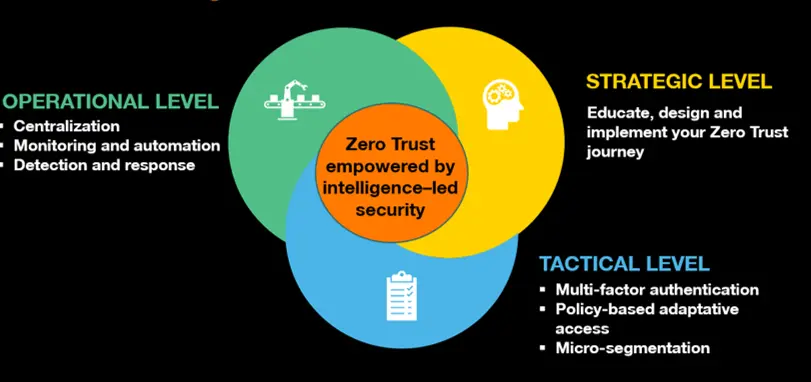
Build a reliable and consistent experience based on your needs and those of your users
Secure access by streamlining least-privileged access controls across distributed hybrid environments
Reduce potential breaches and responding quickly, mitigating their impact
