Our solutions in detail
The digital transformation is changing business
and cybersecurity is a key enabler to succeed
Operational Technology (OT) is everywhere around us and the digital revolution progresses across all industries. Especially in production, OT systems were traditionally thought to be “protected” by an air-gap separating them from the highly connected (and thus highly vulnerable) IT-world.
This is no longer the case as IT/OT convergence, which has already progressed for quite a while, was accelerated by the increasing use of IT technologies in industrial systems. This fusion brings with it a completely new world of benefits, efficiency, and flexibility. But it also opens plants, shop floors, production facilities and vital infrastructure to the darker world of traditional IT threats.
Learn more about OT security

Securing the digital transformation of your business is a serious matter
Let us help you, so you can focus on making the right decisions.
With proper security mechanisms implemented for industrial networks, organizations can increase their competitive edge and benefit from the efficiencies when interconnecting environments. Effective OT security protects business-critical processes, systems and people, and reduces security vulnerabilities and incidents.
Orange Cyberdefense works with customers in many different industries, with similar challenges related to the use of industrial control systems, SCADA environments, health and medical equipment, etc. Many challenges are the same, and security solutions must be applied across OT and IT environments to enable efficient operations and management. Our Industrial Security Services are designed to meet all compliance requirements with regulations such as standards such as NIST 800, IEC 62443, NIS 2.
Setting the right priorities for you is business-critical for us
Understand your environment
Extending your security program to OT environments starts with understanding your assets, networks, threat landscape and attack surface.
Protect your networks and assets
Increasing connectivity of IT and OT requires secure network design and segmentation to protect and access assets in your network.
Detect complex threats
Detecting complex threats in increasingly connected IT and OT environments requires integrated threat detection capabilities.
Prepare for security incidents
Being prepared for security incidents gives you the best chance of minimizing the impact.
Our OT security approach is powered by our dedicated OT teams and intelligence-led services.
So you can:
- Build a risk-based OT security program with embedded threat intelligence
- Securely connect your IT and OT networks and protect assets from evolving complex threats
- Detect threats in your IT and OT networks and build integrated response capabilities
- Be prepared for security incidents with the right specialists on hand to respond
- Meet all compliance checks with standards such as NIST 800, IEC 62443, NIS 2

Secure your OT systems for NIS2
The NIS2 Directive extends beyond traditional IT security—it directly impacts OT environments that power critical industries. With industrial systems increasingly connected to corporate networks and cloud services, the attack surface has expanded, making OT a prime target for cyber threats.
To comply with NIS2, it is important that organizations harden their OT security, enhance visibility, and adopt proactive cyber resilience measures. But achieving compliance doesn’t have to be a burden—it can be a catalyst for stronger security, greater operational resilience, and a true competitive advantage. With the right strategy, NIS2 can be an opportunity to future-proof your OT environment while staying ahead of evolving cyber threats.
Why we can help you
A strong partner to face the security challenge
Support
Dedicated support according to your activity sector in order to set up a strategic, integrated security approach.
Skills
Dedicated OT security specialists and specialized OT managed security service delivery teams.
Presence
A worldwide presence allows us to support you wherever you are and at any given time 24/7/365.
Experience
Cross-industry experience and know-how of industry standards, enhanced by strong partnerships with market leading OT security vendors.
Together with Orange Business, we help you transform your industrial security & digital operations
We partner up with Orange Business to deliver the best levels of service, so you can transform your industrial operations and secure all you industrial environments from existing threats all at once.
Tell me more

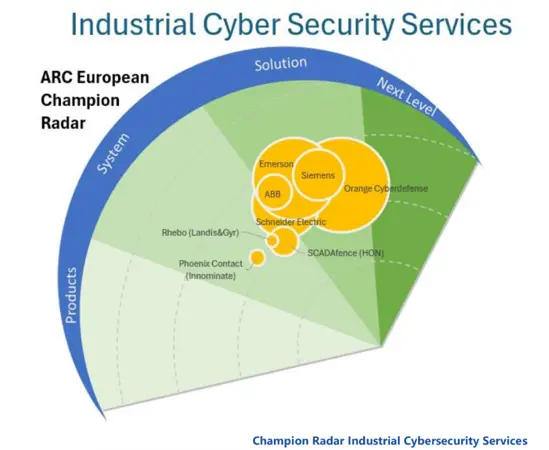
Orange Cyberdefense is recognized as leader in Industrial Cybersecurity Services
We are proud to share that ARC Advisory Group has positioned Orange Cyberdefense as the top-ranked provider in the 2025 ARC European Champion Radar for Industrial Cybersecurity Services.
ARC’s independent evaluation confirms that Orange Cyberdefense not only delivers robust solutions but also brings vision, expertise, and innovation that set us apart in the market.
Learn more