
7 February 2022
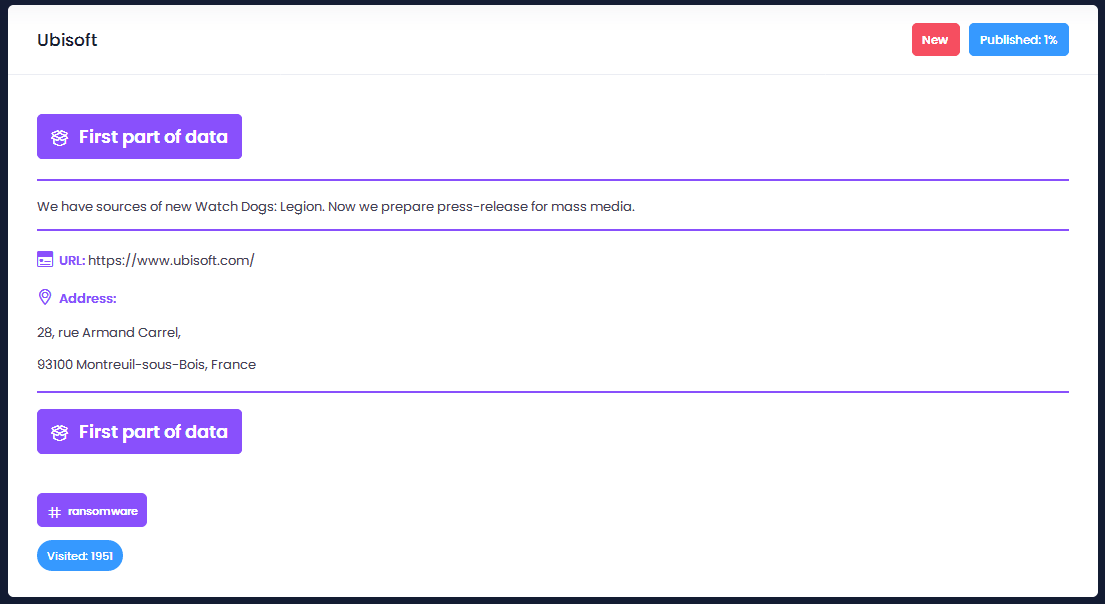
As announced in the press on October 16th, “the Egregor ransomware game posted archives containing unencrypted files, stating that they were stolen from Ubisoft and Crytek in unrelated attacks. While it has not been confirmed if the attack against Ubisoft is legitimate, BleepingComputer has confirmed that Crytek suffered a ransomware attack.”
Source : Ubisoft
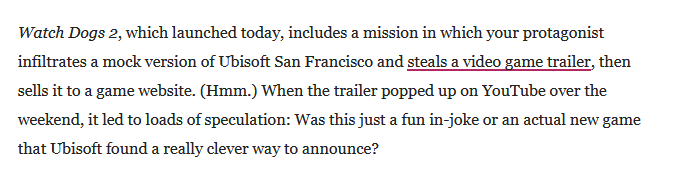
This video game, hacking themed, is scheduled for a release next week, on October 29. Note that the previous opus of the game, Watch Dogs 2, included a mission where the player had to hack Ubisoft to steal a trailer:
Source: https://kotaku.com/sources-ubisofts-watch-dogs-2-teaser-is-a-real-sci-fi-1788999298
Based on currently known information, it is not possible to state this with certainty. Hackers have effectively reported hacking Ubisoft.
Source: Egregor website
However, they do not claim to have encrypted the computer system but to have stolen the source code of the Watch Dogs: Legion video game. It would have been more logical for Egregor to have broken down Ubisoft’s infrastructure, especially if the group had been able to obtain direct access to the development platform. This would have made it possible to incite payment of the ransom rather than just talking about theft (as if it had been obtained indirectly). On this subject, the evidence provided to date are not sufficient (and even recent enough) to prove that they do hold the full source code content.
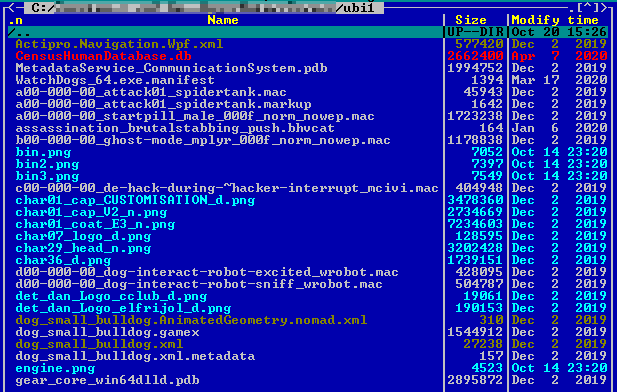
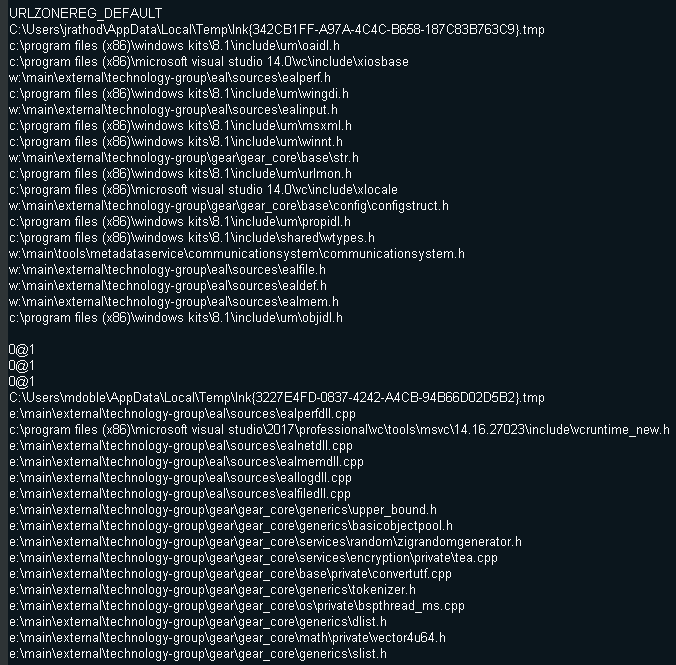
Source: Egregor website
Similarly, the theft of other elements and source codes would have been logical. We’ll have to wait for an official Ubisoft press release to find out what’s going on. In the financial markets, the announcement has in any case not currently given rise to any major movements that could suggest panic, both in public and behind the scenes, on the part of shareholders.

Source: Euronext Paris, October 19, 2020
If this attack is real, it could have been carried out in various ways, such as exploiting an external vulnerability to penetrate the network. It could also be the exploitation of an internal vulnerability, via a user or a partner whose computer or account has been compromised.
As the park has not been encrypted (according to initial information), there is no immediate risk to the continuity of the project. It is mainly a question of image. Ubisoft must also assess the potential risks related to the content of the data that may have leaked (especially if it relates to something other than pure source code). It is conceivable that the source code if it has been stolen and is up to date, could be studied by hackers to find ways to cheat or exploit the game maliciously. Note that this is already possible for most video games, with or without the source code.
This information has not been communicated to our knowledge.
In the event of such a crisis, two priorities come to mind:
– Manage the technical side to understand what potentially happened and ensure that there are no internal threats (malware, abuse of access to services and privileged accounts, the security of certain elements shared with partners).
– Manage the communication around the investigation to be transparent to the public and shareholders and to demonstrate the seriousness of the company even in the face of real or presumed difficulties.
The group is known at Orange Cyberdefense and in general on the OSINT* community.
It shares some technical aspects suggesting a relationship with another group, also operating with ransomware, named Sekhmet. The Sekhmet team presents itself as follow:

Source: Sekhmet website
Egregor seems more incisive in his communications as his victims are referenced on a “hall of shame”.
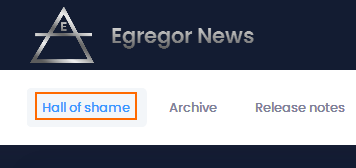
Source: Egregor website
Egregor has a habit of leaving a very short reaction time to its victims, about 3 days, with this type of message:
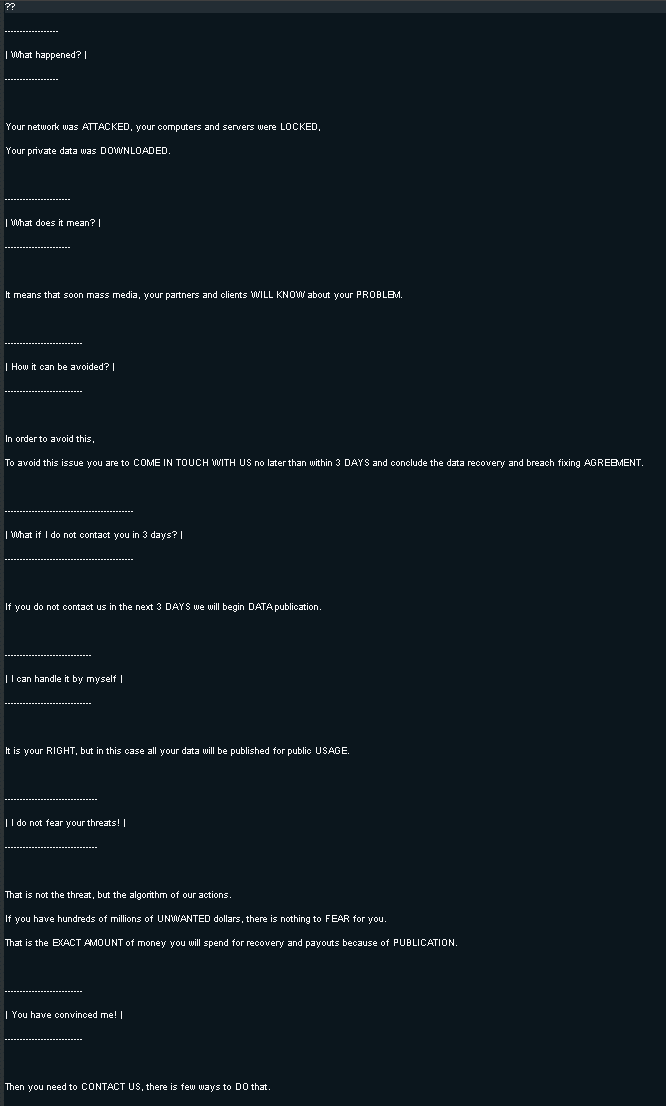
Source: OSINT
Egregor samples are activated via a specific command that sandboxes and other analysis systems cannot know unless it is entered manually. It’s a bit like a password needed to activate the malware command. These samples are therefore created to be triggered and mastered by a hacker only.
However, analysis markers are known on the current samples** but do not guarantee accuracy and durability because they are easily modified by hackers.
Source: Orange Cyberdefense, Epidemiology Lab
Here is the chain of action generally observed:
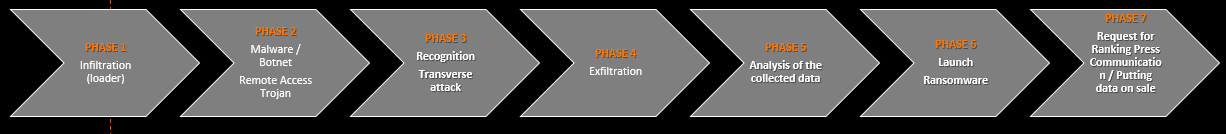
Source: Orange Cyberdefense, Epidemiology Lab
Here are some additional statistics about Egregor:
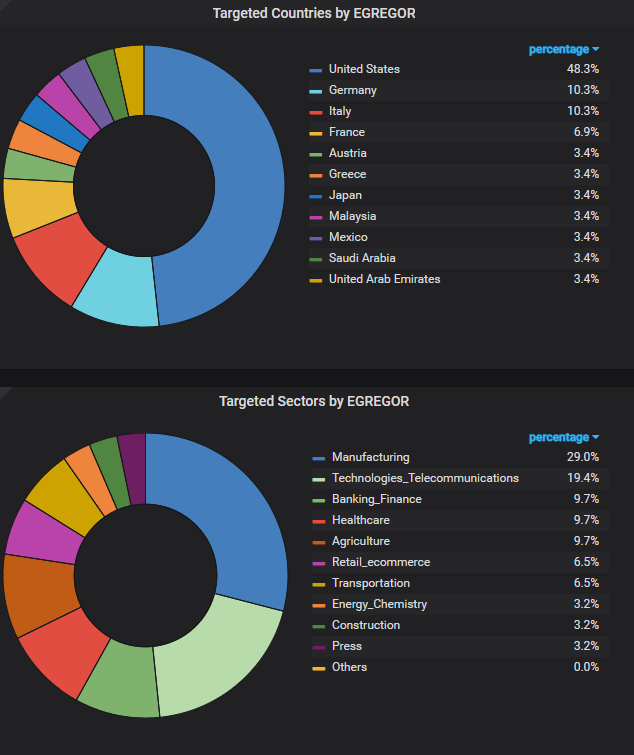
Source: Orange Cyberdefense, Epidemiology Lab
As soon as we have new information on this potential attack, we will not fail to keep you informed.
To discover the Epidemiology Lab’s analyses, click here.
Notes:
*Open Source Intelligence
**Usable for automated systems