
Master your risks and ensure business continuity.

When we published our findings on Hacktivism: Victims and Impact in 2023 in our Security Navigator 2024, hacktivism was already undergoing a visible resurgence. At the time, most of the incidents we observed were not technically destructive at scale in the conventional sense. What stood out were the broader structural trends emerging across the threat landscape. Hacktivism was becoming more frequent, more coordinated, and increasingly entangled with real-world geopolitical events.
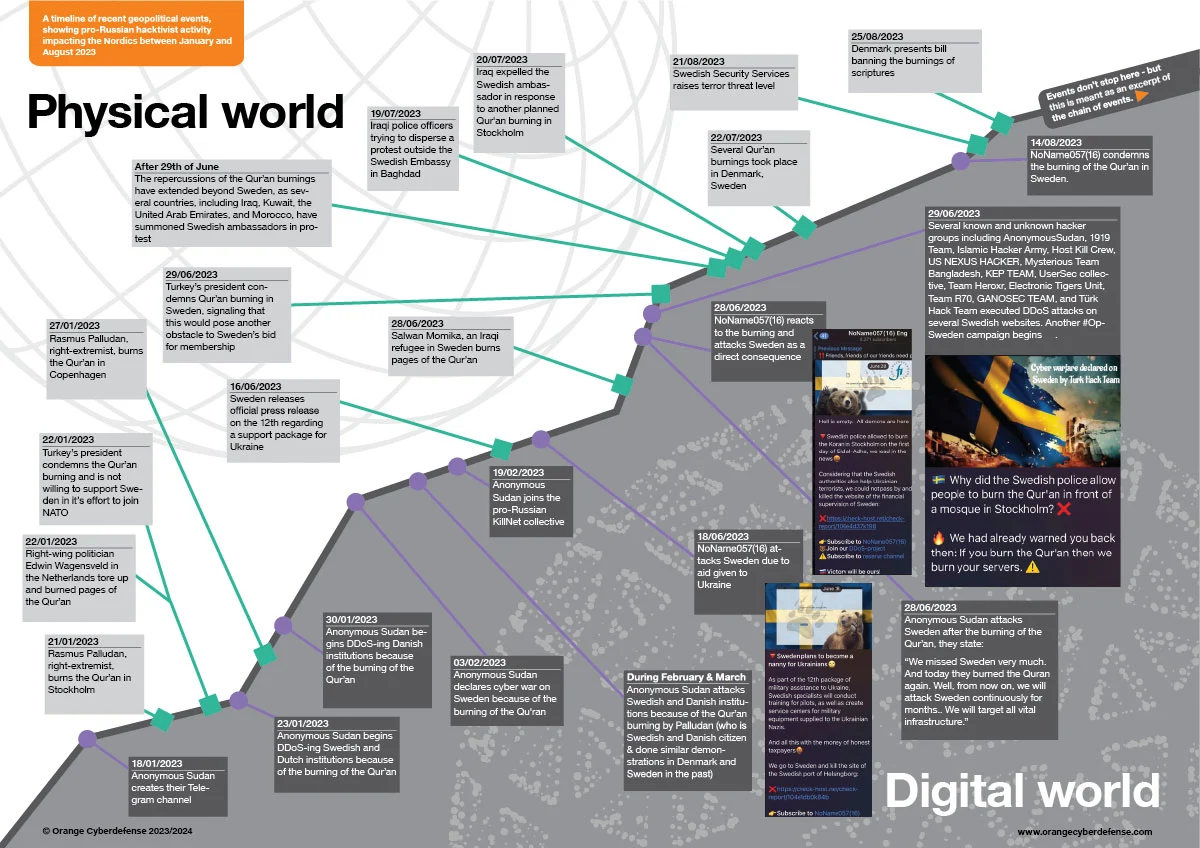
We visualized this observation in a timeline overview back in 2023 on the example of the entanglement of physical and cyber events in the Nordics. In hindsight, we realized that this is a global phenomenon, observable in several regions of the world.
Looking back from today’s perspective, these observations remain highly relevant. Moving on, our research published one year later in the Security Navigator 2025, under the headline Exploring the Intersection of Cyber Activism and State-sponsored Operations provides an essential conceptual expansion: hacktivism can no longer be understood purely as activism or digital protest. Instead, it is increasingly positioned at the intersection of cybercrime, influence operations, and even state-aligned hybrid conflict.
Since 2022 but especially in 2023, we observed two significant trends shaping hacktivists’ activity. First, hacktivism surged dramatically in volume. Second, individual groups began to join larger collectives, enabling them to draw upon shared resources, tools, and visibility. Campaign-style operations such as #OpSweden, #OpFrance, and #OpAustralia illustrated how hacktivism was evolving beyond isolated incidents into coordinated, networked efforts. In 2024, we started tracking some of these networks, illustrating these campaigns and which countries were impacted by different hacktivist groups. This was a view on one of the most active pro-Russian hacktivist groups and how they form ‘alliances’ with other groups to then impact certain countries in joint campaigns, as can be seen below.
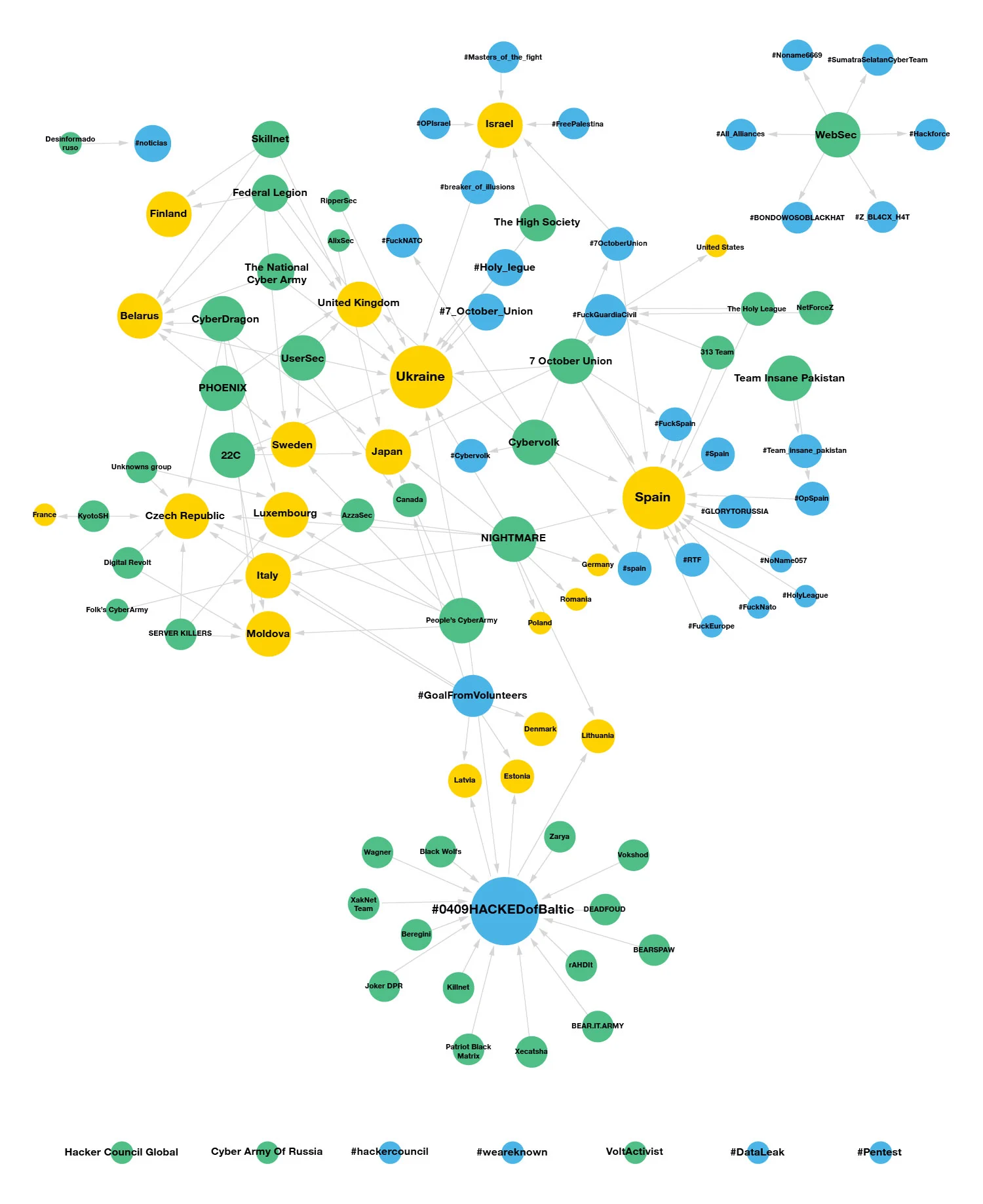
These campaigns disproportionately affected sectors such as government, telecommunications, energy, and media, not necessarily because these sectors were always the most technically vulnerable, but because they represent the symbolic infrastructure of modern societies. Even at that stage, it was clear that hacktivism’s impact extended beyond immediate disruption: its victims were often selected for what they represented politically and socially. This insight is reinforced strongly in the 2025 publication, which emphasizes that in modern hacktivism, victimhood is frequently more symbolic than operational. Attacks against everyday services such as banking systems or public transport are designed to highlight institutional vulnerability and reinforce narratives of state failure.
In this sense, the target matters less for its technical value than for its societal meaning.
An additional factor is the role of the media ecosystem in amplifying hacktivist messaging. By reproducing threat actor narratives, media coverage may contribute to heightened public anxiety, erosion of institutional trust, and distorted perceptions of systemic vulnerabilities. In doing so, sensationalized reporting can unintentionally function as part of the broader amplification mechanism on which these actors thrive. This effect is further reinforced when threat actors are repeatedly named and branded, as many actively monitor media coverage and leverage such visibility to validate, amplify, and sustain their campaigns.
In our 2025 report, we introduce a historical framing of hacktivism as an evolving phenomenon across three distinct eras. The first, the Digital Utopia Era, emerged in the 1980s and 1990s, shaped by early hacker ethics and ideals of building a better internet, exemplified by groups such as the Chaos Computer Club. The second, the Anti-Establishment Era, was characterized by movements such as Anonymous, which positioned themselves against governments, corporations, and entrenched power structures. The third and current phase, however, is what we describe as the Establishment Era. In this era, hacktivist groups increasingly align themselves with nation-states, political establishments, or broader geopolitical agendas. Traditional hacktivism, which is grounded in resisting authority, becomes overshadowed by state-aligned cyber activities that begin to resemble cyber operations or warfare rather than protest.
This shift represents a fundamental transformation: hacktivism is no longer only oppositional. It is, in many cases, supportive of state objectives.
Already in 2024, we argued that hacktivism’s true impact often lies not in technical damage, but in its psychological and societal consequences. Hacktivist activity was increasingly interconnected with real-world events, creating cycles of escalation in which physical conflict triggers cyber retaliation, and cyber disruption fuels further tension. The 2025 research builds upon this by highlighting that modern hacktivism is increasingly oriented toward shaping public opinion through fear, uncertainty, doubt, and manipulation. The aim is less about service disruption and more about influence: destabilizing trust in institutions, amplifying societal division, and eroding democratic confidence. This is particularly visible in the growing overlap between hacktivism and disinformation, where cyberattacks are paired with narrative construction on platforms such as Telegram.
A particularly significant development highlighted in our Security Navigator 2025 publication is the targeting of democratic processes. With more than 50 countries holding elections in 2024, the report identified elections as ripe conditions for influence operations.
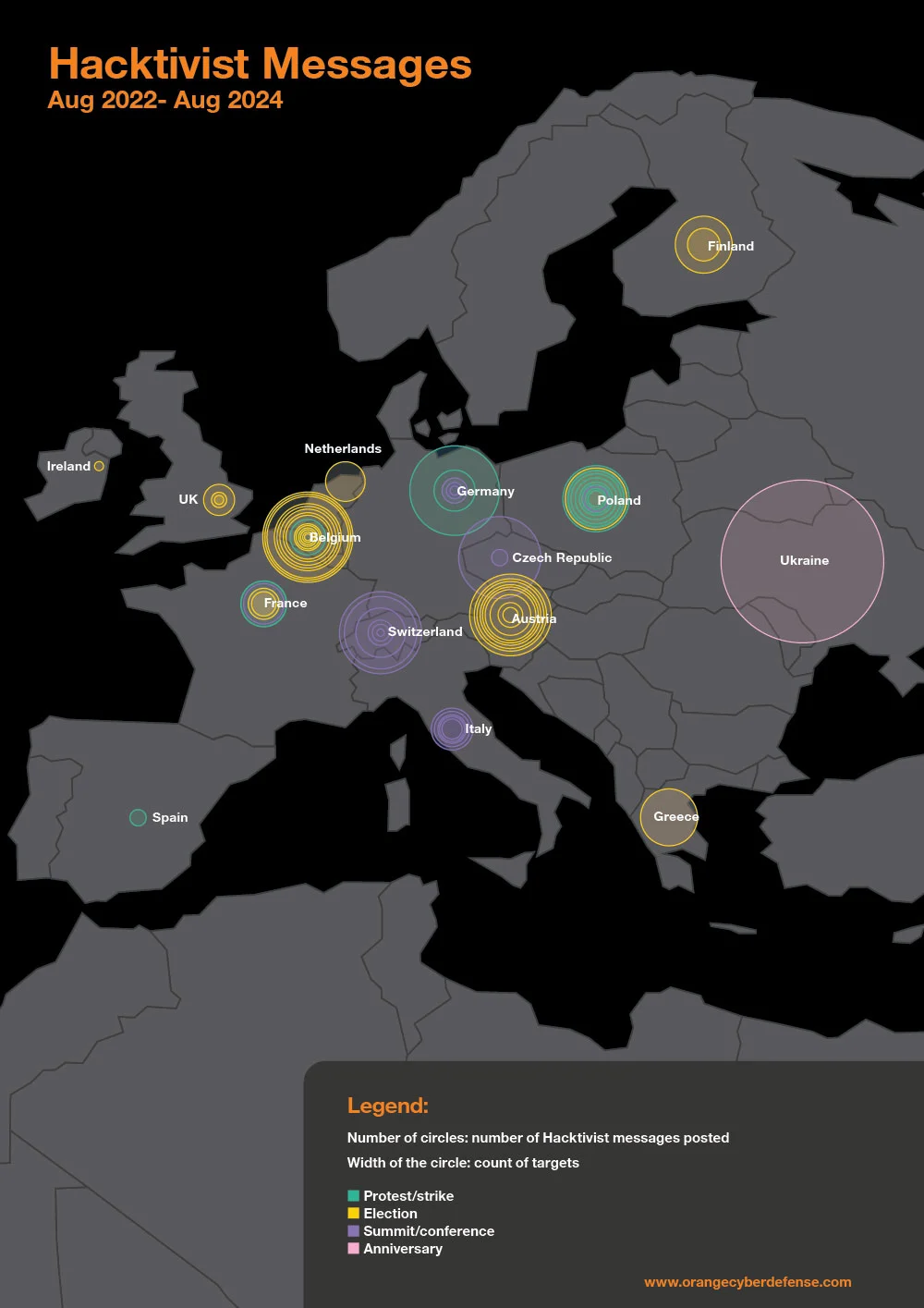
Hacktivist attacks increasingly focused on election-related portals and symbolic democratic institutions, aiming not merely to disrupt access, but to undermine public trust in electoral legitimacy. Election interference represented an escalation beyond traditional hacktivist disruption: it directly targets the foundations of democratic governance. Voting systems in countries including France, Finland, Belgium, Austria, and the United Kingdom were attacked during election periods in 2024, threatening integrity and sowing doubt about outcomes. This we continued to observe in 2025.
Another key finding of the 2025 research was the convergence of hacktivist operations. Modern hacktivists increasingly leveraged DDoS-for-hire services, crowdsourced attack tools, cryptocurrency incentives, and extortion-like coercion techniques. This represents a departure from earlier ideologically driven activism and illustrates how the cybercrime economy has reshaped hacktivism’s operational model.
Hacktivism, in this sense, is no longer easily distinguishable from proxy conflict or politically tolerated cybercrime. Which brings us to the topic of a really important question. Does what we are observing today still fit within traditional definitions of cyber activism / hacktivism, or are we witnessing something distinct?
In a recent research we conducted, we note that many contemporary campaigns extend far beyond the repertoire and ethos historically associated with hacktivism. To help clarify this ambiguity, the paper proposes a spectrum-based framework that situates operations along continuous dimensions of impact, alignment with state-level objectives, and host state involvement. Rather than insisting on fixed category labels, the spectrum approach acknowledges the heterogeneous nature of these activities and offers a more nuanced basis for distinguishing between civil cyber activism (hacktivism), hybrid proxy operations, escalation-driven cyber actions or just ‘good old’ cybercrime activities. It maps operations along two intersecting dimensions: the degree of alignment with state objectives (ranging from opposed to increasingly influenced, tolerated, supported, or controlled), and the level of impact, moving outward from nuisance activity toward disruption, destabilization, and potential harm.
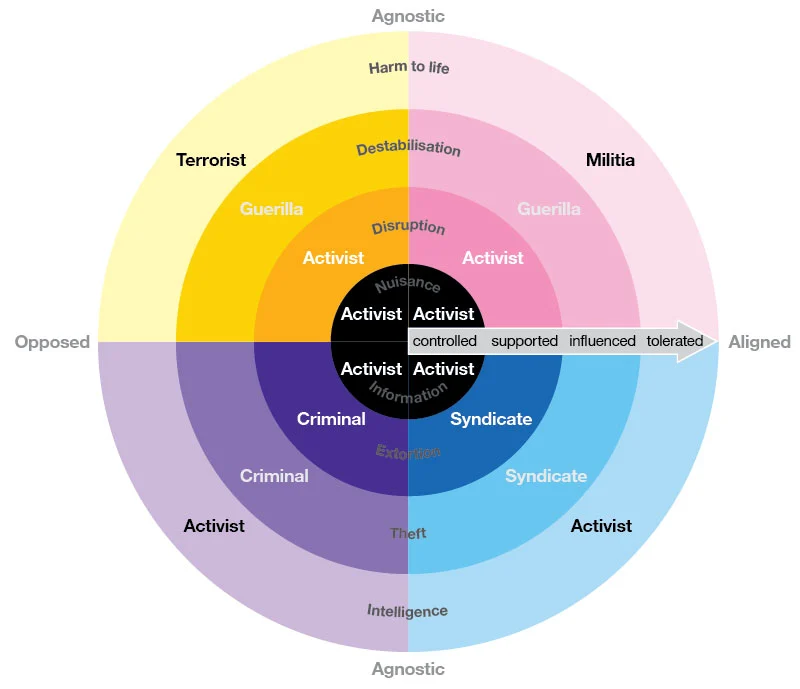
Viewed through this lens, the term hacktivism itself becomes less a clear category and more a contested label, one that can obscure deeper strategic alignment. For this reason, the remainder of this discussion refers to much of what we observe today as so-called hacktivism.
Additionally, we are tracking individual groups that fit the wider spectrum so to say, to understand their motivations, alliances and thus their actual nature. You can find our analyses on our website.
Taken together, our findings suggest a clear trajectory. So called hacktivism today is not merely digital protest. It has become an embedded feature of modern hybrid conflict, increasingly aligned with state narratives, amplified through collective ecosystems, media and oriented toward societal destabilization rather than technical disruption alone. Its victims are not only servers or websites, but public trust, democratic legitimacy, and the perceived stability of institutions. Defending against so called hacktivism therefore requires more than technical mitigation. It demands strategic resilience: protecting information integrity, countering manipulative narratives, and maintaining societal confidence in the face of politically motivated cyber disruption.
While our earlier work highlighted the shift of hacktivism into the Establishment Era, marked by increasing geopolitical alignment, narrative-driven targeting, and the convergence of disruption with influence; the Security Navigator 2026 suggests that this trajectory is continuing into a more escalatory phase. The so called hacktivism is no longer evolving only in terms of coordination or messaging, but increasingly in terms of risk domain: from primarily digital disruption toward scenarios with tangible cyber-physical implications.
Our latest findings indicate that although many operations still remain low-impact at the technical level in 2025, actors are showing growing familiarity with industrial and operational technology environments. Incidents involving unauthorized access or manipulation attempts in sectors such as water management, energy systems, and agriculture illustrate how the symbolic reach into critical infrastructure is becoming part of the threat repertoire. Even when damage is limited or contained, the ability to demonstrate access to such systems carries significant psychological and societal weight.
At the same time, the 2026 report reinforces that the core objective is increasingly cognitive rather than purely technical. Breach claims, verified or not, are rapidly amplified through media ecosystems and social platforms, turning disruption into spectacles.
Finally, our newest research highlights a growing strategic challenge for defenders and policymakers: traditional deterrence frameworks remain poorly suited to decentralized, volunteer-based ecosystems that can regenerate faster than institutional responses can adapt. Even successful disruption efforts demonstrate the limits of conventional enforcement and sanction-based approaches when actors perceive themselves as ideologically or patriotically motivated rather than criminally opportunistic.
Taken together, the Security Navigator 2026 offers an early indication that the so called hacktivism is entering a phase where the stakes extend beyond visibility and disruption, toward a more complex intersection of cyber-physical risk, cognitive influence, and societal resilience. In this evolving landscape, the question is no longer simply how to keep systems online, but how to defend the institutional coherence and public trust that such systems ultimately support.
Read the latest report including some of the most recent observation on hacktivism-like cyber activity and many other cyber security trends, here: https://www.orangecyberdefense.com/global/security-navigator