Tracking the Fight Against Cybercrime: Global Law Enforcement Trends and What They Reveal About Today’s Threat Landscape


Diana Selck-Paulsson
Senior Security Researcher

Zohra Hamila
Junior Security Researcher
Introduction
For organizations navigating an increasingly complex cyber threat landscape, insight into how cybercrime is investigated, disrupted, and prosecuted provides an important perspective on evolving risk and adversary behavior.
Cybercrime continues to grow in scale, sophistication, and diversification, placing sustained pressure on law enforcement agencies worldwide. In response, authorities have increased the visibility and frequency of arrests, takedowns, sanctions, and coordinated international operations. Despite this, publicly available information on law enforcement actions remains fragmented across jurisdictions, agencies, and individual case announcements. As a result, it has been difficult to form a coherent global picture of how cybercrime is being addressed, which criminal activities are prioritized, and who the offenders actually are.
This blog post summarizes findings from a systematically constructed dataset of 418 publicly announced law enforcement actions carried out between 2021 and mid-2025. This dataset is currently one of the most comprehensive and offers a rare consolidated view into global cybercrime enforcement and provides insights into trends in criminal activity, enforcement strategies, international collaboration, and offender characteristics.
About the dataset
The dataset is based exclusively on publicly reported law enforcement actions collected and verified by Orange Cyberdefense intelligence teams. Each entry represents a confirmed law enforcement activity, enriched through manual analysis to include contextual details such as the type of criminal act addressed, the form of law enforcement response, participating countries and institutions, and available offender demographics. While the dataset does not capture the full scope of cybercrime activity, it provides an empirical overview of visible enforcement efforts and allows for comparative analysis over time.
Limitations: Like all open-source datasets, this one has inherent limitations. It captures only publicly reported actions, reflecting the subset of offenders who have been identified, apprehended, or disrupted, rather than the full spectrum of cybercriminal activity. Furthermore, not all announcements include complete demographic information; age, gender, or nationality are sometimes unavailable.
From cybercrime to response: A growing global law enforcement effort
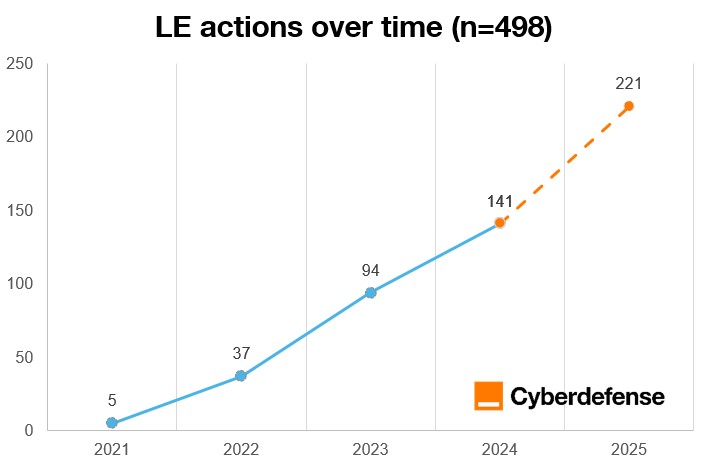
As shown in Figure 1, publicly reported law enforcement actions targeting cybercrime have increased steadily each year from 2021 onward. This upward trend reflects both the growing scale of cybercrime and an increased willingness by authorities to publicize enforcement efforts. By July 2025, the number of announced actions had already matched the total recorded for all of 2024, indicating that 2025 is likely to become the most active year on record once data collection is complete1.
Figure 1: Law Enforcement (LE) activities over time
This rise suggests not only increased attention to intensifying criminal activity but also improved international cooperation, potentially stronger investigative capabilities, and a strategic emphasis on deterrence through public attribution.
Which criminal acts are being addressed?
Figure 2 illustrates the ten most frequently addressed criminal acts. Cyber extortion, including ransomware, emerges as the most successful addressed offense. This is followed closely by malware distribution and unauthorized access or intrusion. Together, these categories dominate law enforcement activity and highlight how financially motivated cybercrime is addressed most.
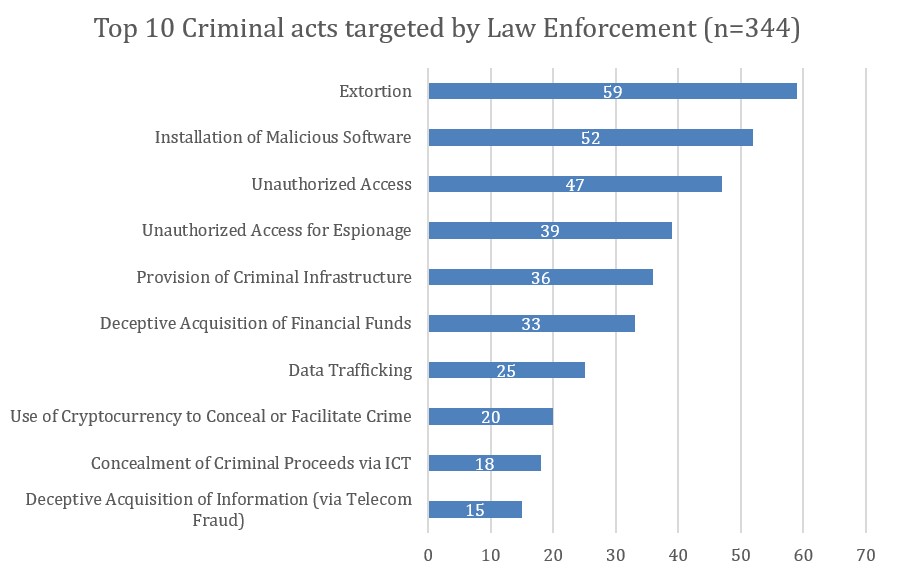
Figure2: Top 10 Criminal Acts targeted by Law Enforcement
Beyond direct financial exploitation, authorities are also increasingly targeting the infrastructure that enables cybercrime. Criminal acts such as cyber espionage, operation of dark web marketplaces, and provision of hosting or technical services to criminal networks appear frequently in the dataset. Less common but strategically important actions address data trafficking, cryptocurrency misuse, and money laundering, reflecting growing awareness of the financial and logistical ecosystems that sustain cyber operations.
The data also illustrates that motivations behind cybercrime are not static. While financial gain remains central, activities have evidently been shifting for example in response to geopolitical developments, blurring the lines between criminal, political, and ideological objectives.
What actions do law enforcement agencies take?
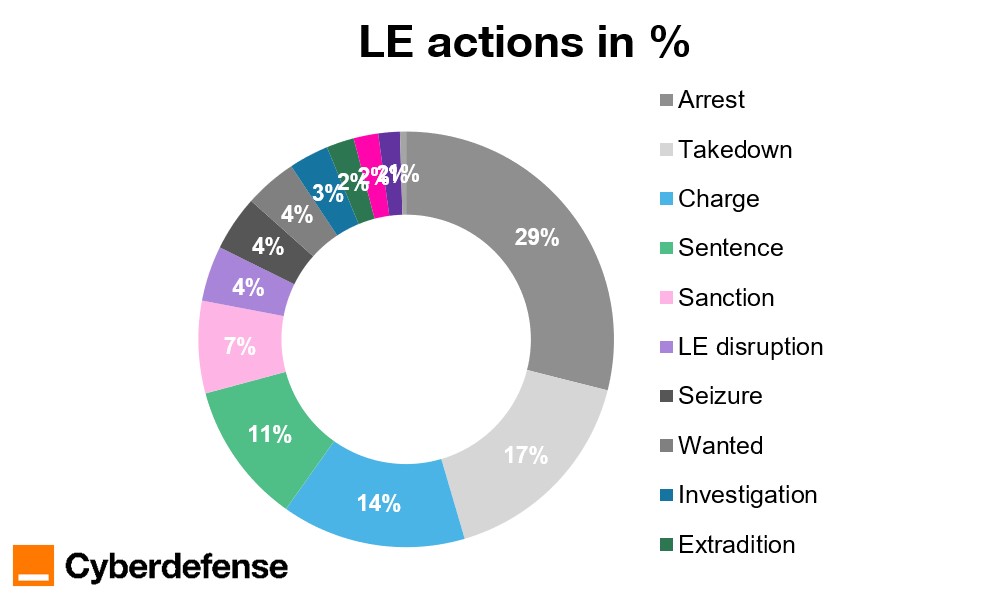
As shown in Figure 3, arrests represent the most common form of law enforcement response, accounting for 29 percent of all recorded actions. Arrests signal a continued emphasis on individual accountability and judicial outcomes. Takedowns and formal charges follow closely, together demonstrating both, disrupting active criminal infrastructure while advancing cases through legal systems.
Figure 3: All Law Enforcement actions in percentage
Additional measures such as sentencing, sanctions, and asset seizures indicate that law enforcement increasingly targets both individuals and the economic foundations of cybercrime. Sanctions, in particular, have grown steadily over time and reflect the expanding role of economic and diplomatic tools within cybercrime enforcement.
Figure 4 combines criminal acts with law enforcement responses and shows that arrests dominate across nearly all crime categories, especially cyber extortion and hacking. Takedowns are strongly associated with dark web marketplaces and malware infrastructure, while sanctions appear primarily in cases related to cyber espionage and state aligned activity.
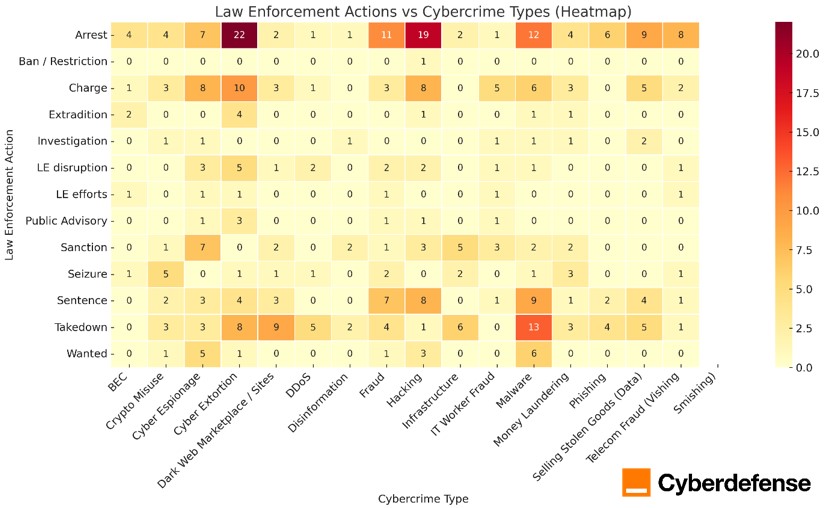
Figure 4: Law Enforcement Actions vs Cybercrime Types
Which countries lead cybercrime disruption?
Figure 5 highlights the leading countries involved in cybercrime enforcement. The United States stands out as the most active participant, acting as the primary lead in 45 percent of all recorded actions. A second cluster consisting of Germany, the United Kingdom, Russia, Ukraine, the Netherlands, Spain, and France forms the core of global cyber enforcement capacity outside the United States.
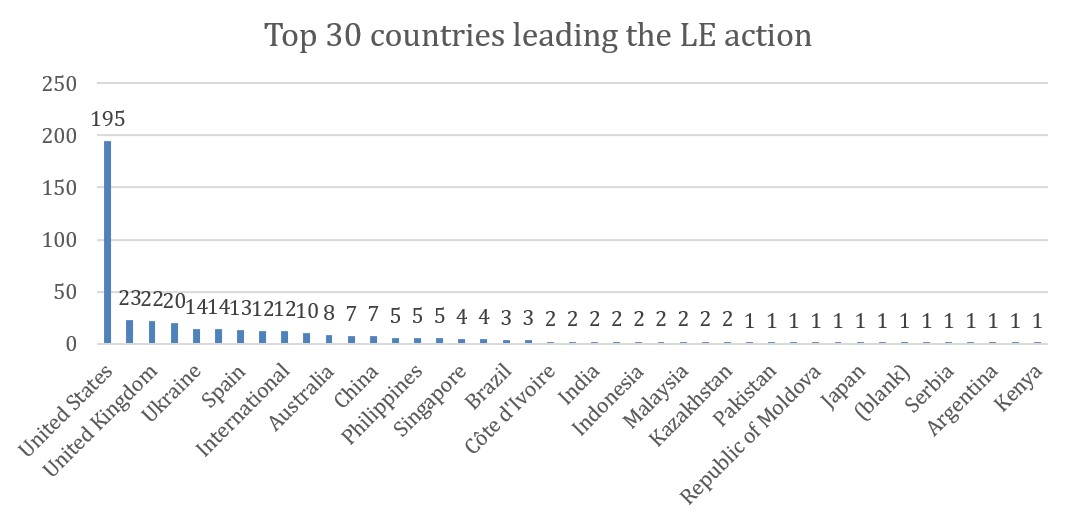
Figure 5: Top 30 countries leading the Law Enforcement actions
The presence of both Western and Eastern European states among leading actors reflects the complex geopolitical environment in which cybercrime enforcement operates. Many of these countries are simultaneously targets, sources, and enforcers within the global cybercrime ecosystem.
The Collaborative Landscape
Looking beyond lead actors, Figure 6 illustrates secondary participation and international collaboration. The United States again plays a central role, appearing frequently as a supporting partner. European countries including Germany, the United Kingdom, France, and the Netherlands also show high levels of collaborative involvement. Australia and Canada emerge as consistent Five Eyes partners.
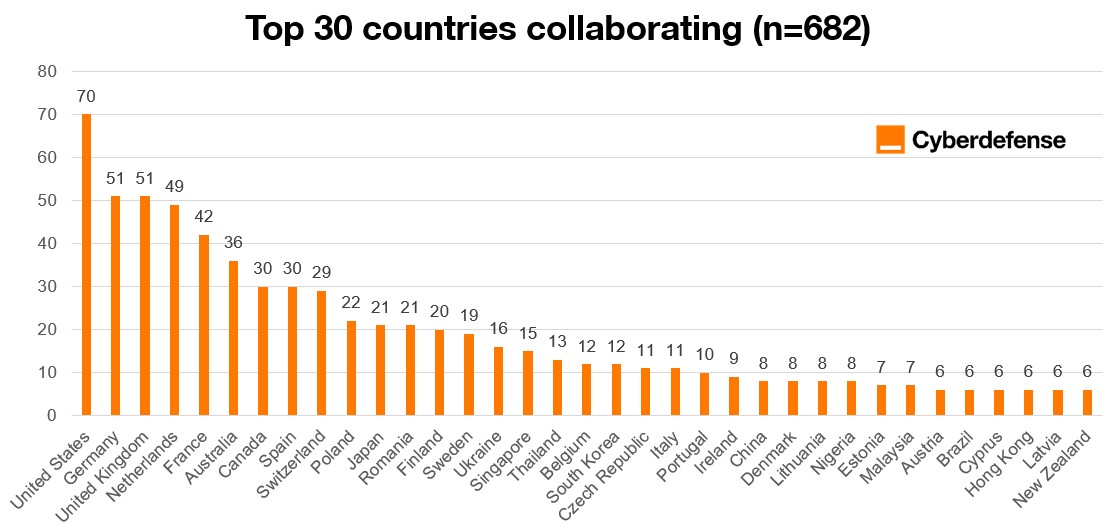
Figure 6: Top 30 countries collaborating
A broader group of mid-tier countries, including Poland, Japan, Finland, Sweden, Ukraine, Singapore, and Thailand, appears regularly in multinational operations. This distribution highlights the increasing globalization of cyber law enforcement and the growing reliance on coordinated cross border action.
Who are the Cybercriminals (that got caught)? Offender profiles and enforcement visibility
Offender data provides important context for understanding cybercrime dynamics. While enforcement actions focus on disruption, offender characteristics reveal who is actually being identified and prosecuted. It should be noted that some individuals appear in the dataset due to national differences in legal practice, as certain countries publicly issue wanted notices that identify suspects by name and age as part of an active investigation, whereas in many European jurisdictions such disclosures are far more restricted and typically occur only once formal charges have been brought.
Age
Figure 7 shows that cybercrime in this dataset is predominantly an adult activity. The largest share of offenders falls within the 35 to 44 age group, followed by those aged 25 to 34 and 18 to 24. Unlike traditional crime patterns that peak in adolescence, cyber offending appears to persist well into adulthood, suggesting sustained and deliberate engagement rather than impulsive behavior. While middle-aged offenders feature prominently in this dataset, younger offenders are likely underrepresented, since minors are often shielded from prosecution and public disclosure under national legal frameworks, limiting their visibility in law enforcement reporting.
Nevertheless, the age distribution of offenders in this dataset challenges traditional criminological assumptions. Foundational research on the age-crime curve suggests that criminal behavior typically peaks in adolescence or early adulthood before declining sharply. In contrast, cyber offending in this dataset is concentrated among adults, with the 35-44 age group representing the largest share of identified offenders.
This sustained engagement into mid-life suggests that cybercrime often involves deliberate and cognitively informed decision-making rather than impulsive or situational behavior. These findings align with rational choice perspectives, where offenders weigh risks, rewards, and opportunities over time.
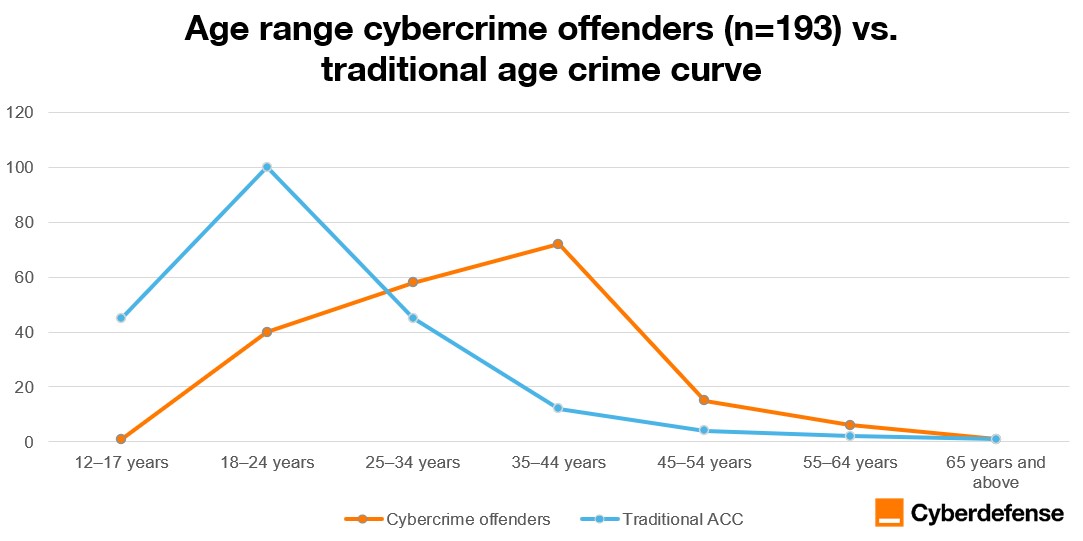
Figure 7: Age range cybercrime offenders vs. traditional age crime curve
Crime Types Across Age Groups
Figure 8 illustrates how offense types vary by age. Younger offenders are more frequently involved in technically oriented activities such as hacking and DDoS attacks, which may be exploratory or reputational in nature. As age increases, involvement shifts toward profit driven and complex activities, including cyber extortion, malware deployment, cyber espionage, and money laundering.
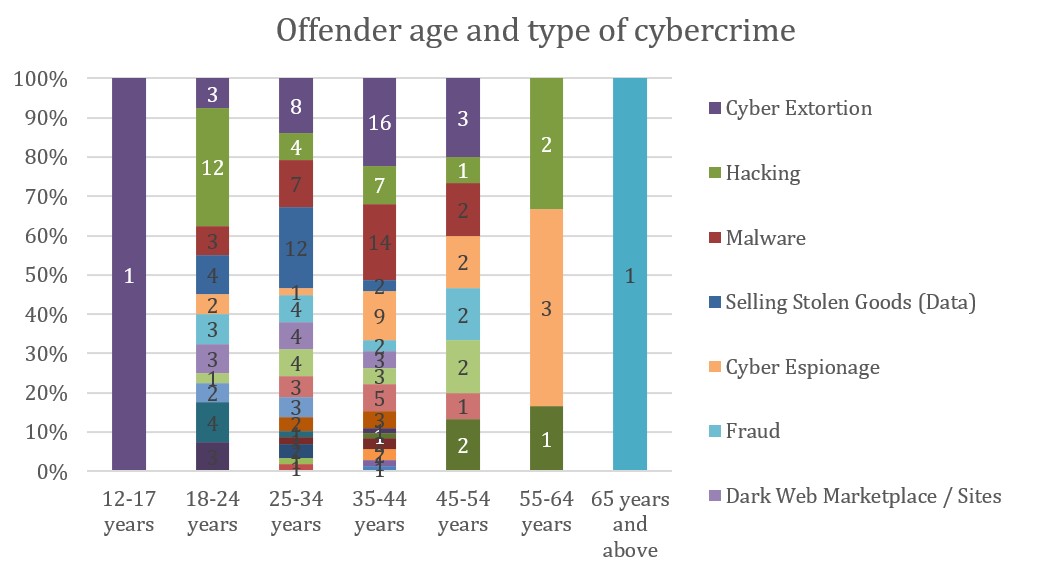
Figure 8: Offender age and type of cybercrime
Gender and Nationality
Figure 9 shows a pronounced gender imbalance, with more than 90 percent of identified offenders being male. This mirrors broader patterns observed in both cybercrime research and the cybersecurity workforce.
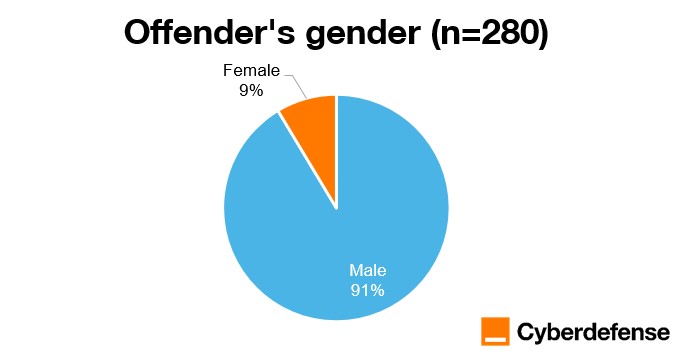
Figure 9: Offender’s gender
Figure 10 presents offender nationality data, revealing representation from 64 different nationalities. The distribution is heavily concentrated, with Russian nationals representing the largest single group, followed by American, Chinese, Ukrainian, and North Korean offenders. While nationality offers only partial insight in a transnational digital environment, it provides useful context for understanding regional enforcement visibility and geopolitical factors.
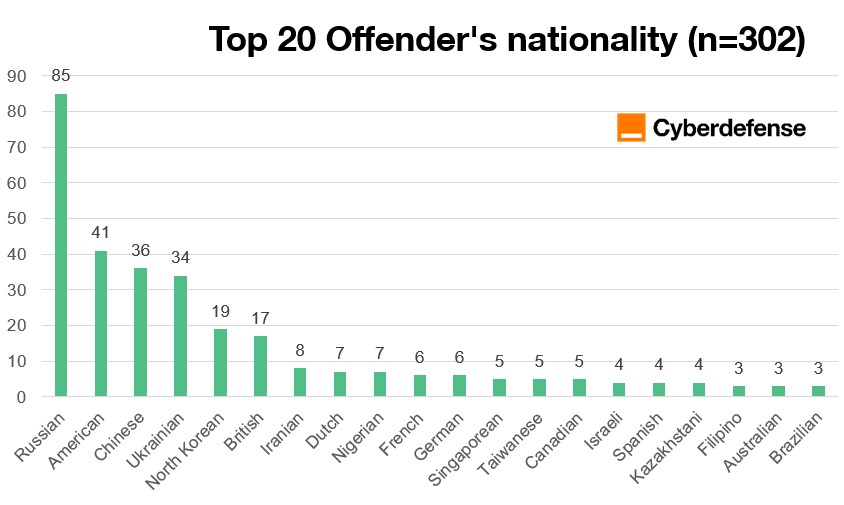
Figure 10: Top 20 Offender’s nationality
Conclusion
Taken together, the findings show that global cybercrime enforcement is becoming more active, more international, and more diversified. Financially motivated crime remains central, but law enforcement responses increasingly combine arrests, judicial processes, infrastructure takedowns, sanctions, and public private collaboration. At the same time, offender data highlights that cybercrime is largely driven by adult actors engaged in sustained and strategic activity.
These trends illustrate how cybercrime is shaped not only by technical capability, but also by legal frameworks, international cooperation, and enforcement visibility. Differences in investigative and prosecutorial practices influence which actors become visible, how threats adapt, and where accountability is ultimately applied.
For the full article, download the annual security report