
16 February 2023

Cyber Extortion (Cy-X) attacks have become a big threat in today’s digital society. They are a type of malicious activity where threat actors attempt to extort money from organizations, or even governments by typically gaining unauthorized access to sensitive data or networks and then demanding a ransom. Common forms of Cy-X attacks include ransomware attacks and distributed denial of service (DDoS) attacks with ransom demands. Here's a snapshot of our research.
Cy-X activity reached the highest volume ever recorded in Q1 2023, according to Orange Cyberdefense’s new report Cy-Xplorer 2023, which examined data from 6,707 confirmed business victims around the globe. This rise came after an initial decline of 8% in 2022. Our research also showed a geographical shift, with an increase in attacks last year in the Southeast Asia region (+42%), the Nordics (+40%), and Latin America (+32%), and a decrease in the US (-21%) and Canada (-28%). Overall, threat actors targeted businesses in 96 countries and publicly shamed over 2,100 organizations as a victim of Cy-X.
Countries are generally impacted in proportion to the number of registered organisations; however, this trend is changing. As governments in larger Western countries are now more proactively addressing attacks, threat actors are increasingly favouring countries whose local governments have fewer measures in place.
As a result, there has been a year-on-year increase (42%) in Southeast Asia, with Indonesia, Singapore, Thailand, the Philippines, and Malaysia the most impacted in that region. At the same time, we have seen a decrease in victims in regions such as the USA, Canada and Europe.
According to our findings, the Ukraine war had an impact on the Cy-X ecosystem, resulting in a decline in attacks as threat actors regrouped before continuing.
While geopolitical tensions saw many countries taking one side or the other, our research shows that Cy-X patterns didn’t follow suit. In 2022, 74% of all victims were from NATO countries, however, Cy-X attacks impacting NATO countries decreased noticeably at the start of the war and continued to decrease as the war progressed. Instead, the impact of Cy-X attacks on organizations increased in non-NATO countries, particularly in regions like Latin America (+32%) and Southeast Asia (+42%).
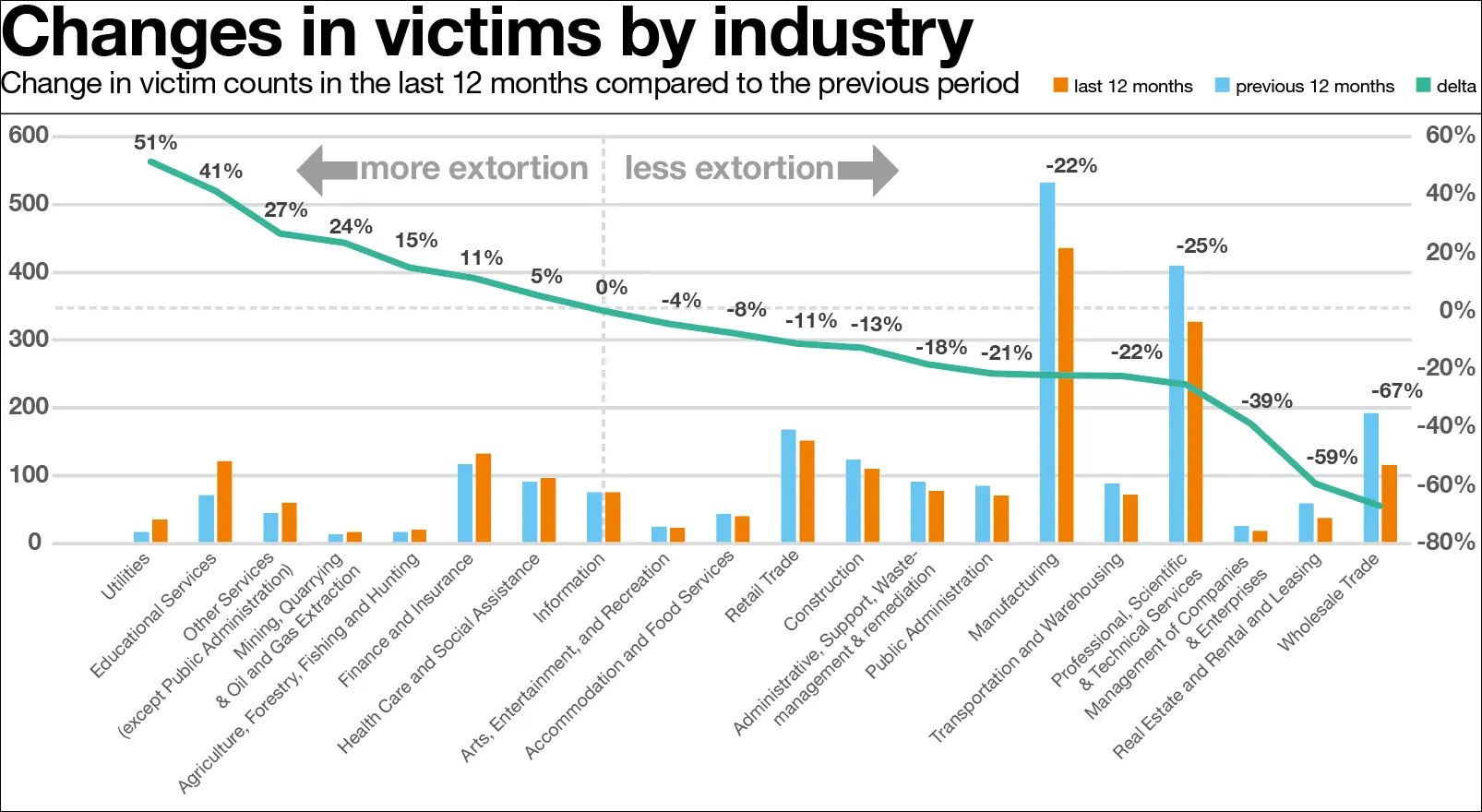
In 2022, Manufacturing was the biggest industry hit with approximately one-fifth of all victims across the industry. But despite this, the number of attacks fell 39% compared to the previous year. One reason for this sharp decline is the closure of the Conti group’s criminal activities.
Whereas the educational sector saw an increase of 41% in 2022 with around 10 Educational organizations being publicly exposed on the dark web per month. The Vice Society group emerged as a prominent actor targeting this sector.
The Utilities sector experienced a 51% surge in Cy-X attacks, although, the actual number of cases reported was only 35. However, in the Financial sector, there was an 11% increase in attacks, affecting over 130 Financial institutions. 75% of all victims were from organizations with fewer than 1,000 employees.
Threat actors also targeted businesses of all sizes. Large organizations were impacted the most with 36% of all victims, while small organizations accounted for 30% and medium-sized ones 24%.
In response to the rising number of attacks, governments worldwide are taking more proactive measures. Authorities in countries such as the USA, Australia, and others have issued official statements condemning threat actors and some have implemented regulations that prohibit companies from paying ransoms.
Law enforcement agencies and governments are also gradually gaining ground by disrupting the Cy-X ecosystem in other ways. These include the arrest of criminals, infrastructure takedowns, money seizures, international sanctions, development of decryptors for victims and ‘hack back’ activities.
As threat actors continue to exploit vulnerabilities in technology, wreaking havoc across various sectors, organizations need to protect themselves and be ready to respond to potential attacks. The best way to do this is by gaining a deep understanding of the underlying trends and geopolitical factors that drive these malicious activities.
However, tackling Cy-X attacks is not a challenge that organizations can tackle on their own. Our research highlights that collaboration between industry and government is important in addressing malicious cyber-attacks. But while we have made some progress, we must keep up this level of collaboration to slow down the increasing efforts of threat actors. Only then can we move one step closer to building a safer digital society.
.