
SolarWinds: Chasing the storm

When faced with the inevitable, embrace a new way of thinking
Be prepared for nasty weather
SolarWinds did not come out of the blue and should not be regarded as an isolated incident. SolarWinds is the inevitable consequence of a powerful set of systemic factors that collectively produce a climate that is inherently volatile but can still be predicted. While forecasts for a specific day may fail, the general tendency is driven by known forces and systems.
This volatile context currently strongly favours the attacker over the defender. That is not going to change unless the systemic drivers that create it are dealt with. In this case that means confronting and addressing some factors (like a massive investment by governments into computer hacking capabilities) and accepting and adapting to others (like the strong ties of interdependence that lie at the heart of cyberspace, the business ecosystem and indeed society in general).
How the attack happened
The SolarWinds Orion Platform is a unified system to monitor, analyze and manage IT infrastructure remotely. This software is used by a wide variety of companies, including prominent US Telco’s, banks, and major US government institutions. Attackers, dubbed UNC2452 by FireEye, a US cybersecurity company, managed to breach SolarWinds sometime around September 2020. They cleverly managed to insert a backdoor, labelled SUNBURST, into the SolarWinds Orion Platform software via the dynamic software build process, thereby infecting several versions of the software that were made available to SolarWinds customers via official, digitally signed, updates.
According to CrowdStrike3*, who are investigating the breach, this was achieved by a specific malware component dubbed ‘SUNSPOT’. SUNSPOT is the malware used to insert the SUNBURST backdoor into software builds of the SolarWinds Orion product. It monitors running processes for those involved in the compilation of the Orion product and replaces one of the source files to include the SUNBURST backdoor code. A third malware payload is called ‘Teardrop’ 4**. It is employed during post-exploitation and is delivered by Sunburst. Teardrop is used to drop a Cobalt Strike Beacon, which is used to communicate to the common commercial Command and Control system of the same name. It was not known at the time how SolarWinds themselves were breached, and details have not yet emerged at this time.
Worryingly sophisticated
The Sunburst backdoor is sophisticated in that it hides in a trusted component that is signed with a legitimate SolarWinds code signing certificate. The backdoor resides in a trusted process that is used for IT system administration, thus blending in nicely and extremely difficult to detect.
SUNBURST will remain dormant on initial infection anywhere between 12 to 14 days before it starts its activities. The attackers use SUNBURST for initial access with the intent to steal credentials and to gain secure remote access to the compromised environment. The attackers used secure remote access with the stolen credentials to propagate through the network.
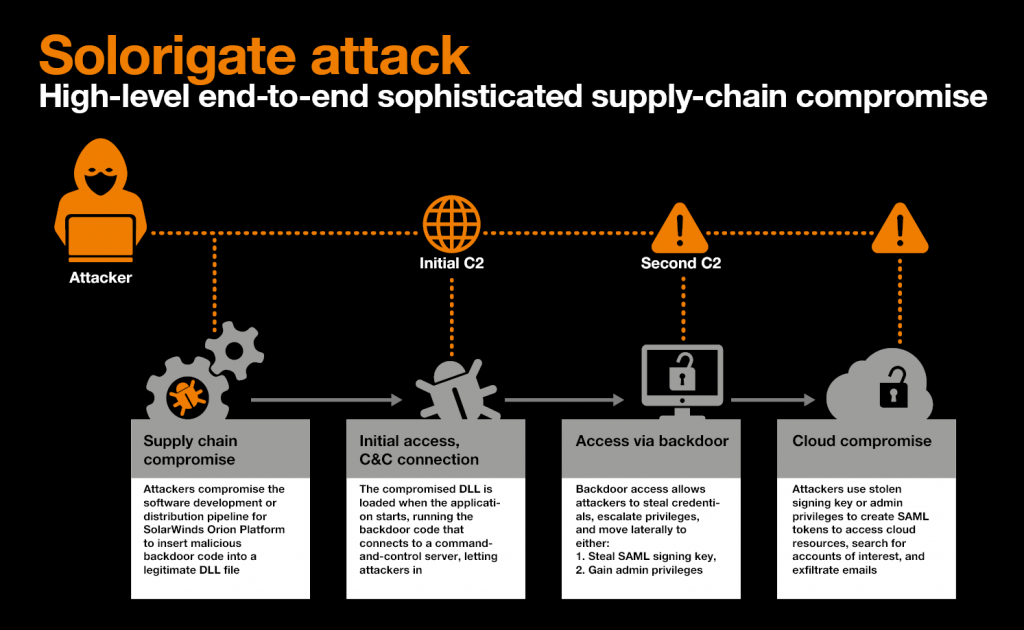
The SUNBURST backdoor, which uses steganography to hide any communication, can temporarily replace legitimate utilities with malicious versions, use a domain generated algorithm (DGA) for the C2 hostnames they wish to contact, and can detect the presence of anti-malware causing it to become dormant or stop any activity when it detects these “blocklist” items. Other vectors (apart from the software backdoor) may also have been used by the attackers and are currently being investigated. The SolarWinds story has been unfolding continuously since it first broke, with several high-profile government agencies and corporations (including Microsoft) confirming that they were breached via the backdoor in the SolarWinds software.
Who was the target?
Victims so far include the US Treasury, and the US NTIA, the US Department of Energy, and the US nuclear weapons agency. Microsoft was also a victim and has revealed additional details regarding the attack it suffered. The company reported that it detected unusual activity with a small number of accounts. Further investigations made it clear that attackers used these accounts to view source code in several source code repositories.
According to Microsoft***, no code was altered as the accounts had only read-only privileges. Microsoft maintains that the attackers viewing source code doesn’t imply an elevation of risk because its threat model already assumes that attackers have knowledge of the source code. Microsoft has not disclosed which of its products were affected or for how long hackers were inside its network.
The Orange Cyberdefense response
We believe it to be a mistake to focus too closely on the specific details of the SolarWinds attack. Instead we need to recognise that the security landscape is deeply fluid and dynamic, reshaping itself rapidly and continuously, and position ourselves to perceive and respond to it appropriately. We should not be distracted by the identity of the attacker, or the speculation about state-backed adversaries. Ransomware attacks, botnets, crypto miners and the like, all follow the same ‘opportunistic’ philosophy in which no target is too small or insignificant.
This is why it’s crucial for a new way of thinking, moving away from naïve rules-based security practices towards an agile, intelligence-based approach.
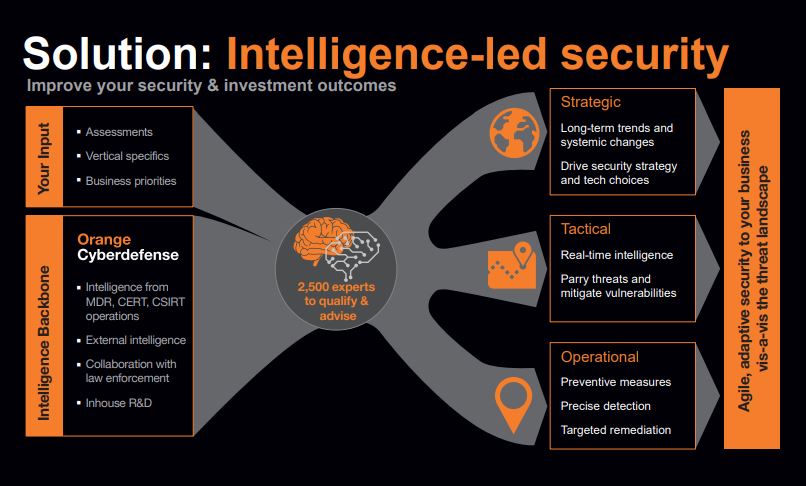
At Orange Cyberdefense we implement a philosophy of ‘intelligence-led security’ to ensure that we remain aware of significant events like SolarWinds and agile enough to provide our customers with the appropriate response when new threats and vulnerabilities emerge. Intelligence-led security is the collection and analysis of both internal (operational) and external (landscape) data in order to understand continuously changing risks so that limited security resources can be appropriately invested where they will have the most impact.
Our ‘World Watch’ Service works on behalf of the customer to collect, analyse and summarise global threat and vulnerability news to provide actionable security intelligence relevant to our business and our customers. The World Watch ‘Signals’ are produced by a dedicated Security Research Unit. Our process continuously collects security intelligence from diverse internal and open sources then processes it to produce actionable security bulletins, called Signals, that can be delivered to CISOs and Security Managers when they need them, how they need them.
A key element our World Watch process is that the actionable intelligence we collect is synthesised and communicated to our operational teams in a consistent, efficient and timely manner to ensure that the appropriate actions can be taken on behalf of the customers we support.
Conclusion
Successful cybersecurity today requires us to strike a fine balance between two prerogatives that will often be in tension with one another:
Firstly, a state of perpetual agility in which we continuously discern shifts in our environment and adjust our own approach accordingly, both at a tactical and a strategic level. Secondly, we need to move doggedly toward understanding, adjusting to, or impacting the underlying systemic factors that are shaping the volatile asymmetric reality we’re forced to contend with.
To offer a detailed understanding of the underlying causes and implications of the Solorigate attack and how to respond in both a practical and strategic way, our Security Research Centre has published a dedicated research paper available for free to those of you who are always on the look-out to improve your security posture.
Sources:
*https://www.crowdstrike.com/blog/sunspot-malware-technical-analysis/
**
***https://www.zdnet.com/article/solarwinds-hackers-accessed-microsoft-source-code/
More insights

