
Public cloud or companies: who is responsible for security?

If a data breach was to occur who is responsible? Is it the cloud services provider or the client company?
A huge success
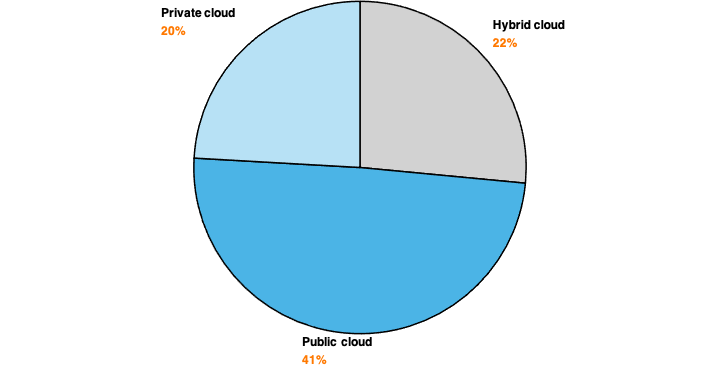
83% of corporate work data are in the cloud in 2020, according to a study conducted by LogicMonitor. Of these, 83%:
- 41% are stored on public platforms;
- 20% in a private infrastructure;
- 22% in a hybrid cloud.
Several factors can explain the popularity of the public cloud. Cloud services providers (CSPs) are based on pay-per-use consumption and billing. CSPs provide access to various computing services and applications (such as Office 365, for example). In exchange, the customer is billed only based on their actual consumption of the resources required for their operation.
These models provide great flexibility, scalability, and high availability, and drastic cost reductions: real advantages for any company. They benefit from computing and development power that is difficult to match globally: their applications and data can be accessed from anywhere in the world. By way of illustration, Microsoft Azure is present in 142 countries.
However, since no system is infallible, the cloud (whether public, private, or hybrid) is a source of risk, and data leaks can happen. The security of infrastructures, data, and access, therefore, remains paramount. But who in the enterprise, or its CSP, should take responsibility for this?
Public cloud: who is responsible for security?
The security support by the cloud services provider (CSP) is not the same, depending on the level of service chosen. Whether it is an IaaS, PaaS, or SaaS (Infrastructure/Platform/Software as a Service) service, it is essential to know that security responsibility is always shared between the CSP and its customer.
Furthermore, and most importantly, the customer remains responsible for securing his data, setting up his cloud environment, and must stay in control of access and resource control.
Focus on: GDPR
Under the General Data Protection Regulation, it is generally accepted that CSPs are legally qualified as subcontractors and benefit from the obligations and responsibilities for protecting personal data arising from this role, just like any other subcontracting company.
However, the legal qualification must be studied on a case-by-case basis depending on the actor concerned, whether it is a CSP or another. As stated in the previous paragraph, even in an incident, it is always the customer who remains responsible for the data he hosts in a public cloud.
What are the risks for companies?
The most common attack vectors
Identity theft: hackers, through phishing campaigns, for example, can recover access from cloud users. From there, it becomes straightforward for them to control resources in the cloud infrastructure and hijack data.
Malware: they are capable of damaging and destroying an information system but also of stealing, modifying, or deleting data.
SQL injections: they offer attackers the possibility to target selected databases directly and steal the files and information stored in them.
Distributed denial of service attacks: these attacks have an obvious goal: to make the service completely unavailable. When a cloud service is affected by a DDoS attack, the infrastructure can compensate by requiring more resources, thus generating overbilling for the customer. There are anti-DDoS mechanisms set up by CSPs, limiting the type of attack, but fine-tuning of the resource management is necessary to avoid over-consumption.
System vulnerabilities: To avoid system and resource takeovers, it is necessary to rely on its intrusion detection and vulnerability management solutions.
Advanced Persistent Threats (APT): These highly targeted, long-term cyber-attacks allow an attacker to infiltrate a network undetected, damaging the data and infrastructure they are targeting.
It should be noted that CSPs offer services – usually as an option – to protect against this type of attack, but it must be known that they must be complemented by third-party mechanisms to best protect against it.
The most frequent errors
Insufficient risk analyses: When companies define new strategies or new services, it is essential to evaluate the technologies used in the cloud, analyze the risks involved, and have an appropriate roadmap and checklist to ensure that these services are not exposed to attack.
Unsecured APIs: One of the critical aspects of the security of services in the cloud is often found in the programming interfaces (APIs) of the services offered to create applications. These APIs are among the most differentiating elements provided by vendors, but they must be designed to avoid any attempt to exceed security rules.
Abuse and harmful cloud services: Poor control over cloud usage and resource utilization can quickly overwhelm the bill. Cost governance and regular monitoring and the establishment of financial policy for cloud usage are necessary.
Insufficient network protection: An enterprise that chooses the public cloud must consider that it remains responsible for managing and allocating access. To do this, it can rely on protection mechanisms such as firewalls, network segmentation, and WAF, detailed later in this article.
Cloud: how best to protect yourself?
Secure your entire virtual network infrastructure, its routing, and make the right choice of storage services.
An enterprise that decides to move to the public cloud must rebuild (according to the level of services chosen) its entire network and application infrastructure, system, and storage in a cloud. Even a carefully executed development does not entirely protect against the risks of cyber-attacks. In addition to the security offered by the CSP, solutions exist.
If firewalls are still essential to secure infrastructure, they will be reinforced by the use of third-party NextGen Firewall solutions and WAF. As their name indicates, Web Application Firewalls are firewalls for web applications. They ensure that web servers are not affected by an attack by analyzing user requests and application responses. WAFs thus protect web applications and services published in clouds.
Manage access and identities
“71.5% of the violations targeting Amazon Web Services (…) concern flaws in identity and access management,” wrote Silicon.fr in 2018. If the idea is not to point precisely at Amazon – all CSPs can encounter the same problems – it highlights the problematic access control in the cloud.
Employee awareness remains key to ensuring a secure cloud access policy. Moreover, access management, mostly after employees leave, must be a priority concern for companies: according to Intermedia, for 89% of companies, employees who have left them still benefit from IT access to connect to it[3].
CSPs offer native access management mechanisms via the Active Directory [4] and integrate encryption. These solutions enable authentication, authorizations, SSO (single sign-on), MFA (multi-factor authentication) to secure access to resources and data. However, experience shows that it is better to compliment them with third-party software.
Protect your data
DLP: Data Leakage Prevention (DLP) allows files to be marked and provides a confidentiality level. The more sensitive the data is, the more restricted its access will be, according to a scale determined by each company.
CASBs: Cloud Access Security Brokers (CASBs) analyze data flows and scan documents within a cloud. They enable to extend the security policy in the cloud by controlling activities and access.
CWPs: Cloud Workload Protection (CWP) tools check for wrong cloud infrastructures configurations, including data storage spaces. They provide an overview of the actions taken by each administrator.
Note that CASBs and CWPs can detect malware.
What about multi-cloud environments?
All the risks mentioned in this article are multiplied in a multi-cloud environment. The management of settings, access, resources, security, regulatory compliance, and budgets makes everything much more complicated.
As each cloud environment has its own technical and configuration specificities, the diversification of CSPs (Amazon Web Services, Microsoft Azure, Google Cloud Storage…) brings a complexity of the organization, management, control, and visibility of services. To be accompanied by a third party can prove to be of paramount importance.
Despite all the cloud’s merits, security remains essential. Since customers are always responsible for their data, the implementation of management and security policies is necessary to stay compliant with each company’s security objectives (and by the regulations in force). Regardless of its level of maturity in cybersecurity issues, an entity should not hesitate to seek support.
More insights

