
8 März 2021

Ransomware can be described as “a subset of malware in which the data on a victim’s computer is locked — typically by encryption — and payment is demanded before the ransomed data is decrypted and access is returned to the victim.” Source
The first instance that falls under this definition, although occurring years before it was defined as such, was the AIDS Trojan. The malware received this name due to the victims targeted all being delegates at the 1989 World Health Organization AIDS conference in Stockholm.
They all received floppy disks (remember them?!) which contained malicious code which encrypted the names of all the files and hid all the directories on the drive after the system booted for the 90th time after being infected. This resulted in the system being unusable.
Victims were presented with a note telling them that they had to send $189 to a postal address in Panama if they wanted their system to be restored. Whilst a far cry from modern ransomware attacks this attack is known as the first attempt to extort money from victims by preventing access to their files and systems. Fortunately, due to the weak encryption used by the Trojan, security researchers were able to release a free decryption tool.
After the mid-2000s, ransomware continued to evolve and started utilizing stronger, often off the shelf, encryption mechanisms. The attacks were still limited primarily to individual home users often with ransoms asking for no more than a few hundred dollars. This can be attributed to the fact that the ransoms needed to be paid in the standard currency which didn’t offer any form of covertness for the criminals.
In 2012, a byline from an eWeek article read: “Rather than encrypt the entire hard drive, criminals are using fairly unsophisticated ransomware to lock a victim’s PC and then demand cash for the keys”. This was one of the few early observations of the emerging new threat that was ransomware. It was one of the myriads of business models that cybercrime was experimenting with at the time. The journalist ended the article with this sentence: “I think it is just a temporary trend until someone finds a better idea to make money easier”.
The comment about a ‘better idea to make money easier’ pointed to ransomware’s Achilles Heel at the time. There was no easy way to receive payment from the ransomware victim, with the criminal forced to resort to the use of pre-paid cards or money transfers.
It would have seemed clear at the time that ransomware as a form of crime was unlikely to go anywhere. It was just too difficult to get payment from the victim. Nowadays, the final quote seems ironic. The trend, as it turns out, was anything but ‘temporary’, as the chart below illustrates…
Publicly reported ransomware incidents over time
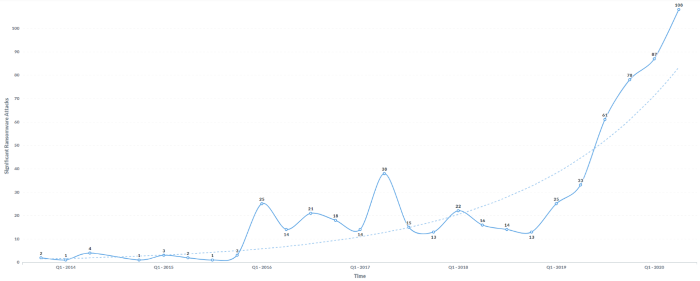
Publicly reported ransomware incidents over time. Source: Orange Cyberfense and the Temple University. Project: ‘Critical Infrastructures Ransomware Attacks (CIRWAs). Includes 687 records assembled from publicly disclosed incidents between November 2013 and August 2020.
For the 2012 cybercrime ecosystem, ransomware was a natural pivot. It represented a business model that allowed for ‘direct monetization’, as opposed to stealing data for example, which would then need to be resold for any profit to be made.
Ransomware also had some advantages, notably that there is less need for the malware operator to maintain a Command and Control (C&C) channel with the infected machine.
But it still lacked one significant advantage. It could not use the cheap and reliable payment networks provided by the credit card companies to extract payment from its customers, which was the model at the time. There was no safe and efficient way to receive and verify payments from victims. That meant ransomware as a business model was essentially dead in the water.
On 18 August 2008, the domain name bitcoin.org was registered. Later that year the mysterious Satoshi Nakamoto published his seminal paper on methods of using peer-to-peer on “a system for electronic transactions without relying on trust“. On 3 January 2009, the bitcoin network came into existence.
Bitcoin turned out to be just what the flailing ransomware crime model needed – a safe, cheap, simple, and reliable means to receive payment from their targets. Apart from the high degree of anonymity, a hacker can simply watch the public blockchain to know if and when a victim has paid up; or even make a unique payment address for each victim and automate the process of unlocking their files upon a confirmed bitcoin transaction.
By 2013 the CryptoLocker ransomware strain – using Bitcoin to collect ransom money – had earned around US$27 million in just two months.
Cryptocurrencies had helped turn ransomware into a viable cybercrime business model. When cyber insurance policies started paying the ransom on behalf of the victim, it created the perfect storm. Ransomware is now the cybercrime’s killer app and as far as we can see, it is here to stay…
For more intelligence-led ransomware insights, take a look at our Security Navigator.
Security Navigator Insights