MITRE Engenuity — Calculator and Scoring

"Where to start"
MITRE Engenuity develops free solutions with and for our industries worldwide. Although these solutions are developed by the brightest minds, they are still very little used.
One of the most innovative developments and one of the most valuable for companies is the calculator for the Top ATT&CK MITRE techniques. The calculator gives companies the chance to find a “where to start” when they are challenged to implement mitigation and detection to harden their systems against threat actors in a constantly changing environment.
Top 10 MITRE ATT&CK techniques
MITRE Enegnuity has developed a methodology to find the top 10 MITRE ATT&CK techniques as a starting point for companies and to find adequate mitigation and detection adopted to the needs of the specific infrastructure. And this is why a top MITRE ATT&CK technique list should be actionable and driven by threat intelligence. This belief guided the creation of the MITRE Engenuity methodology. It is composed of actionability, choke point and prevalence. MITRE Engenuity created algorithms for each component, and then combined each component weighted to give it an overall score.
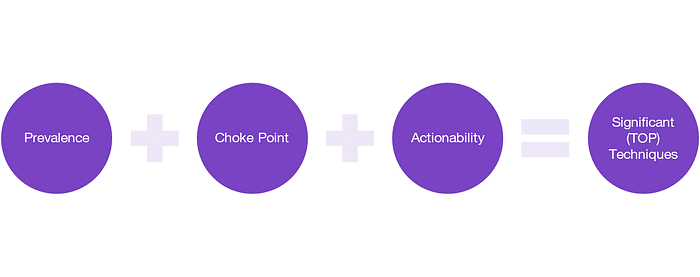
System and Methodology
We then made a total count of all detections and mitigations available for each ATT&CK technique. Techniques that have a greater number of detections and mitigations are weighted more heavily than those with a lower number. If a technique has a limited number of ways to detect or protect against it, we believe defending against those techniques will provide diminishing returns and more attention should be placed elsewhere.
More about the methodology
In addition to a 3-year research work and detailed mathematical evaluation of data, more than 22 ransomware reports were calculated and evaluated using mathematical calculations according to frequency of which an attacker uses a specific MITRE ATT&CK technique over time. Not only the frequency of the attacks were included, but also the most effective measures that can be implemented to prevent the attacker from causing further damage in the systems, the so-called choke point.
Analyzing chokepoints can assist defenders to pinpoint critical techniques needed to be successful in an attack. These techniques serve as a common denominator amongst in otherwise disparate attacks. For instance, T1047 (WMI) can serve as a choke point because there are a many other techniques that can be executed after an adversary executes WMI. Defending against malicious WMI usage can limit the potential attack path that an adversary might have used.
The calculator offers the option of setting priorities by using the filter to select what the company attaches particular importance to using both the NIST and the CIS framework.For detections, we reviewed several publicly available analytic resources and mapped each of them to ATT&CK. The repositories we used were MITRE’s Cyber Analytic Repository, Elastic, Sigma HQ’s rules , and Splunk Detections.
For mitigations, we reviewed security controls from two publicly available repositories and mapped each of them to ATT&CK. The repositories we used were CIS Critical Security Controls and NIST 800–53 Security Controls.
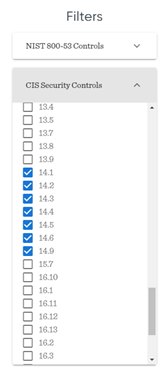
CIS Awareness Security Controls
If there is recently a ransomware attack on the infrastructure and the initial vector is phishing, the focus on phishing and awareness can be selected here in the filter for NIST and CIS.
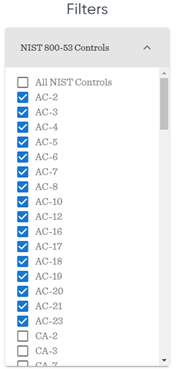
AC NIST Controls for Phishing
Depending on which repositories or operating systems are used by the company, a selection is also possible here:
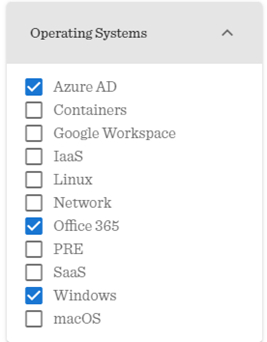
Operating System Example Top 10 Techniques
Detection Analytics Customer use (in this case no specific detection analytics)
In addition, the company can also assess the monitoring. How good is the network, file, process and hardware monitoring? Do they have any cloud monitoring components? Depending on what is chosen, the top 10 techniques and the respective measures change.

How good is your monitoring?
Depending on the result, the techniques can then be downloaded in the form of a JSON format and are available to management, also to display the techniques in the ATT&CK Navigator.

JSON Format of the results
CIS Community Defense Model
With the result, the analyst can then proceed with the measure evaluation by weighting the techniques and the number of measures that can be used repeatedly for other techniques as well. The weighting is also interesting if the top CIS Community Defense Model measures can be used to work out which measures are the most effective and should be installed first.
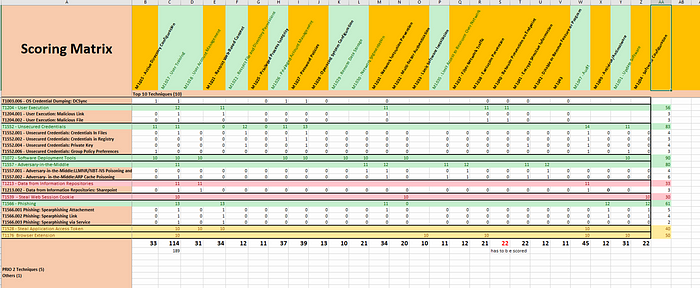
Scoring Matrix — Where to start top mitigation
Where there are not enough hardening measures, the author recommends developing detection rules using MITRE detection engineering and analyzing the MITRE ATT&CK techniques in a deep dive. Appropriate countermeasures can often be found in the Holy Grail of defense, the D3FEND.
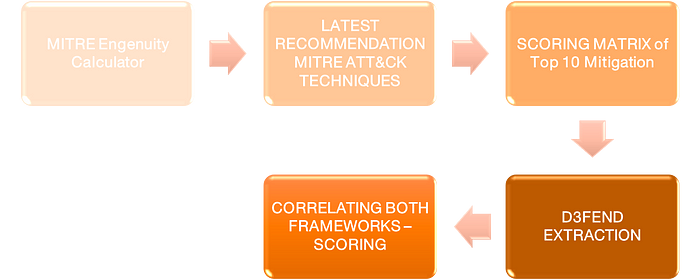
How to mitigate and score
Next, you can add the measures for the NIST and the NIST controls within the D3FEND framework according to the analyzed and prioritized MITRE ATT&CK techniques. But there is much more to come. A possible deception strategy can also be worked out according to the MITRE ATT&CK techniques with the MITRE Engage.
You can do this in just a few hours. Therefore, this solution is a starting point for companies in the fight against ransomware, be it in the critical infrastructure or in the usual IT environment. Once you know the necessary NIST and CIS controls, you can implement them relatively quickly for the corresponding operating systems.

Top CIS ATT&CK v8.2 Framewokr Top 10 Controls
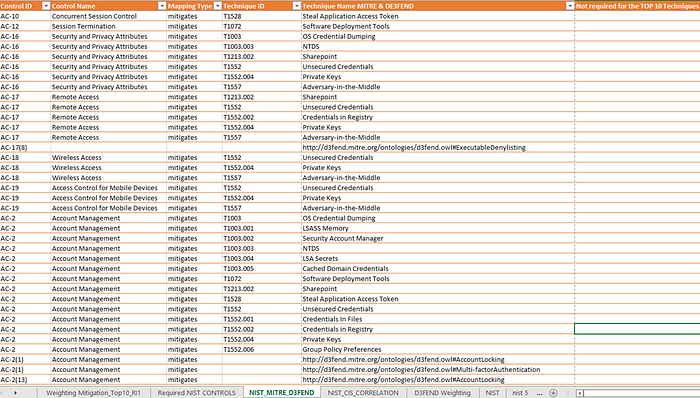
Top 10 NIST Controls for Mitre ATT&CK and D3FEND
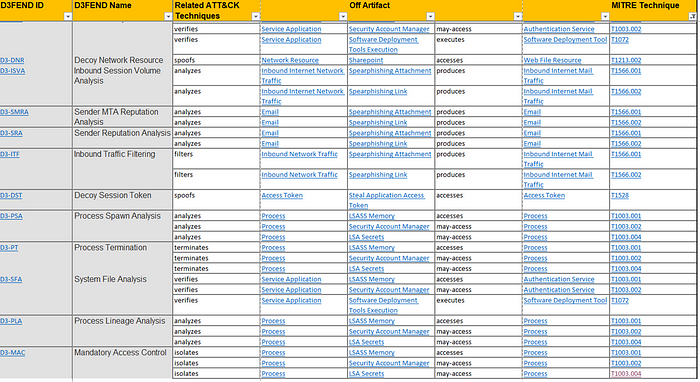
Top 10 D3FEND Techniques
Why MITRE Engenuity
MITRE Engenuity offers not only large companies but also small and medium-sized companies a free solution for fast hardening of the systems thanks to its well-founded scientific preparatory work. Hopefully more people recognize their great developments in the future.
More Information
Another great short introduction to the Top ATT&CK MITRE calculator you can find on YouTube here: Leadership Spotlight — CrowdStrike — Top ATT&CK Techniques.
The Center for Threat-Informed Defense is proud to launch our new video series, Leadership Spotlight. Our first episode premieres with a discussion of Top ATT&CK Techniques, featuring Joel Spurlock, Senior Director of Malware Research at CrowdStrike, a Research Partner at the Center and participant in the Top ATT&CK Techniques project. Joel highlights a key challenge: With MITRE ATT&CK® being a big space and limited numbers of cybersecurity experts, how do organizations adopt ATT&CK into their security operations, and build strategy to improve their defense? He explains how the Top ATT&CK Techniques project delivers a key methodology enabling an organization to prioritize their defense around ATT&CK based on their maturity and security controls, and how this methodology was developed. Joel also goes into depth on how CrowdStrike leverages this R&D work.
Watch this episode and stay tuned for upcoming videos on how Center Participants, among the most sophisticated cybersecurity teams from around the world, bring thought leadership and commitment to the Center’s mission.
