

Managed Secure Access
A new mindset to address new business needs
The world is changing
Digital transformation: +53% is the expected YoY spending growth on cloud services in 2022 (Gartner Research)
Apps are everywhere: An average enterprise has 464 custom applications deployed, and IT security are only aware of 38.4% of those (Cloud Security Alliance Report)
Work from anywhere: 48% of employees will work remotely at least some of the time post-pandemic (Gartner Research)
Enterprises are changing their architecture
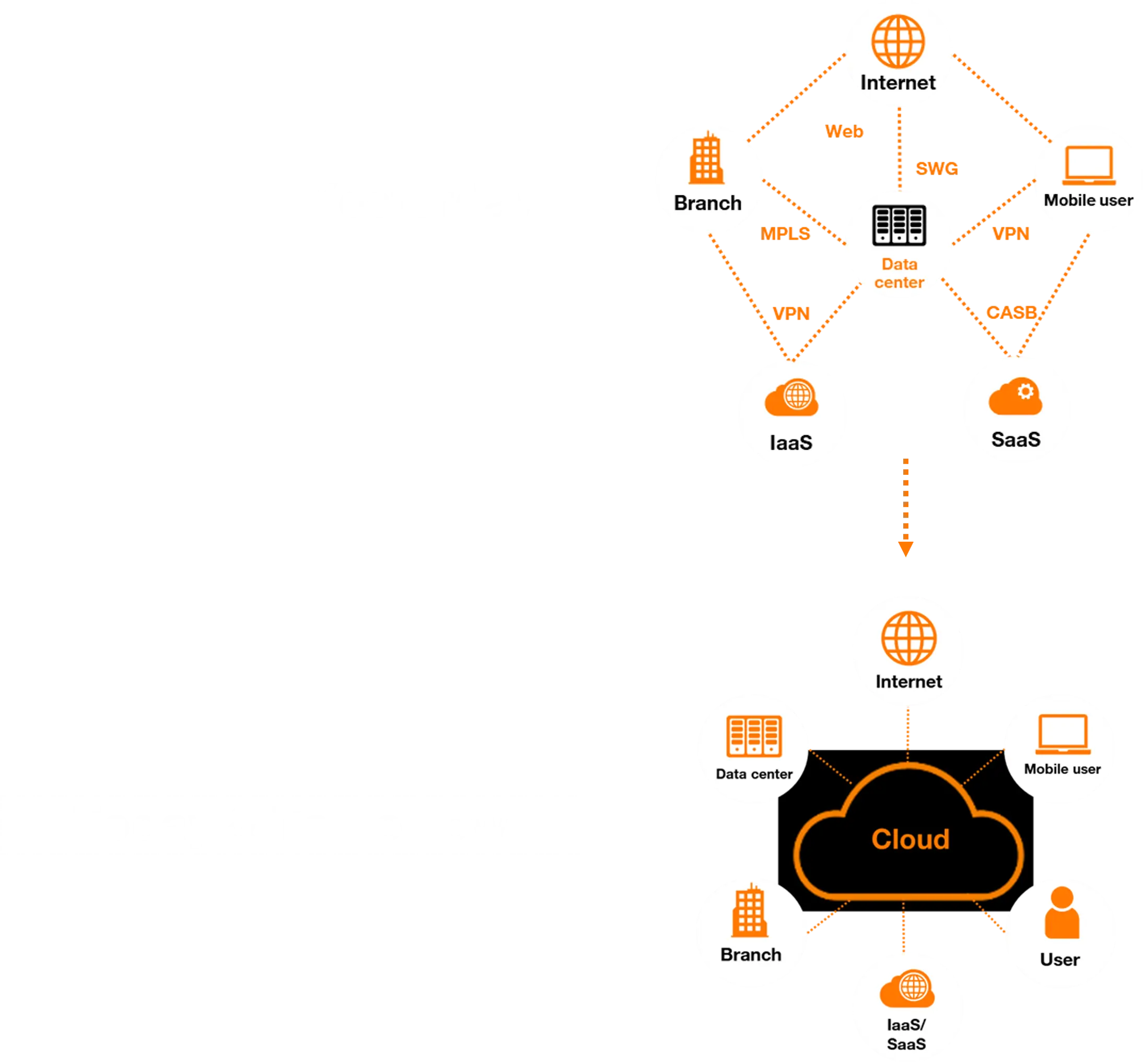
This is not the only change … the architecture which is connecting the different sites, applications, and users is changing too.
Today, and following the departure of the users from the offices and the Applications from the datacenter, the cloud is becoming the new center of gravity, where everything connects back to it. Datacenters did NOT disappear, but instead of being the center of the architecture, they are connecting back to the cloud similar to any branch office!
And as in the past when all the security was built inside the datacenter to protect an enterprise most important assets … Now the security has to be built in the cloud … the new home of critical applications & data.
Discover our datasheet
From what you are facing...

See further
Expand existing protections to cloud platforms without losing visibility

Policy Enforcement
Challenges to enforce a consistent policy across all users, at all times, on any device type

Lack of agility & limited budgets
Address a complex threat landscape, shortage in security skills, and eroding budgets.

Hard to control user experience
Measure the quality of the users’ digital experience and address concerns before they become issues
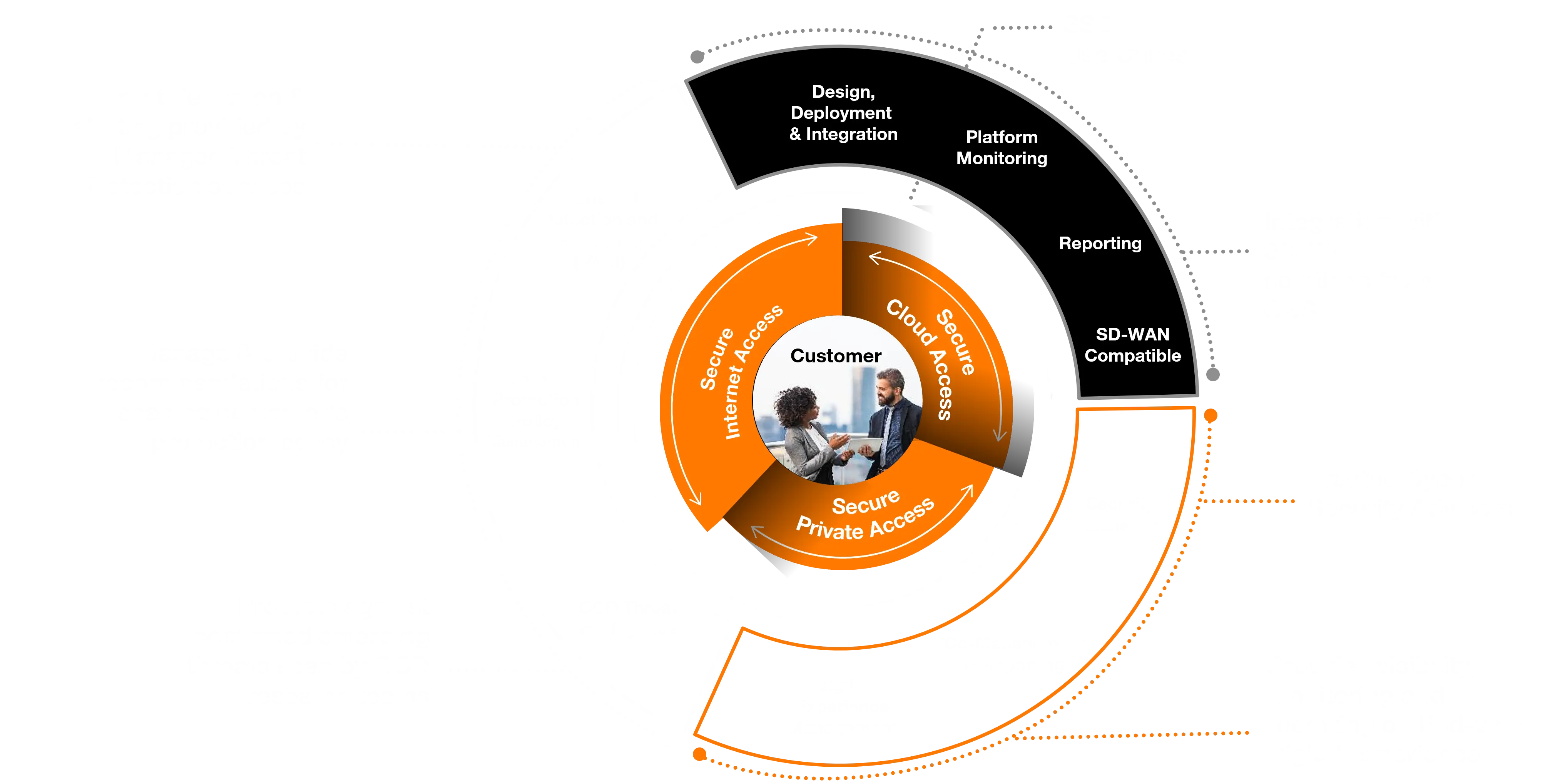
A single solution to secure all types of access
...to an efficient and solid protection
Flexibility
Hybrid deployments allows you to gradually expand your protection policies to the cloud. The co-management platform provides you with global visibility
Consistency
Benefit from consistent policy enforcement & visibility
Agility
Take advantage of our flexible delivery models
Take your first step toward SASE
No two SASE journeys are alike.
A successful transition to a SASE architecture depends on how you choose to design, build and maintain the network to secure users, applications and devices.
Orange Cyberdefense is here to help you achieve a seamless and secure transition to a SASE architecture while reducing complexity and optimizing the user experience.
Read more on SASE:


