How F5 Networks’ Application Delivery Controllers contribute to GDPR.

GDPR: a short summary
The General Data Protection Regulation (GDPR) is the EU’s upcoming new personal data protection law. On the 25th of May 2018, the GDPR becomes enforceable and will replace the Data Protection Directive that was introduced in 1995. This will significantly change the rules surrounding the protection of personal data of EU residents.
The GDPR is much stricter and has a greater scope of coverage than the Data Protection Directive. The GDPR now also includes companies outside the EU and introduces new data breach notification requirements and administrative fines. The vast majority of GDPR requirements are centered around data management and data security. In essence, the law requires and enforces the security of data processing. This includes access, rectification and erasure of personal data held on individuals, and the right of data portability.
2 GDPR principles you can’t forget
GDPR is about privacy. When talking about security versus privacy, two principles of ‘Privacy by Design’ are very important:
You can have security without privacy, but you can’t have privacy without security.
Security and transparency are privacy’s key driver of success.
Technologies like Palo Alto Networks and F5 Networks play a key role in the support of these two principles. This blog post will elaborate on specific features of these two technologies in your journey towards GDPR readiness.
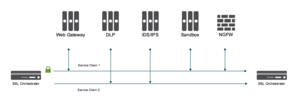
How F5 Networks’ Application Delivery Controllers contribute to GDPR.
Orangecyberdefense primary focus with F5 Networks is on the incoming connections and the protection of public-facing datacenter resources that are vulnerable to data theft, hacking or manipulation. Needless to say, a lot of GDPR-sensitive data is located in applications and databases on servers in these datacenters.
The following F5 features are very interesting to look at in the context of GDPR:
SSL/TLS Encryption and Decryption Capabilities:
As it comes to GDPR, encryption is mentioned as a Privacy Enhancing Technology (PET). The SSL/TLS visibility functionality of F5 Networks provides encryption and decryption capabilities for data in transit on crucial places within your infrastructure. F5 Networks offers the following state of the art technology feature to support GDPR:
- Encryption of data: F5 Networks encrypts GDPR-sensitive data the moment it is in transit between (end-)users and applications, applications and database or between machines.
SSL/TLS Visibility:
As with Palo Alto Networks, we need visibility into the incoming traffic before anything can be detected or prevented. Traditional security gateways, network firewalls, and intrusion prevention system (IPS) appliances have decryption capabilities, but most organizations don’t have the right architecture in place to enable it holistically.
F5 Networks has added value in the field of SSL/TLS visibility by providing the following features:
- Unified visibility: F5 Networks can offer a unified solution by providing a single point of control for SSL inspection with support for the latest encryption ciphers to provide superior TLS inspection.
- Security Service Chaining: To solve specific security challenges, security administrators are accustomed to manually chain multiple point products, creating a security stack consisting of multiple services. A typical stack may include components such as data loss prevention (DLP) scanners, web application firewalls, intrusion prevention systems (IPS), malware analysis tools, and more. F5 SSL Orchestrators can dynamically chain security services by matching the URL and policies that determine whether traffic should bypass or be decrypted and sent to one service or another. This policy-based traffic steering capability reduces administrative costs and enables organizations to gain more value from the investments they’ve made in these security services.
Access Protection:
After creating visibility into the incoming traffic streams, the next most important aspect is to create an insight into how and by who applications are used (or abused). To accomplish this, it is important to have information about things like unauthorized or malicious access attempts and to have some form of identity and access control.
F5 Networks’ APM (Access Policy Manager) can provide a solution for this by enabling a granular and context-aware secured access for all your applications. In addition to the standard authentication types, APM can also enable advanced Multi-Factor Authentication (MFA) or Step Up Authentication flows. Single Sign-On (SSO) and/or Federation services between local and cloud-based resources or applications can be integrated through full support for SAML 2.0 and OAuth 2.0.
F5 Networks BIG-IP APM can also enable an inspection of the user’s endpoint device through a web browser or through the BIG-IP Edge Client to examine its security posture and determine if the device is part of the corporate domain. These endpoint inspection checks can consist of verifications of OS type, anti-virus software, registry files, CPU or HDD ID, hard disk encryption enabled and so on. Based on the results, it can assign dynamic Access Control Lists (ACLs) to deploy identity-, context-, and application-aware security.
Finally, in order to be GDPR ready, it is not only important to protect the infrastructure but also to have good logging and reporting in place about potential unauthorized access attempts or data breaches.
Using a combination of F5 BIG-IQ Centralized Management and BIG-IP APM helps to gain visibility into traffic and application trends. With customized reports including access failures, impacted users, accessed resources and IP geolocation, it is possible to quickly identify problems, accelerate incident response and aggregate data for long-term forensic analysis.
Application Protection:
Lastly, it is important to secure internet facing (web-)application access and the sensitive data behind those applications from hackers or other malicious attempts to steal data. Hackers can abuse application weaknesses or 0-day exploits to gain access to and exfiltrate sensitive data.
In order to mitigate this risk, an F5 ASM (Application Security Manager) can be deployed that serves as Web Application Firewall (WAF).
The F5 ASM has many different features to detect, prevent and report L7 based application attacks.
Needless to say this plays an important role in the process of becoming GDPR-ready.
The following F5 ASM features are the most important ones to look at:
- Track malicious user attempts: Distinguishing permitted users from malicious users whenever a web application is used helps to minimize security risks and prevent unwanted activity. With F5 ASM, application security teams can employ device fingerprinting and session tracking techniques to identify specific end-users, application sessions, and attackers. These unique capabilities allow to easily distinguish between human traffic and bot traffic, prevent malicious attempts, and helps to more accurately mitigate brute force, session hijacking, web scraping, or DDoS attacks to reduce the risk of data loss by a hack.
- Patch Application vulnerabilities: F5 ASM can detect and mitigate layer 7 threats including web scraping, SQL injection, brute force, CSRF, JSON web threats, DoS-heavy URLs, and zero-day attacks. ASM can defend against multiple, simultaneous, volumetric application-layer threats including stealthy, low-bandwidth DDoS attacks. F5 ASM can also prevent the execution of fraudulent transactions, stop in-browser session hijacking, and report on regular or repeated attacks from IPs.
- Extensive reporting and analysis: The ASM can provide the reporting capabilities to analyze incoming requests, track violations, generate security reports and evaluate attacks. These capabilities help the IT department to make informed security decisions. With full REST API support integrations with SIEM or other management services are also possible. For deeper analysis, high-speed indexing and long-term data aggregation, the F5 ASM can also integrate with solutions like IBM QRadar or Logpoint.
- Data Transparancy: The ASM has Sensitive Parameters settings to protect sensitive user input, such as a password or a credit card number, in a validated request. The contents of sensitive parameters are not visible in logs nor in the user interface. More extensive anonymization of logs needs to be done through an external solution. In this case, the logs should not be kept on the F5 devices but on an external logging server. Pseudonymization/Anonymization solutions like puppetDB for example can then process the logs to protect user privacy.
Conclusion
From the F5 Networks side, the focus shifts to the protection of applications and database containing your GDPR sensitive data. Encryption, Access Control and Application Protection against breaches are a must have. The combination provides you with the desired confidentiality and integrity of the GDPR sensitive data your organization has while these technologies elaborate on optimizing availability.
