Pan-OS 10.0: Security features
Palo Alto Networks
Do you have a state-of-the-art firewall from Palo Alto Networks today?
In this rapidly-evolving technological world, it is crucial to check whether your firewall can still face current and future threats. Our Palo Alto experts have created a checklist with 7 items to help you protect your organization.
Go to the checklistInline WildFire & URL Machine Learning based Prevention
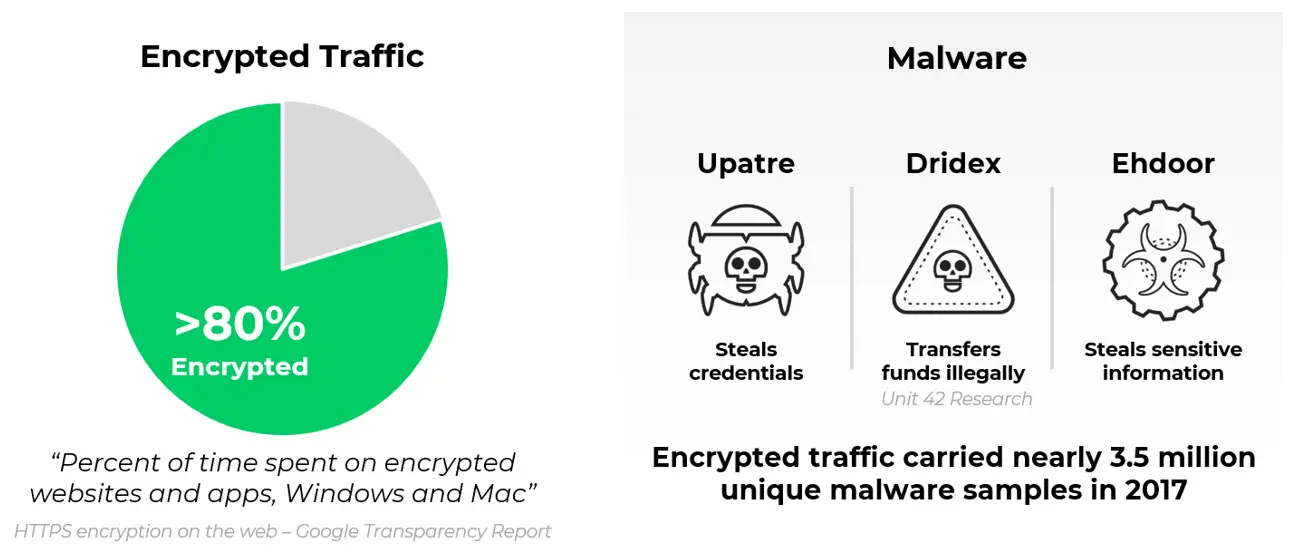
The ML-based prevention works for files and web-based attacks. It performs immediate inline prevention against phishing and JavaScript attacks. This should help against phishing attacks launched every day and most of them are opened within the minute they are received.
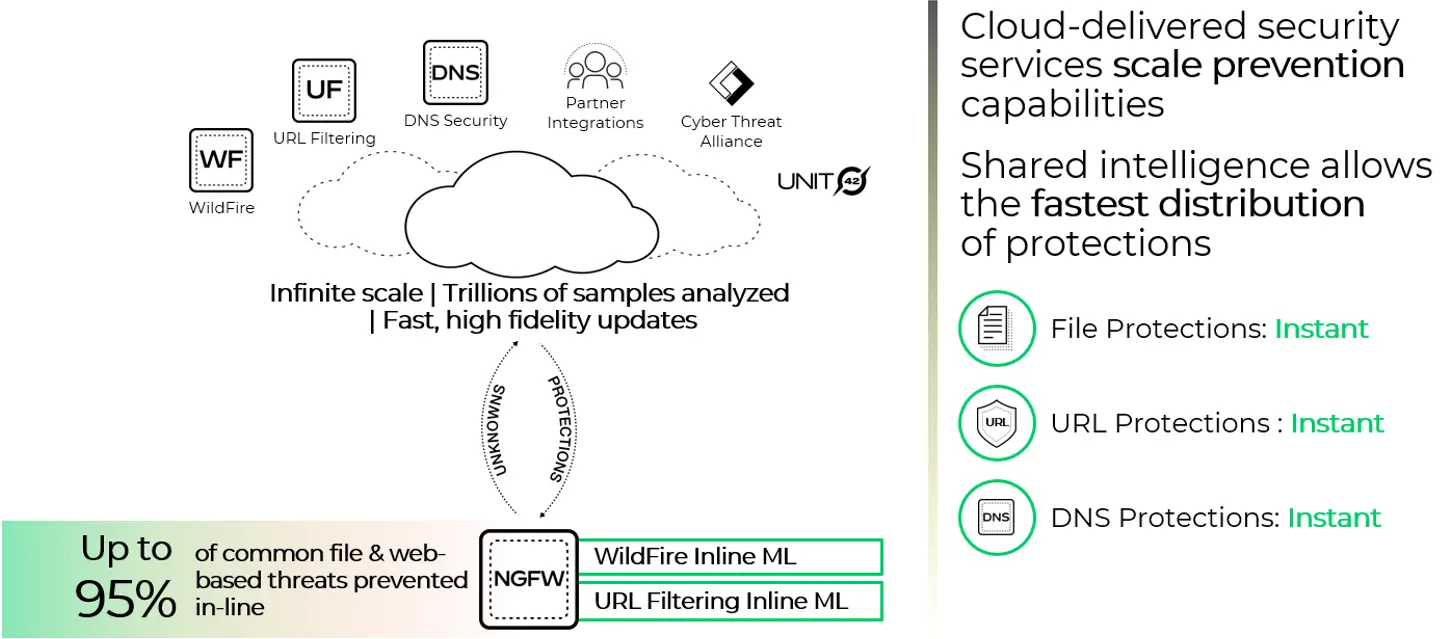
On the file level portable executable & DLL attacks and PowerShell attacks are immediately inline prevented. Other file types that are not known are uploaded to Wildfire and signatures are delivered as they are created. Pre-PAN-OS 10.0 WildFire update packages are generated every 5 minutes and firewall checked every minute is now transformed into realtime update streams with signatures. Going from about 5 minute signature updates to updates withing seconds to stop unknown malware files.
IoT security
More and more IoT device are connected into traditional IT networks. Most of the are not managed by IT and even IT is not aware about the amount of device connected. Creating a risk to the business because most of those IoT devices do not have security build in, running on outdated operating systems and are not integrated by the best practices.
- Massive increase in connected devices: 30% of devices on enterprise networks today are IoT
- Pose a huge security risk: shipped with vulnerabilities and difficult to patch, yet have unfettered access
- Securing IoT devices is hard: incredibly diverse devices; traditional IT security controls do not work
Starting PAN-OS 10.0 it is possible to start using all Palo Alto Networks firewalls, even VM-series & cloud services, as a probe in your network to gain insights about the IoT devices connected.
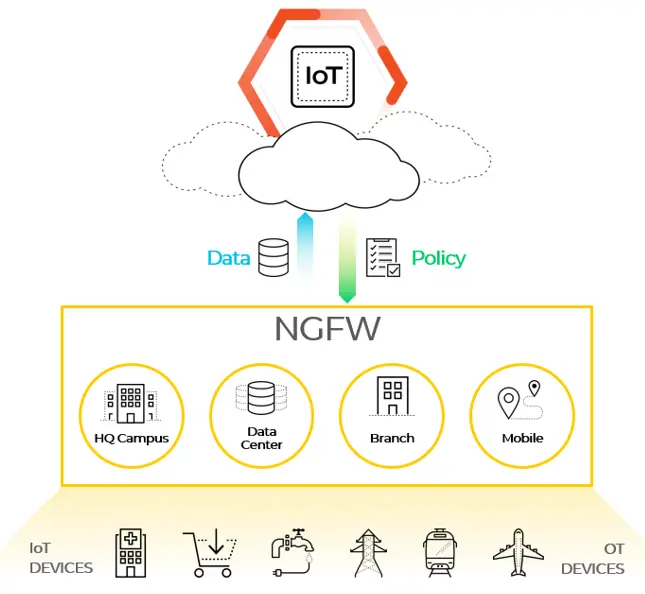
This will make it possible to:
- Reduce the business risk
- Visibility across the entire enterprise on IT & IoT
- Operation cost control because no additional appliances needed
- No risk in added latency on the network or new technical challenges
Using the IoT security subscription will provide you:
- Asset overview of all connected devices and details
- Assessment of the IoT risk
- Possibility to creates security policies based on device-id
- Prevention of the know threats
- Detection and response when devices are changing their behavior.
Decryption for TLSv1.3
Today encrypted traffic became the norm. More and more new malware campaigns are using a type of encryption to conceal the activity.
Deploying decryption is not so easy and should be done in steps to level up the security. This will bring the prevention capabilities back on track to protect your organization.
Modern applications and websites are using now TLSv1.3 and are adopting http/2 to provide security and performance. So, it is important to inspect https/2 (started in PAN-OS 9.0) and now in PAN-OS 10.0 also TLSv1.3 can be decrypted. This ensures that all the security subscriptions of the Palo Alto Networks firewall can do their inspection.
To help enabling the decryption new visibility and troubleshooting is provided within PAN-OS 10.0.