
9 February 2023
This is our response to the latest joint cyber security advisory (Alert AA22-040A) jointly authored by the cyber security authorities in the United States (FBI), the Cyber Security and Infrastructure Security Agency (CISA), and the National Security Agency (NSA), Australia (The Australian Cyber Security Centre (ACSC)), and the United Kingdom (National Cyber Security Centre (NCSC)).
The advisory warns about the increased global threat of ‘Ransomware’ against critical infrastructure. We welcome this coordinated warning and endorse the findings and guidance included, much of which resonates with our own observations and guidance over the last few years.
In this blog post, we aim to make you aware of the concerns raised by the government agencies and add some of our own thoughts and observations to complement their work.
Orange Cyberdefense is observing this threat very closely and has increased its research capabilities over the past 2 years to understand the issue better. Since January 2020 we have been actively documenting every victim that was publicly been revealed on so-called ransomware leak sites on the dark web, resulting in 3,921 documented cyber extortion victims between January 2020 and January 2022. Note that these are confirmed ‘end state’ victims, where systems have been compromised, data encrypted or stolen, and the victim publicly revealed on the criminals’ sites. Thus, our numbers are much smaller than reported ‘attacks’, but are arguably more ‘meaningful’.
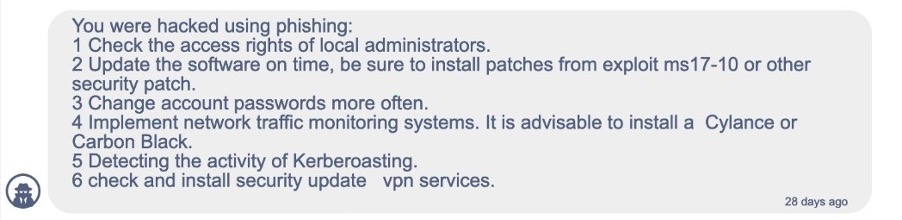
The CISA advisory recognizes the most used attack vectors are phishing, RDP exploitation, and software vulnerabilities. As can be seen below, threat actors often share their initial infection vector once the victim has paid. We have collected several of these so-called “security breach reports” provided by the threat actors at the end of a successful negotiation.
As the CISA advisory states, threat actors continue to evolve their criminal enterprise, outsourcing some components of the attack to third parties and renting out malicious software to others to increase distribution and impact. Ransomware-as-a-service is nothing new but seems to evolve more and more, making ransomware the prevalent threat as it is today.
In an interview, a representative from the recently surfaced Ransomware strain ALPHV explains: “In addition to high-quality software, for advanced partners, we provide the full range of services related to ransom[…]”. The statement continues by saying “We have made a truly new product, with a new look and approach that meets modern requirements for both a RaaS solution and high-class commercial software.”
As the ransom demanded continues to be paid by victim organizations or third parties such as cyber insurance, Cy-X will continue to evolve and spread due to its financial attractiveness.
The estimated cost of the current threat for the coming years has been widely reported in mainstream media and is predicted to skyrocket in the next decade. How these estimates are measured is a little unclear, but the fact is we continuously observe successful payments made by victim organizations. In fact, we’ve seen over $5 million (USD) in ransom payments made by several victims to just one single threat actor within a single week. And those are payments we know of. There is of course a higher dark number of victims and potential payments made we don’t see publicly revealed.
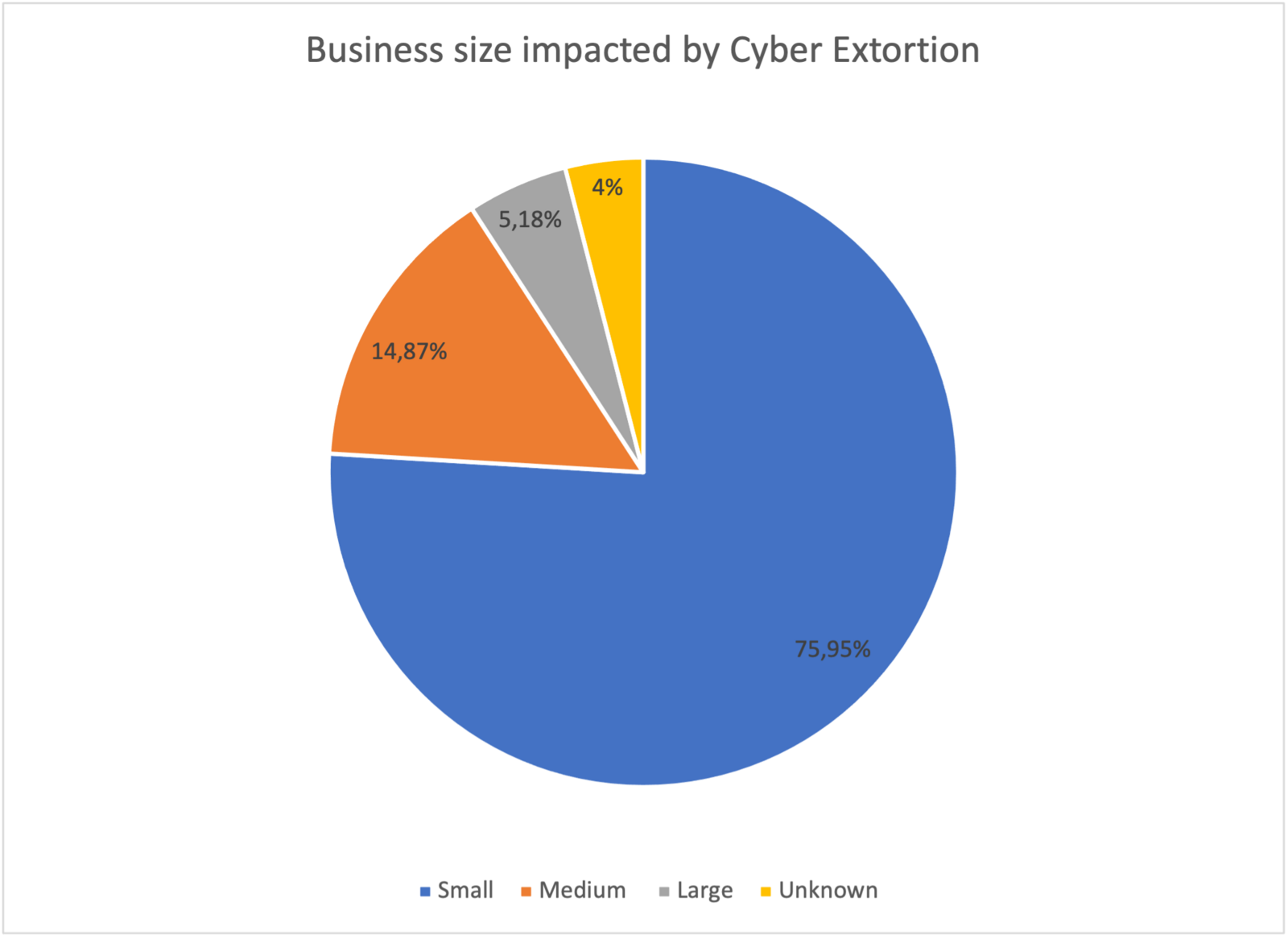
The CISA report comments that Cy-X has shifted away from “big-game hunting”, and we have previously noted a similar trend. Indeed, we are not entirely convinced Cy-X incidents are as ‘targeted’ as many suggest. The idea of “big-game” hunting or “mid-game” hunting has been oft-touted by analysts and media over the past 2 years. But our data suggests that the majority of victims are not represented by high-profile incidents like Colonial Pipeline, JBS Foods, and Kaseya Limited. Instead, we see most of the victims in business size Small and Medium business category (Small = 0-999 employees, Medium = 1,000-10,000 employees, Large = 10,000+ employees) as can be seen below.
We, therefore, have issues with the term “big-game” hunting. The dynamic nature of the relationships that Cy-X groups have with outsourced partners, such as Initial Access Brokers, suggests a more opportunistic attack pattern than a highly targeted one.
Like most literature on the topic, the CISA report uses the term ‘Ransomware’ to describe this crime. We have issues with this term also.
Threat actors are constantly evolving their tactics, techniques, and procedures to higher levels of efficiency, for example by automating different extortion techniques. We often see the terms “double-extortion” or “triple extortion” floating around to describe common and less common variations of the crime. Indeed, extortion has been so successful for criminals that these different forms of extortion will most likely continue evolving.
This is one of the reasons why we don’t think that the term ‘Ransomware’ sufficiently describes the full scale of this threat. We, therefore, propose to call it Cyber Extortion (Cy-X) instead. We understand Cy-X as a form of computer crime in which the security of a corporate digital asset (Confidentiality, Integrity, or Availability) is compromised and exploited in a threat of some form to extort payment.
Finally, it’s noteworthy to observe that the top 5 Cy-X groups of 2021 represent over half the incidents we recorded. However, off those 5 threat actor groups, only 3 are still active at the time of writing. Avaddon and REvil have been either partially arrested, re-branded, merged into new groupings, or may have simply retired (?). On the other hand, over the last few months we have registered up to 24 unique threat actor groups victimizing organizations around the globe.
This demonstrates that this ecosystem is very fast-moving and evolves very quickly.

In contrast to the tight group of just 5 threat actors dominating the landscape in 2021, we note how diverse the victim demographics are. For example, we find that businesses of all sizes fall victim, and several different industries are impacted.
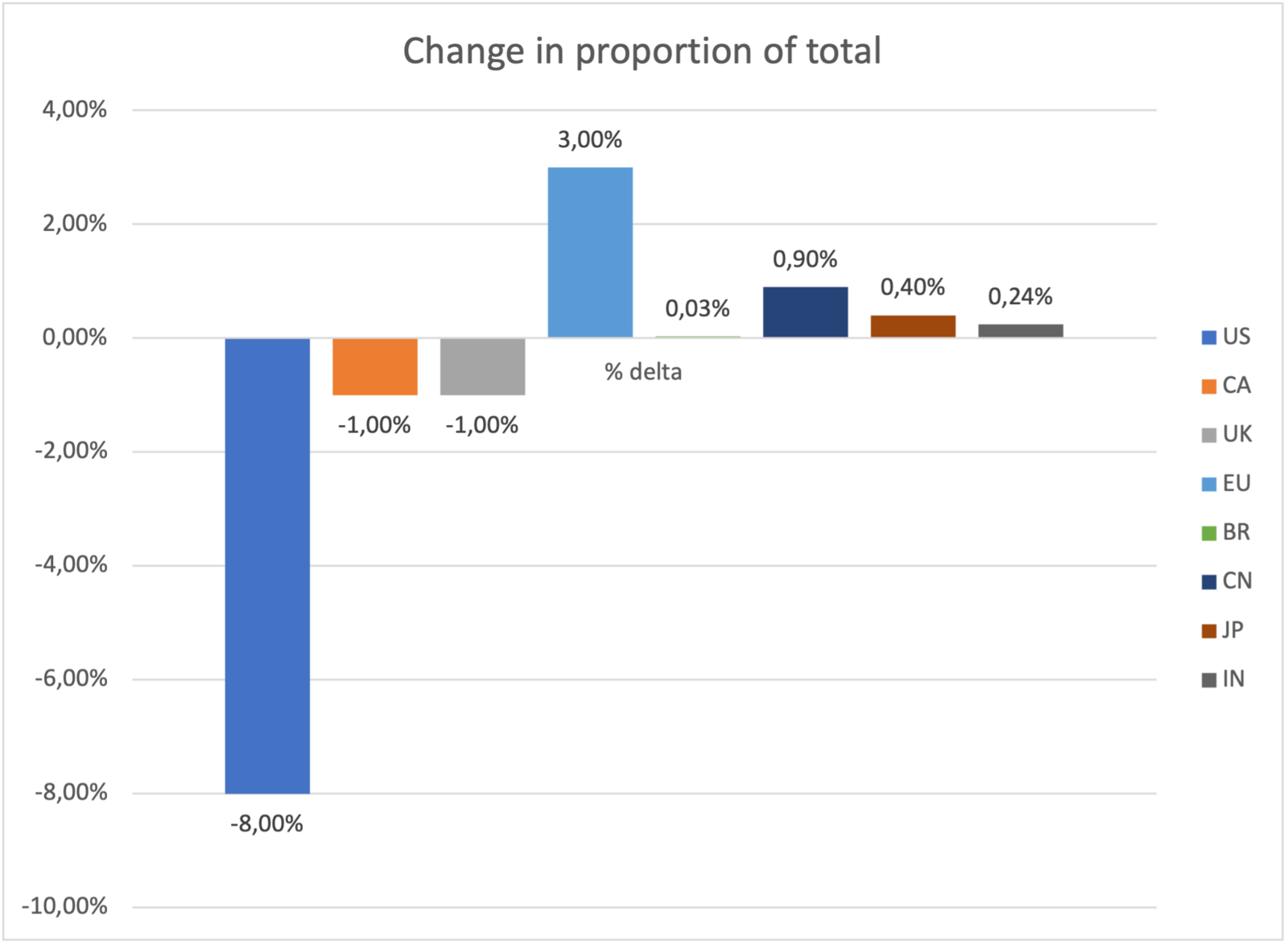
Notably, however, in our 2021 Security Navigator report, we observe important shifts in the countries the Cy-X victims are headquartered in. What we see is that the number of victims in non-English speaking countries is growing much faster than what we’ve seen English speaking countries. While we still see English-speaking countries such as the U.S., United Kingdom, Canada suffering more than any other, we’ve noticed that non-English-speaking countries such as China, Japan, India, and European countries have increased their relative share as victims in our database.
We agree with the conclusions in the CISA advisory that Cy-X has evolved over the past years and is an imminent threat to us as individuals, organizations and as a society. This is especially true when critical infrastructure and industries are impacted.
In January 2022, we noted that 9,82% of all Cy-X victims fell under the finance sector, followed by Construction with 6,25%, Educational Services with 6,25% and Healthcare and Social Assistance constituting 5,36%.
For more insight into our observations regarding Cy-X victimology, please see our 2021 Security Navigator report here.
The advisory list of recommendations for technical counter-measures. We generally concur with this, which has the added advantage of providing a generally robust level of cybersecurity.
For more detailed information, check the advisory here. Our detailed and complete vendor-neutral guidance on technical countermeasures can be found here.
By completing the perfect triad of insatiable demand, limited supply, and the smooth flow of value, cryptocurrencies had helped turn Cy-X into a viable cybercrime business model. When cyber insurance policies started paying the ransom on behalf of the victim, it created the perfect storm. Cy-X is a cybercrimes killer app and as far as we can see, it’s here to stay.
While addressing the systemic factors that create and perpetuate this problem are the only sustainable vaccine to the threat, reducing our own levels of visibility, vulnerability, and accessibility to reduce the likelihood of are an essential short-term measure.