Ransomware 2020: pay up or find your data online

Our malicious counterparts have yet again found a new way to increase their revenue and simultaneously leave victims of ransomware attacks in utter shambles.
Unpleasant, but predictable and manageable
Ransomware has been around for a while now, and after incident stories have been hitting the news regularly for the past years, most companies are now well aware of the possible consequences of a cryptolocker infection on their systems. Anyone can become the target of an attack: stolen credentials can be abused, an inattentive user can open a malicious mail attachment, an unpatched vulnerability can be exploited, and of course a zero-day is always a possibility.
Backups have thus far been the holy grail for mitigating the damage caused by ransomware attacks. All my files have been encrypted? No problem; let me just recover from my backup and we’re back on track in no time. The number of lost files is often minimal, and recovery time is usually acceptable. There have been cases where the backup system showed some hiccups, like being accessible (and thus deletable) from the network, using no or lousy (or stolen) credentials, improper configuration, incomplete coverage, etc. But usually, the companies with properly installed and configured backups could rest assured that a cryptolocker infection could not cause that much damage and that it would not be necessary to pay any ransom.
Upping the ante
Apparently, these limited successes for the victims have been a source of frustration for the friendly ransomware owners. Even though they are trying their best to provide a modern decryption platform (see image below), and even full-blown help-desk services, too many “clients” have been refusing to pay their ransom, and would rather take recovery into their own hands, or would, in some cases, rebuild from scratch instead paying any amount of bitcoin.
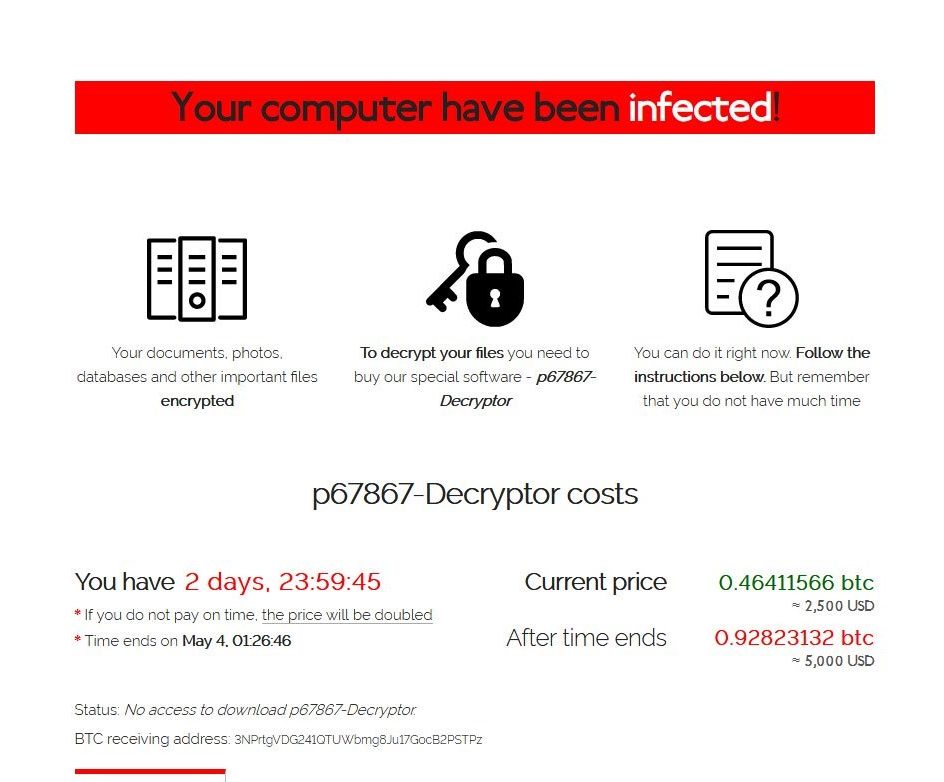
Since the end of 2019, at least one hacker collective has decided to straighten out this issue by applying some new tactthics to twist the victim’s arm into paying the ransom. Instead of merely decrypting the data, the Maze ransomware first transfers it to the attacker’s systems. Victims that refuse to pay get threatened with the release of their company data; it can be sold to the highest bidder or released into open source.
Ransomware developers have been warning victims about this possibility for a while, but up until now, such claims had never been substantiated. This unfortunate evolution might mark the beginning of a new chapter in the book of ransomware, starting with the story of Allied Universal. This chunky security firm based in the United States got breached and infected by Maze ransomware. Being a self-respecting security player, Allied Universal chose to recover without paying the ransom of 300 bitcoins.
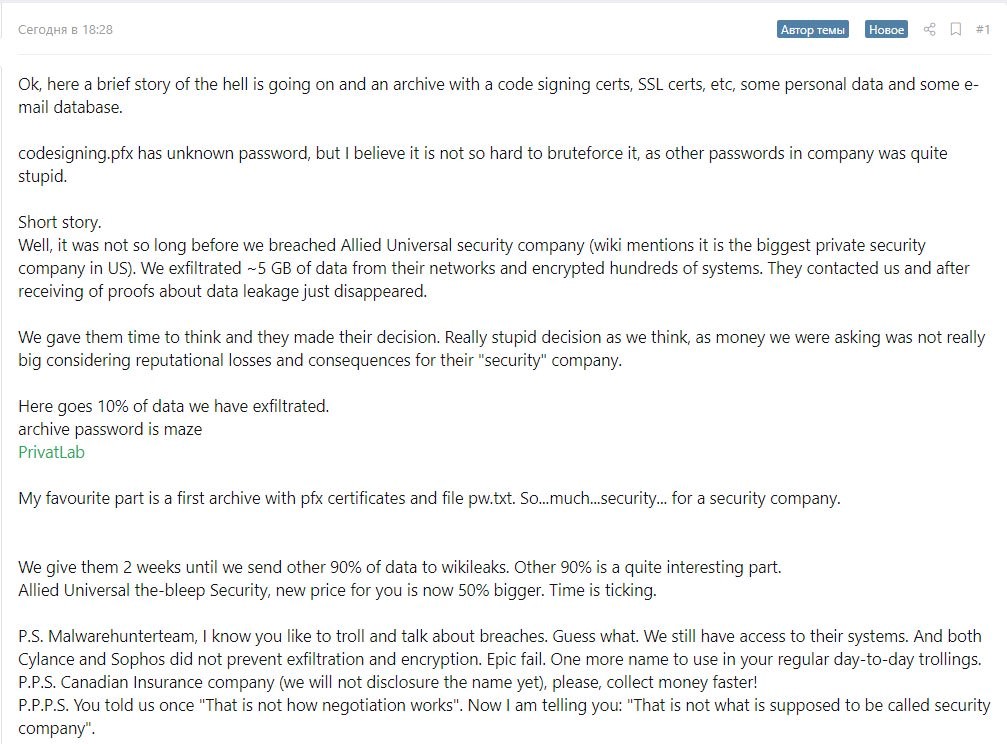
Team Maze, going by the name TA2101, threatened to make the breach public if Allied Universal failed to pay up. Since the threats went unanswered, TA2101 contacted security researcher Lawrence Abrams of BleepingComputer, to get him to publish an article about the Allied Universal breach, while providing some screenshots proving their access to the internal systems. Later on, the Maze actors added threats of conducting a spam campaign using Allied Universal’s domain name and e-mail certificates. In their communication, the hackers collective mentioned how Allied Universal really dropped the ball on their internal security by storing passwords in a plain text file named “pw.txt.”
BleepingComputer chose not to cooperate with the hackers, which prompted them to eventually publish a link to 700MB worth of internal Allied Universal data on the BleepingComputer forum, and on a Russian hacking forum. The message on the Russian forum is shown below (source: bleepingcomputer). It’s unclear whether or not this has finally prompted Allied Universal to bow to the threats, and pay the now 450 requested bitcoins (adding up to about $3.8 million).
Mazenews
It seems, however, that the wrestling competition with Allied Universal provided the hacker collective TA2101 with some insights on how to go about applying pressure to companies to pay the ransom. Instead of relying on news websites and forums to do the naming and shaming, they decided to simply put up a handy website of their own.
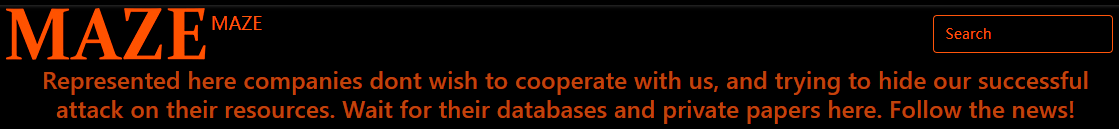
For a few weeks, anyone could access this site and check out which companies had been victimized by Maze, and had refused to pay the ransom. The articles of each breach listed the lock date, locked devices (hostnames), IP addresses, and total amount of data locked/exfiltrated. In some cases, actual documents were added as well, to show that they mean business.
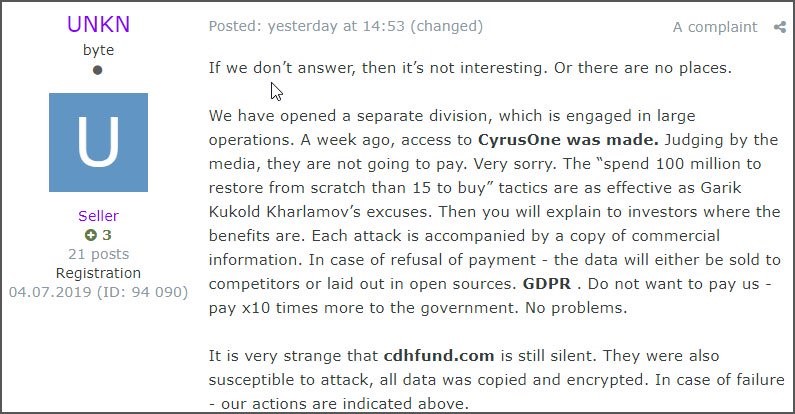
One of the victims, Southwire, where 120GB of data was stolen for a ransom of 850 BTC, sued the Maze team for the data theft and publication, which made enough fuss to make the provider take the website down. This has put a temporary end to the data publications, but chances are slim that this will put these kinds of practices to a full stop. Another player in the malware business, UNKN, known for deploying the Revil/Sodinokibi ransomware, has indicated similar intentions on online forums (see image. Source: bleepingcomputer)
Next to the public naming and shaming of the victims, which causes considerable reputation damage, default exfiltration of data before encryption turns a ransomware infection into a full-blown data breach. Even if the victim plays along and pays up, the data has still left the company network, and there is absolutely no assurance that the malicious actors will neatly delete the data without looking into it or spreading it. The data can include Intellectual Property, or Personally Identifiable Information, which makes GDPR applicable, along with its hefty fines!
We can conclude that these evolutions are pretty scary at best and that the security teams will need to step up their game to protect their networks. Awareness training, intrusion detection, layered defenses, etc. A well-implemented security plan will become indispensable in the near future.
If you want to make sure your network is ready for these challenges, feel free to contact our CyberSecurity Advisory team on expert@be.orangecyberdefense.com .
Discover what our advisory team can do.
Sources:
- https://www.bleepingcomputer.com/news/security/another-ransomware-will-now-publish-victims-data-if-not-paid/
- https://www.bleepingcomputer.com/news/security/allied-universal-breached-by-maze-ransomware-stolen-data-leaked/
- https://www.bleepingcomputer.com/news/security/maze-ransomware-demands-6-million-ransom-from-southwire/
- https://www.bleepingcomputer.com/news/security/the-week-in-ransomware-may-31st-2019-maze-sodinokibi-and-more/
