

Securing Operational Technology
What all decision-makers need to know about improving protection of OT in a rapidly evolving threat landscape.

Across the world, industries and critical infrastructure are rapidly digitalizing. As connectivity and automation grow the Operational Technology systems that are vital for controlling all kinds of physical operations are becoming deeply integrated with IT networks. This unlocks new opportunities but it also introduces significant cyber risks.
While IT Security has become a well-understood priority at the executive level, OT Security often remains overlooked. In today’s threat landscape this poses a safty hazard.
In this perspective it’s importand to understand that OT Security is not just a issue that can be handled by technical specialists alone – it’s a strategic business imperative.
Securing your organization’s OT environments and strenghtening your long-term security posture is about understanding what’s at stake for your business – and leading the way to a more resilient organization. It’s about understanding that OT Security is essential for safeguarding business continuity as well as your revenue, reputation, resilience and safety.
Waste no more time – now is the time to act, because safeguarding your Operational Technology is safeguarding your future.

In today’s hyper-connected world, Operational Technology faces unprecedented vulnerabilities. As organizations accelerate digital transformation, communication between IT and OT-systems increases dramatically, exposing critical infrastructure to a new wave of cyber threats due to this critical link.
Despite decades of IT Security evolution, OT Security often remains overlooked, creating a blind spot with potentially devastating consequences. This poses both a huge risk and a safty hazard for your business.
Get in touch with our OT experts
We often tend to think of “Operational Technology” as technologies controlling industrial processing and production – the very name implies this. But the field of OT is far wider than that. In fact, OT-systems can be found in just about any kind of industries and organizations.

Andreas Jacobsson | OT Solution Architect
In today’s interconnected world, OT Security is no longer just an operational concern – it’s a strategic imperative. Therefore, leaders must prioritize resilience, foster collaboration between IT and OT, and embed security into the very fabric of their digital transformation.
What is OT Security?
Operational Technology (OT) includes the hardware and software that control physical processes –think of it as the nervous system behind industrial operations. Unlike traditional IT-systems that manage data, OT-systems monitor and control assets like electricity grids, water treatment plants, manufacturing lines, and more.
Why is OT Security Important?
OT Security aims to protect these critical systems from cyber threats that could cause operational disruptions, safety hazards, or environmental damage. With evolving legislation like NIS2 and DORA, higher levels of security are essential to ensure compliance and safeguard vital infrastructure

Mitigating these risks requires a tailored, comprehensive cybersecurity strategy, employee awareness, and continuous assessment.
Every organization faces unique challenges, but common OT Security risks include:

Legacy Systems: Outdated software lacking modern security protections, difficult to patch or update.

Security as an Afterthought: Systems designed for availability and efficiency, not security.

Lack of Visibility: Insufficient monitoring of security measures and system activity.
Regulatory Gaps: Limited awareness or enforcement of industry standards and compliance requirements.

Overlooked Systems: Critical secondary systems, like servers or building management, often remain unprotected.

Remote Access Vulnerabilities: Growing connectivity with partners and suppliers increases attack surfaces.

Physical Consequences: Attacks can lead to safety hazards, environmental damage, or operational shutdowns.

We get an updated overview of the OT environment and find opportunities for improvements in OT Security. At the same time, we now see great potential for both simplification and improvement in the management and use of several different systems, in a relatively simple and economical way. Truly a "win win" for everyone.
– Patrick Gillmor, Automation and Process Engineer, Renova Miljö AB


Unplanned Downtime with Heavy Financial Impact
For many organizations, operational uptime directly correlates with revenue. While cyberattacks often target interconnected IT-systems, OT environments are increasingly being targeted directly. Successful breaches can halt production, delay supply chains, and incur contractual penalties. Unlike IT-incidents that may result in data loss, OT failures can cause physical disruptions – impacting manufacturing lines, critical infrastructure and vital societal functions. A critical step to mitigate these risks is understanding how IT and OT-systems are interconnected – enabling continued operation even during security incidents.
Shortage of Skilled OT Security Experts
The demand for OT Security specialists far exceeds supply. Many organizations struggle to find professionals with both cybersecurity expertise and industrial process knowledge, making effective OT Security difficult to implement.
The IT-OT Communication Gap
One of the biggest hurdles is the disconnect between IT and OT-teams. While IT focuses on data integrity and confidentiality, OT prioritizes system availability and safety. This misalignment often leads to:
Conflicting security priorities
Organizational challenges
Delayed incident response
Lack of clear ownership and accountability
Limited cross-domain expertise
Supply Chain Risks and Third-Party Vulnerabilities
OT environments rely on complex supply chains, including vendors, contractors, and legacy equipment providers. Attackers exploit these external connections to access OT networks. To reduce this risk, organizations should:
Update procurement requirements and security specifications
Strengthen service agreements with clear accountability for OT Security
Enforce strict access controls for third parties
Monitor for anomalies indicating supply chain breaches
Require a Software Bill of Materials (SBOM) from suppliers to improve vulnerability management and incident response
Historically, cybercriminals have exploited weaknesses in IT Security to access valuable digital assets – encrypting data, stealing intellectual property, or damaging critical infrastructure. However, today, highly sensitive and essential OT environments are increasingly becoming prime targets due to the growing communication between IT and OT networks.
High-profile cyberattacks have demonstrated the devastating real-world consequences of OT Security failures. The financial losses, reputational damage, and regulatory penalties underscore why OT Security is now a business-critical priority.
As regulations like NIS2, IEC 62443, NIST CSF, ISO 27001/2, and CIS tighten, organizations must proactively adopt security measures to meet these evolving standards. Compliance is no longer optional – it’s essential for resilience, trust, and operational continuity.
Failure to secure OT environments can lead to:

Martin Blak | Senior Trusted Advisor
The path to a resilient and secure future is paved with strategic vision and decisive action. OT Security is not just an IT issue – it’s a core business risk that demands leadership, collaboration, and a forward-thinking mindset.
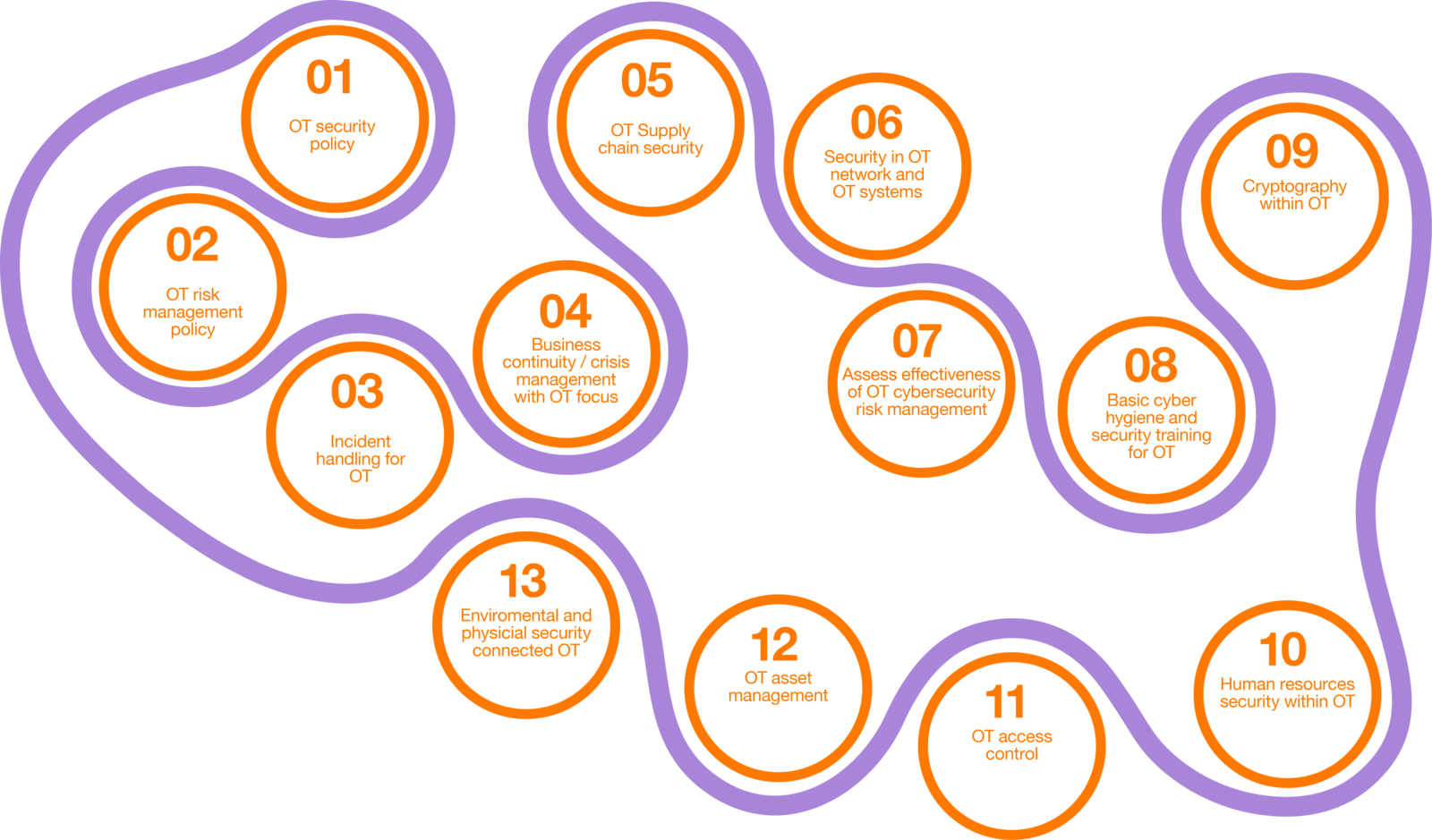
As OT differs from IT in many critical ways, a straightforward copy-paste of IT Security measures is not an option. Instead, an OT-specific governance frame-work is essential for managing OT Security risks effectively.

Orange Cyberdefense’s long pedigree in OT was invaluable – their deep understanding fostered trust, encouraging open dialogue and engagement throughout the assessments, which naturally led to upskilling and an accurate 'as-is' of our industrial environment.
– Fawzi Aiboud Nygren, BISO, Volvo Group Trucks Operations

OT environments often evolve through organic expansion where new systems and components are continuously added without a cohesive, overarching security architecture. IT makes it difficult to maintain visibility, consistency, and control over the full attack surface, which is typically compromised by attack vectors like:
Strong OT Security depends on risk-based identification of all mission critical technology. In this process support systems can easily be overlooked. To reduce the risk against your complex OT environments and avoid the most common attack vectors to stay ahead of threats while building a resilient OT Security posture, make sure to tick these boxes:
As cyber threats evolve, OT environments become increasingly attractive targets. While most attacks currently start in IT and spread to OT, dedicated OT-malware has already been detected, especially in conflict zones.
Relying on a reactive approach – responding only after an attack – risks severe operational, environmental, financial, and reputational damage. Instead, organizations must adopt a proactive, prevention-focused strategy.
Implement Risk-Based Security: Continuously monitor and improve your OT Security posture. Maintain an inventory of all assets, assess risks, and prioritize investments to protect the most critical systems.
Taking these steps helps you stay ahead of emerging threats and build resilience against future attacks.
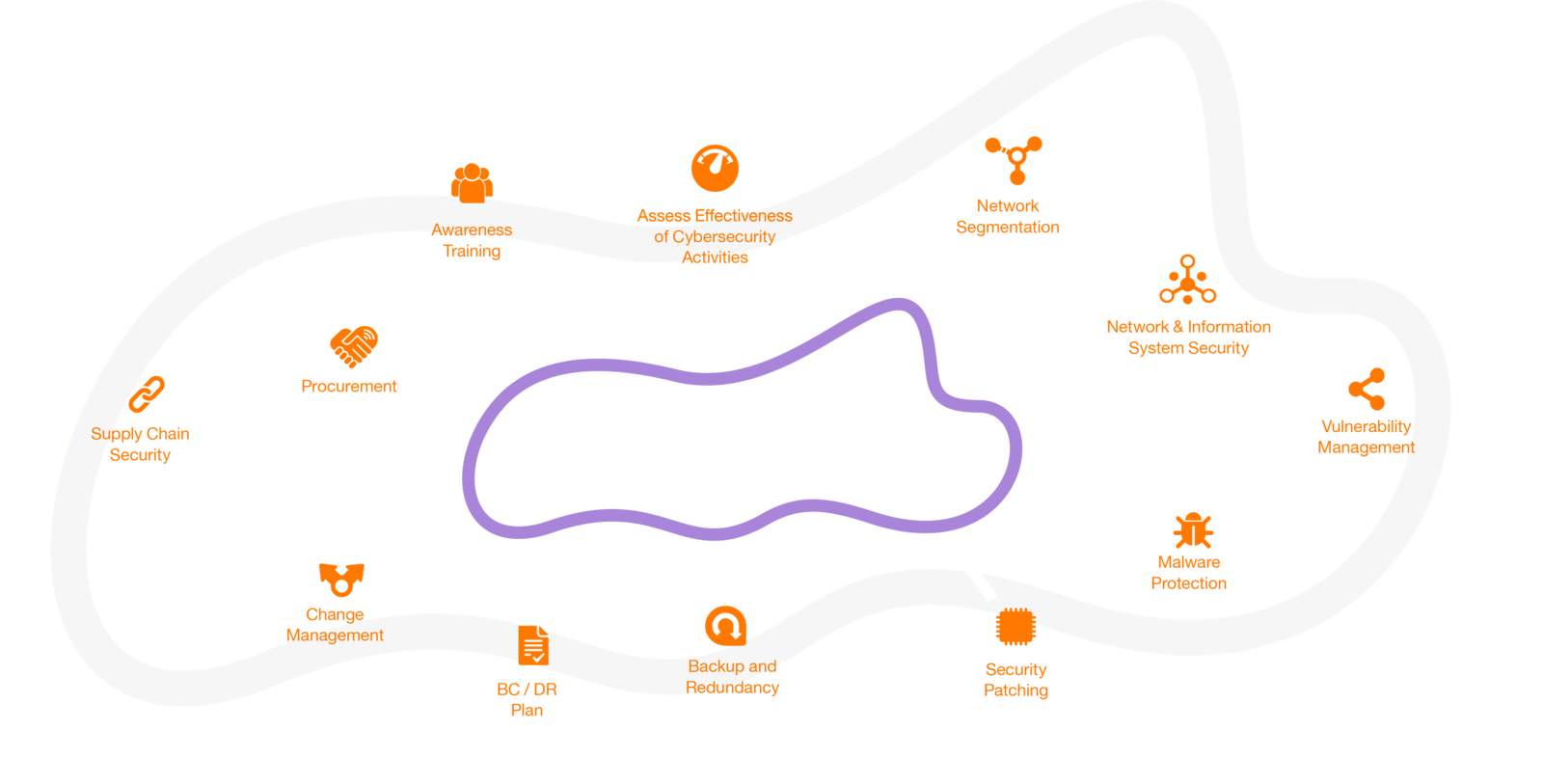
Secure remote access and third-party integrations.
Many cyberattacks originate from unsecured remote connections or third-party vendors. To mitigate these risks, organizations should.
Deploy network segmentation and multiple layers of defense.
Traditional flat OT networks are highly vulnerable to cyber threats as they typically allow access to all assets. Implementing network segmentation and layered security controls significantly reduces risk.
Focus on employee awareness and training.
Human error remains one of the largest vulnerabilities in OT Security. Continuous education and training programs help employees recognize and respond to threats effectively.
Continuously monitoring and proactively use of threat intelligence.
A proactive approach to OT Security requires real-time monitoring and intelligence-based threat detection. These are the cornerstones to stay ahead of threads.
Prepare your crisis management and plan for recovery.
Time is crucial – especially in OT, where any good security strategy must include plans for getting back on track as fast as possible.

For decision-makers, understanding the importance of OT Security is the first step toward creating a resilient, secure industrial environment. Key takeaways include:
Get in touch with our OT experts
Carsten Lyth | Business Area Manager, OT Security
Effective OT Security is a business enabler, not just a technical necessity. It requires visionary leadership, proactive risk management, and a unified approach across all levels of the organization. Those who lead with foresight will safeguard their operations and secure their competitive advantage.


Conducting a security assessment is not just about identifying security gaps - it’s about building a resilient foundation for the future. By evaluating our OT Security practices, we’ve been able to implement meaningful improvements, ensuring stronger defenses and compliance with evolving standards like NIS2 and NIST.
– Julian Beauregard Camp, Subject Matter Expert OT, EcoDataCenter
Industry 4.0 is transforming the landscape with increased connectivity, automation, and data-driven operations. In this evolving environment, artificial intelligence (AI) is no longer optional – it’s a strategic necessity for OT Security.
AI enables real-time analysis and decision-making beyond traditional methods. Instead of relying solely on predefined rules, AI learns what “normal” looks like within your systems and detects deviations that could indicate cyberattacks, malfunctions, or insider threats. This is especially critical as operational systems become more autonomous and less dependent on human oversight.
However, threat actors are also leveraging AI – developing malware that evades detection, adapts to environments, and targets critical infrastructure with precision. To stay ahead, defenders must harness AI with the same ambition, applying it to threat detection, response, and strategic forecasting.
With forward-thinking AI security, Industry 4.0’s promise of innovation becomes a resilient, adaptive, and secure reality.
Looking ahead, the questions you must ask are:
As organizations accelerate digitalization and adopt new technologies, OT Security must evolve to address emerging threats.
Here are the key trends shaping the future of OT Security:


Deeper IT-OT Integration
Increasing communication between IT and OT for efficiency raises security risks. Effective strategies must seamlessly bridge both environments to protect against threats.

Stricter Regulations
Future regulations will demand higher security standards in OT. Organizations need to proactively meet compliance requirements to avoid penalties and operational disruptions.

Skills Gap and Training
As OT Security complexity grows, so does the need for specialized expertise. Investing in training and recruiting skilled personnel across IT and OT is essential.

Architectural Changes
Concepts like Zero Trust are being adopted in OT environments, requiring organizational and technical adjustments to ensure no device or user is implicitly trusted.

Growth of IoT and Industry 4.0
The rise of connected IoT devices expands the attack surface, demanding advanced security measures to protect these endpoints and maintain operational integrity.

Evolving Threats and Attack Vectors
Cybercriminals are becoming more sophisticated, using ransomware and supply chain attacks. Future OT-systems must be prepared to detect and defend against these threats.

AI and IoT: Opportunities and Risks
While AI and IoT boost operational efficiency, they also introduce vulnerabilities. Securing these endpoints is critical as their proliferation continues across industrial environments.
To prepare for future industrial cyber threats, organizations must embrace a forward-thinking mindset.
This involves:

To strengthen IT- and OT Security across Europe, the EU has issued the NIS2 directive, and it has been implemented in national law by the 27 EU countries. As the directive is particularly focused on organizations working with critical infrastructure, it has a strong emphasis on OT Security requirements.
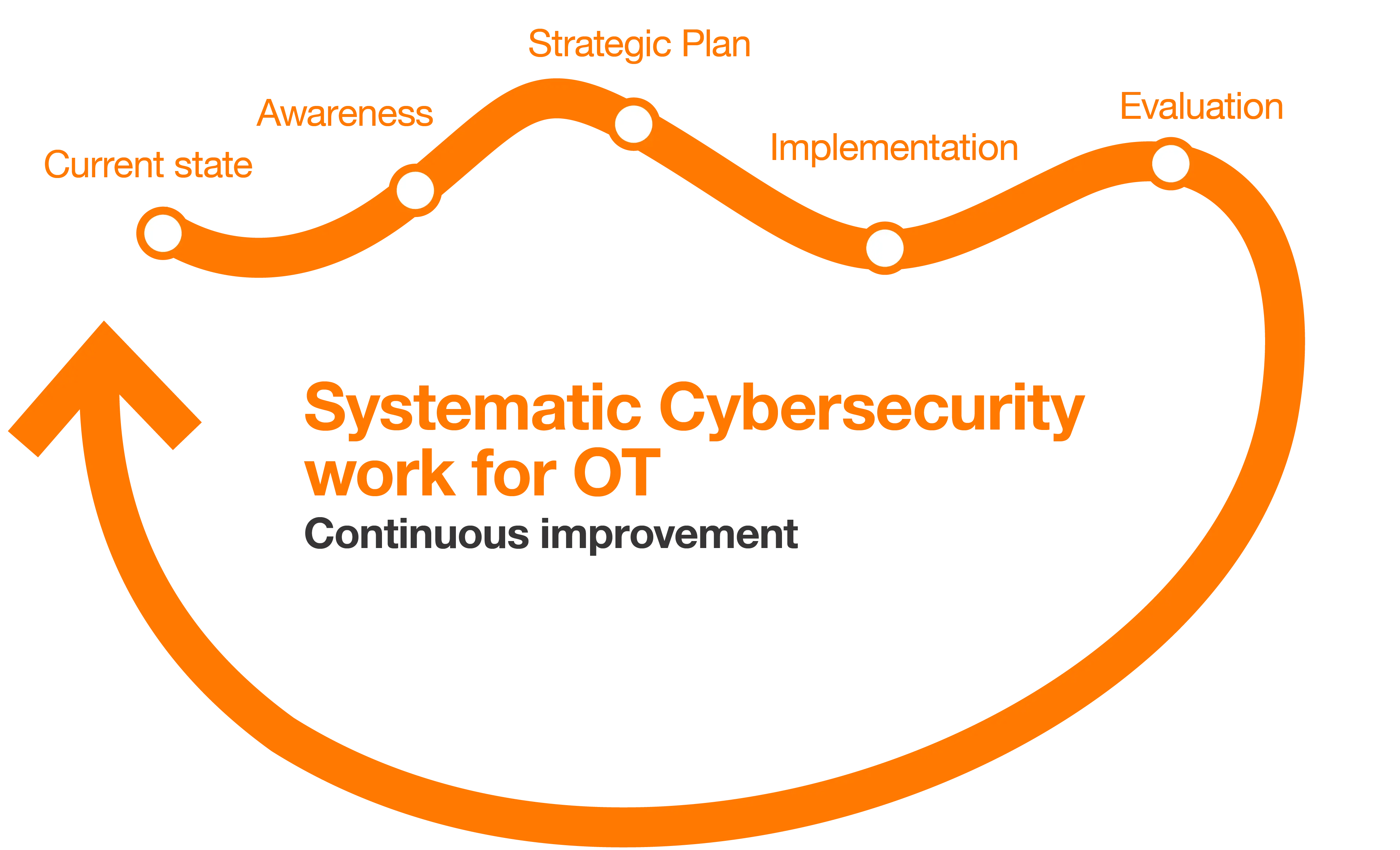
Start by building a strategic roadmap
Any successful OT Security strategy should be built on a clear roadmap that includes short-term and long-term objectives that align with the business goals, address key vulnerabilities, and set out the steps needed to achieve a secure OT environment.
Start by assessing the current security posture, identifying critical assets, and implementing a risk management framework. Over time, the roadmap should evolve to accommodate new technologies, business needs, and emerging threats.
How to get started with OT Security
If you’re just starting your OT Security journey, the first step is to assess your current risk landscape. Work with experts to identify potential vulnerabilities and begin implementing the necessary solutions to safeguard your OT environment. Leverage resources like OT Security Assessments, Ethical Hacking, and Managed Security Services to accelerate your security strategy.

At Orange Cyberdefense, we recognize the unique challenges of OT Security and the critical differences between OT and IT environments. Because these domains require tailored approaches, a simple copy-and-paste strategy won’t suffice. Our expertise spans multiple industries and sectors, enabling us to deliver solutions that safeguard both the physical and digital aspects of your OT environment to the highest standards.
Partner with us to build a resilient, secure OT environment – protecting your operations today and preparing for the challenges of tomorrow.
Our Managed Security Services provide continuous protection through real-time monitoring, threat detection, and incident response – ensuring your OT systems stay secure and operational. Our offerings include:
With a shortage of skilled OT Security specialists, we offer a different approach. Our experienced team of OT Security consultants across the world, and local OT specialists in Denmark, Sweden and Norway, is ready to help you significantly enhance your defenses. Key services include:

While IT Security has evolved over decades, OT environments often rely on legacy systems with limited monitoring and low network visibility. Understanding what communicates with what – and why – is crucial to building a strong security foundation. Our OT Security Assessment provides the insights needed to identify vulnerabilities, prioritize risks, and develop a clear roadmap for improvement.
What you’ll receive:
What we offer:
When should you consider an OT Security assessment?

As a recognized leader in Managed Security Services, we bring industry-standard assessment methods and proven expertise to help you build a resilient OT environment. Let’s take the first step toward a safer, more secure future - together.
At Orange Cyberdefense’s OT Showroom in Lyon we offer an extensive, tailormade, interactive, hands-on experience where decision-makers can witness OT Security in action. This unique facility showcases the latest OT Security technologies and provides a real-time demonstration of how our solutions work to defend critical systems. Visitors can engage in practical exercises, observe simulated cyberattacks, and learn how to address security challenges in their own environments.
Learn more