
5 April 2023

The short answer is that not every company has it’s own SOC so if they do not, MDR is an attractive proposition. Not everyone is looking at MDR services for the same reason, though, so it’s not that simple to answer. Overall, companies look towards MDR for some of the following reasons:
Some companies have their ownSOC and are perfectly happy with that solution. But for others, it’s impossible to provide an equivalent function themselves, for the reasons we mentioned earlier: time, skills, money. When we look at small companies, for example –,and let’s take the UK market – the average cost of a security analyst is somewhere in the region of £50k per year[i]. To deliver 24×7 you will, need at least 5 or 6 analysts on shift, so already (without recruitment, training, benefits, etc.) that is £250-300k per year. And of course, you need to go and find those people. That’s without considering the necessary tools that they need, the processes that need to be developed, and the time it takes to be operational.
An MDR provider will have resources. They will have a dedicated function just for Managed Detection and Response (often including a team that will run the MDR tooling as well, which is less work for businesses).
Caution: some non-specialist Managed Security Services (or even Managed Services) generalists are trying to get into Managed Detection and Response having seen the growing market. It’s not easy to deliver good Service on MDR. It’s far from a commodity so, if you choose this option, pay attention to the experience and the focus that the MDR provider brings to the function (and therefore to you, as a customer).
Analysts’ reports can be innovative tools to help you choose the best MDR provider for your business. The last one in date, Gartner’s Market Guide for Managed Detection and Response Services, was published in August 2020 and lists Orange Cyberdefense as a Representative Vendor for MDR services.
MDR providers have many customers from whom they can glean global threat intelligence. Something that is challenging to recreate in a SOC running inside a single business. It’s not just a case of having the data but knowing how to analyze it. Research and Development functions are crucial to unlocking the potential of threat intelligence.
Any MDR provider of a mature state will have 24×7 resources, fully staffed with security analysts. This is a real advantage for any business because the MDR provider can share those 24×7 resources across customers, thus bringing down the cost of such a function.
Stay vigilant and be careful of providers that use automation or non-security analyst shift workers. This can make for an inconsistent experience outside office hours.
Our analysis would not be fair if we were only focused on the positive side of MDR. With any service, there are things you need to know as a client.
An MDR provider will never have the same deep-level business understanding as… you. And this is why coordination between your MDR provider and your staff is critical. A good MDR provider will have dedicated experts. They act in a Technical Account Management capacity or Consultant capacity to collaborate with the Security and IT team to bring that business context into the Service and customize it over time, again and again.
Also, an MDR provider often does not have the same level of access to IT systems as internal staff and, as such, may not be able to respond to an incident as quickly as the internal team would. This needs to be addressed at the beginning of the collaboration, to find ways to shorten the response time if an attack were to occur. An example is to have at least the capability to provide the MDR team with the ability to isolate endpoints or lockdown accounts used to perpetrate attacks (or take this function and the accompanying tools to do so as part of the Service).
As in any business, not all MSSPs are equal. There are many different ways to produce a Managed Detection and Response service. And the outcome can be very, very different. Some MSSPs do not provide enough value. They just send alerts that businesses still need to do a lot of investigation on themselves and, as such, are not lightening the load on the company which procured their services.
Some companies find themselves disappointed in the Service, only receiving emails like this: “There is a critical alert on your firewall, you should investigate this further.” It’s just one example of MDR at its worst. The good thing is that as time moves on and the market space is more crowded, MDR providers have to do better and provide a greater depth and range of services and outcomes for their customers.
When talking to customers, one of the first things we usually get asked is: “What can we do to make sure this is a success?“.
Without customer collaboration, MDR does not work. You get a service that is not customized, nor engaging and does not solve any problem. So, the first thing to do when you start with MDR is to work closely with the MDR provider and prepare yourself to receive the service. Remember – the one thing you will never outsource is in-depth knowledge of your business that only you have, and this is what your MDR provider needs. Look at how existing incident handling and incident response policies will work with using an external MDR provider and if they won’t – change them! You have to be ready and a good MDR provider will have advisory consultants on hand to be able to help you through this part too if you need it.
The next step is really to look at where to begin. Many companies still ask for a traditional, Managed SOC/SIEM combination.This used to be a natural pairing – you want proactive security analysis of events from your IT environment, then yes, you need a SIEM and a SOC team to manage it. This is no longer the case. In introducing the SOC Nuclear Triad as a concept, Gartner shared new ideas (back in 2015) that to achieve full visibility and maturity in security operations, SIEM was not enough anymore. In more recent times, has not only has this idea developed but also the concept that sometimes SIEM is not even the starting point.
If we go back to COVID-19 and the impact of the pandemic, for example, and the risk profile for most companies right now, securing the endpoint is hugely important. So Endpoint Detection and Response (EDR) solutions, often embedded within MDR services, become much more attractive (especially given their time-to-deploy/time-to-value compared with SIEM). We have also seen the evolution to extended detection and response (XDR) to enable even more of a “headstart” without needing a SIEM platform, to buy some time to plan for what you might want to do in 2 or 3 years and whether you then need to invest in further security analytics systems.
Having matured our services to the point where we can offer all of these options – either individually or, more powerfully, together as a full MDR proposition – Orange Cyberdefense has developed our Threat Detection Framework to help customers visualize what deployment of different service options looks like.
Explicitly modeled to their environment and the type of data they can provide us with, we work with customers to set target visibility across the critical phases of the kill chain and look at ways to help them achieve that. In building trust, transparency is key.
Gartner Market Guide on MDR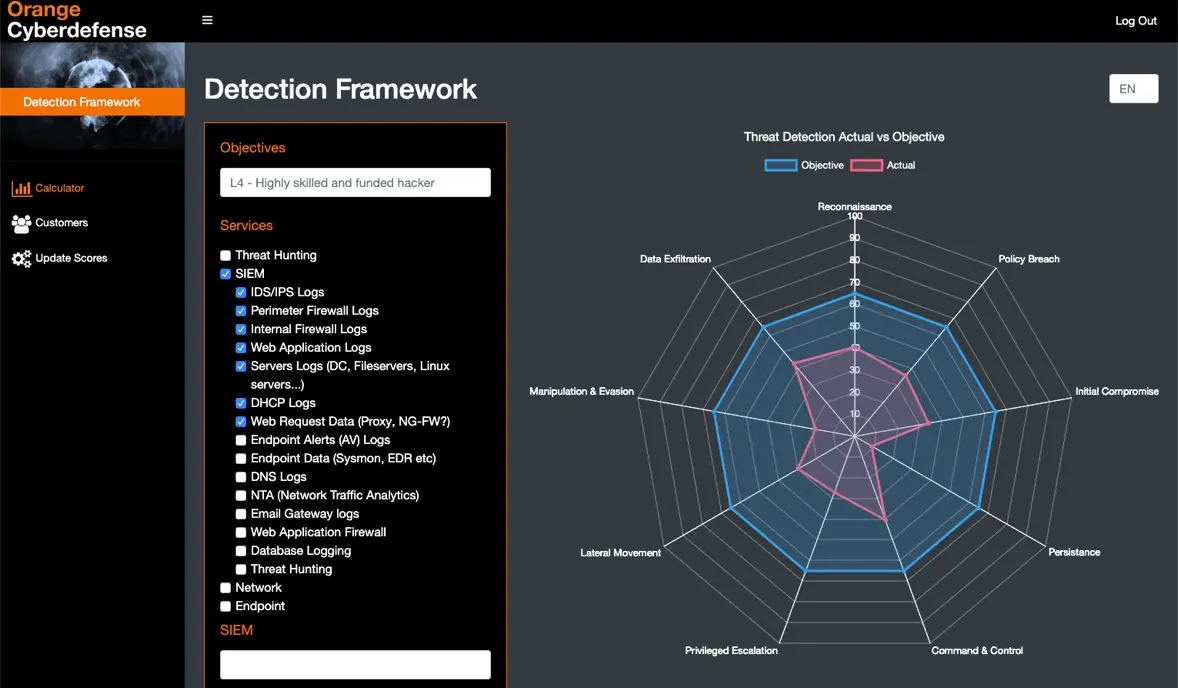
This framework aims to:
The framework is developed and actively used by our 11 CyberSOCs distributed worldwide (UK, Sweden, Poland, Russia, China, India, France, Netherlands, and Germany), and sales and services support in 160 countries. We offer global protection with local expertise.
If you want to know more, please use the contact form right here.