
1 July 2025
Security teams can only defend what they can see – and today, that visibility is being put to the test like never before. With cloud sprawl, mergers, third-party services, and shadow IT exploding across modern enterprises, understanding the full breadth of your attack surface has become a strategic imperative.
“External Attack Surface Management (EASM) isn’t just about scanning IPs or domains,” explains Nicholas. “It’s about continuously discovering how your organization actually shows up online, including the things you didn’t know were out there.”
From legacy domains still registered under past brand names to employee-provisioned cloud services outside IT control, the modern attack surface is vast and constantly shifting. “It’s simply impossible to map this manually,” he adds. “The only way to do this right is through intelligent, continuous discovery driven by platforms that understand who you are as a business, not just some IT infrastructure.”
As organizations move toward more proactive security models, EASM becomes a foundational capability. Why? Because modern SOCs aren’t just about responding - they’re about anticipating.
“In a modern SOC, the discovery of an external asset can’t be a manual event,” says Nicholas. “It needs to trigger an automated response: tagging, monitoring, protection, and even remediation - instantly.”
EASM enables exactly that. By integrating with threat detection platforms and vulnerability scanners, it feeds newly discovered assets directly into the organization’s protective layers. This tight feedback loop shortens the gap between identification and action, and reduces the risk of overlooked exposures.
“It’s not just about mapping the terrain,” Nicholas says. “It’s about automatically defending it the moment it appears on the radar.”
One of the biggest operational challenges with EASM? Noise. A platform that finds everything also risks overwhelming teams with false positives.
“There’s always a trade-off between discovery breadth and data relevance,” Nicholas explains. “The wider you cast the net, the more likely you are to pick up things that aren't yours — and that can drive up detection volume and platform costs if not managed properly.”
That’s why effective EASM isn’t just about discovery, it’s about smart filtering. Organizations need trusted partners or managed services that can continuously tune and refine asset data, ensuring only meaningful exposures are passed downstream into detection and response platforms.
“You need a system - and a team - that knows how to clean the data before it becomes a distraction.”
Traditional vulnerability management often focuses on known assets — those that IT has already accounted for. But in a world where anyone with a credit card can spin up a public-facing cloud app in minutes, that approach leaves too much in the dark.
“Let’s say you’ve configured your scanners to cover 70% of your known environment,” Nicholas says. “That still leaves a big blind spot. EASM fills that gap , so it can still flag unknown assets with exposures that need urgent attention.”
In this way, EASM complements traditional scanning, rather than replacing it. It acts as a radar, constantly sweeping for new terrain, and pushing critical findings into the organization’s managed vulnerability lifecycle when needed.
Nicholas compares it to navigating the Wild West of cybersecurity. “There’s so much out there that’s uncontrolled, unregistered, and unmanaged — the unknown unknowns. EASM brings structure and visibility to that chaos.”
EASM isn’t just about finding assets - it’s about understanding which ones actually matter. That’s where context becomes key.
“When we onboard customers, we go through a process of tagging and grouping assets by business importance,” says Nicholas. “That allows us to prioritise exposures based on risk – combining asset criticality, technical vulnerability, and real-world threat intelligence.”
This multifactor approach ensures that alerts aren’t just technically valid, but operationally relevant. Threat intelligence plays a key role too: if a vulnerability is actively being exploited in the wild, it climbs the priority list.
“Prioritisation is everything,” Nicholas insists. “Without it, you’re just adding more noise to the system.”
So how will EASM evolve in the SOC of the future?
“It won’t always be front and center, but it will be a core capability — deeply embedded in how modern SOCs operate,” says Nicholas.
As security platforms consolidate - combining exposure management, threat detection, and automated response - EASM will play a central role in feeding these systems the visibility they need to work. Especially in platform-driven models (like Microsoft XDR or similar), EASM becomes a key input that drives everything from attack surface reduction to real-time detection.
To illustrate the point, Nicholas refers to a mental model often used in SOC discussions — the “boom model.”
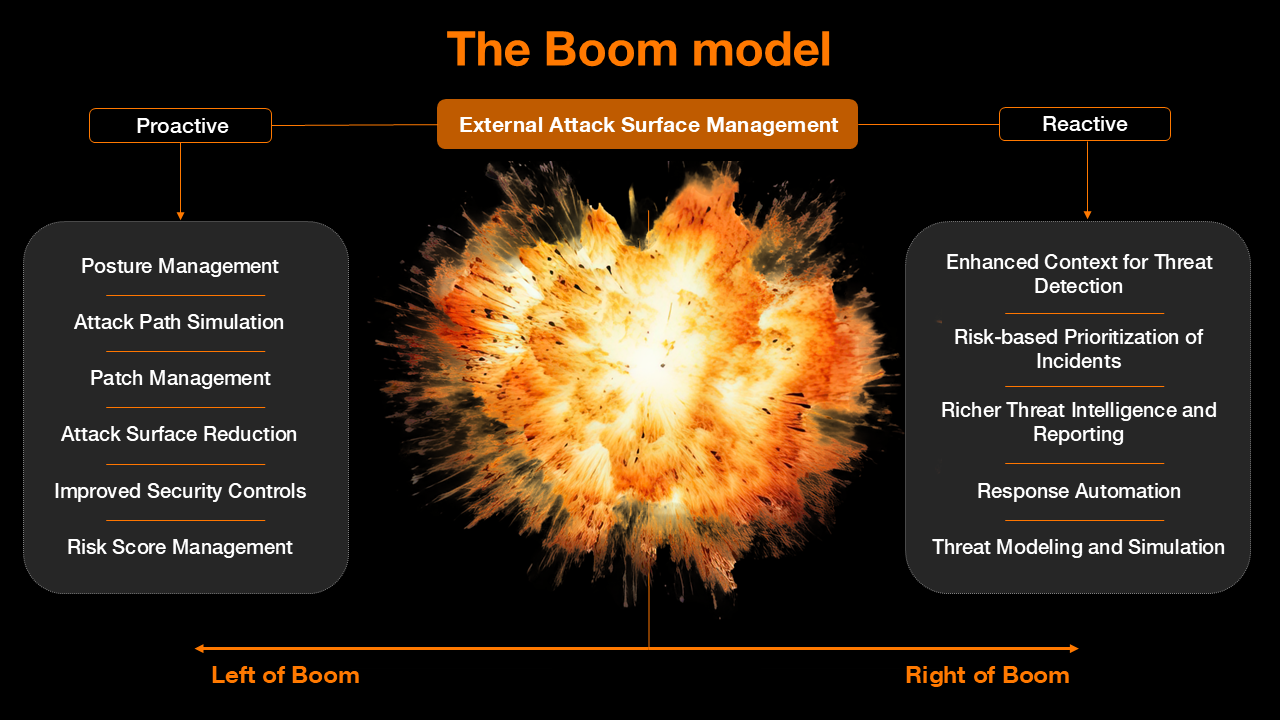
“On the left of boom, you have the proactive space — where you want to understand your attack surface, reduce your exposures, and prevent incidents. On the right of boom, you’re in reactive mode, detecting and responding to threats. EASM is a left-of-boom capability. It helps you act before things go wrong.”
This left-of-boom emphasis is essential for SOCs that want to reduce alert fatigue and be more strategic in their detection investments. By shrinking the attack surface proactively, they lower the volume (and urgency) of threats reaching the right side of the boom.
“This is where it’s heading,” says Nicholas. “A continuous flow of external discovery feeding into a unified platform that can detect, defend, and even remediate exposures - fast.”
For leaders starting their EASM journey, Nicholas’s advice is simple: start with identity.
“You need to understand who you are as an organization online — and that picture is changing all the time,” he says. “That’s the real value of EASM. It gives you a live map of your digital self — across clouds, suppliers, dev teams, and business units.”
And once you have that picture, the rest becomes possible: prioritisation, automation, and ultimately, better protection.
“EASM isn’t a nice-to-have,” Nicholas concludes. “It’s a critical part of building a modern SOC — one that’s ready for the speed and sprawl of today’s threat landscape.”
Click here to keep reading the modern SOC series.
Add EASM in your SOC

Global Product Manager
Orange Cyberdefense
Nicholas King is a cybersecurity professional with over 20 years of experience in IT infrastructure and security. As Product Manager at Orange Cyberdefense, he leads the development of cutting-edge External Attack Surface Management (EASM) solutions, helping organizations achieve continuous visibility, proactive risk reduction, and stronger resilience. A recognized expert in threat detection and protection, Nicholas combines deep technical insight with real-world leadership to ensure EASM becomes a core capability to bring value to Orange Cyberdefense customers.