Managed Vulnerability Intelligence [identify]
Staying on top of vulnerabilities
Take advantage of intelligent vulnerability management
In our research based report, the Security Navigator, it appears that 56.8% of vulnerabilities are taking between 31 and 180 days to get patched, 14% take longer than six months. A quick analysis of CVE sources shows that 1500 vulnerabilities are published on average each month.
Embrace a risk-based approach for vulnerability management
To protect business-critical assets and ensure compliance, a company needs to identify, prioritize and mitigate the most relevant vulnerabilities before cybercriminals exploit them. Systems, services, applications, and threats constantly change. There are too many new vulnerabilities everyday, therefore, it's impossible to patch them all.
All vulnerabilities are not actively exploited and all assets don't have the same level of priority according to the customers. We need to pay attention to the real organisational risk combining both the customer's environment and the threat landscape. There's no need to apply hundreds of patches but rather ten of them, selected ones, that will drastically reduce the attack surface of the company.

All vulnerability related data consolidated in the Vulnerability Intelligence Platform:
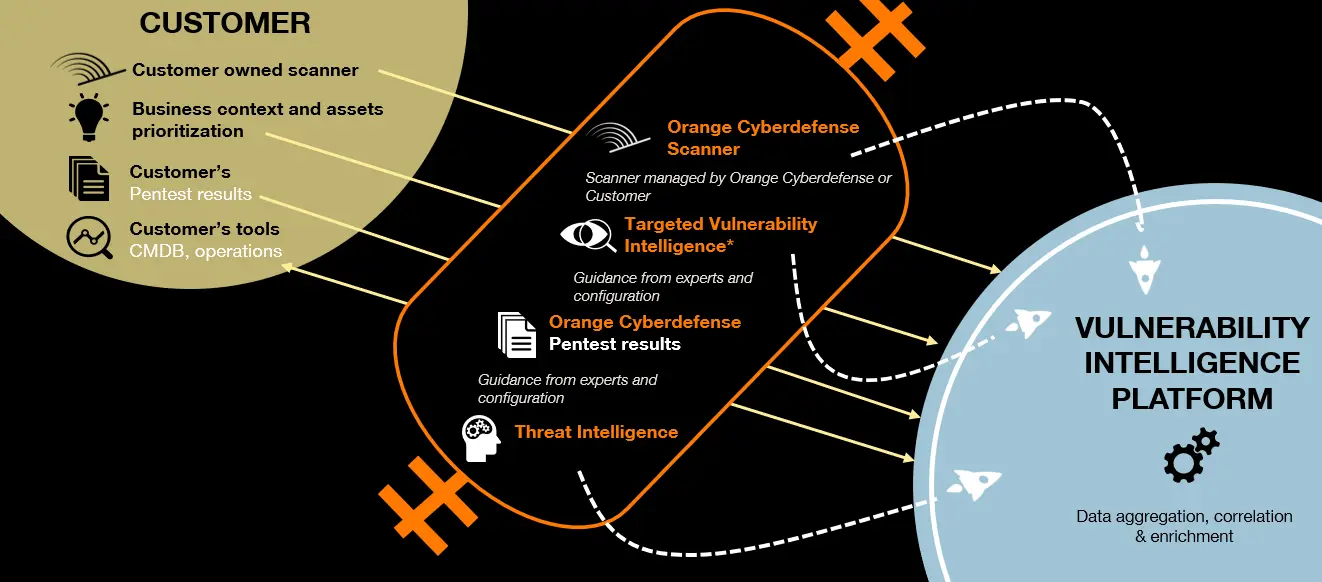
Managed Vulnerability Intelligence [identify]: continuous visibility of vulnerabilities to rapidly identify attack targets
The Orange Cyberdefense cloud-based Managed Vulnerability Intelligence [identify] services ensure you have experienced analyts armed with industry-leading tools on hand to identify, classify, and prioritise weaknesses as needed.
Without interrupting business-as-usual, we provide meaningful intelligence on verified vulnerabilities and the best route to remediate or mitigate against them via clear, personalised reporting.
Moving to a risk-based model rather than being simply driven by volume-based CVSS score fixes is key to making your vulnerability management programme a success.
The Managed Vulnerability Intelligence [identify] solution is really flexible.
If you already have your scanning platform in place you can keep it and decide whether Orange Cyberdefense should manage it or if you want to continue managing it.
The scanning platforms compatible with our service are: Qualys, Rapid7, Tenable and Microsoft Defender (TVM module). If you don’t have any scanning platform in place we will use our Orange Cyberdefense scanning platform.
We can also combine both your scanning platform and ours in case you want to extend the perimeters you’re already scanning and don’t want to manage the new scanning platform.
Exploit our experienced analysts and industry-leading tools to succeed
Complete Asset View
Have confidence that you have a view of all of the assets that exist that constitute your attack surface.
Scan everything
Whether it is network infrastructure, web applications or endpoints, we extract an accurate view of your vulnerability and associated risk data.
Report
Bringing all of that data together and enriching it with threat intelligence and customer-focused context, we report both tactically and strategically on your attack surface.
Guided Remediation
Once you have all the data and the ability to visualize it in a way that reflects your true business risk, our experts give you guidance and advice to produce smart, risk-based remediation decisions.