

Training Services
Knowledge is power
All trainings proposed by Orange Cyberdefense Switzerland are available as dedicated training sessions at the client's premises or as shared training sessions, organised throughout the year at Orange Cyberdefense's offices in Morges (see Training Calendar below).
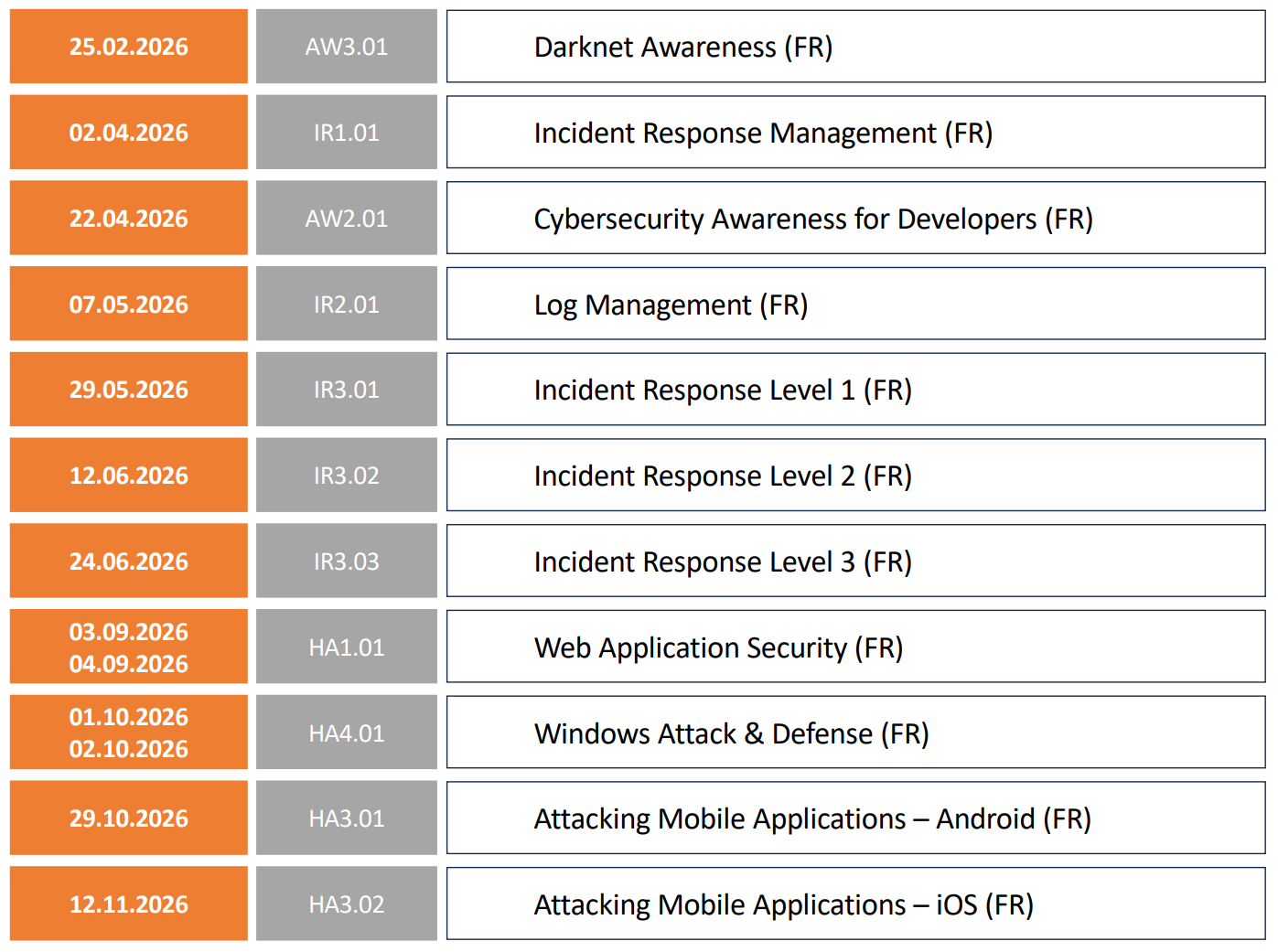
2026 Calendar (shared sessions)
Catalogue Overview
Download Training Catalogue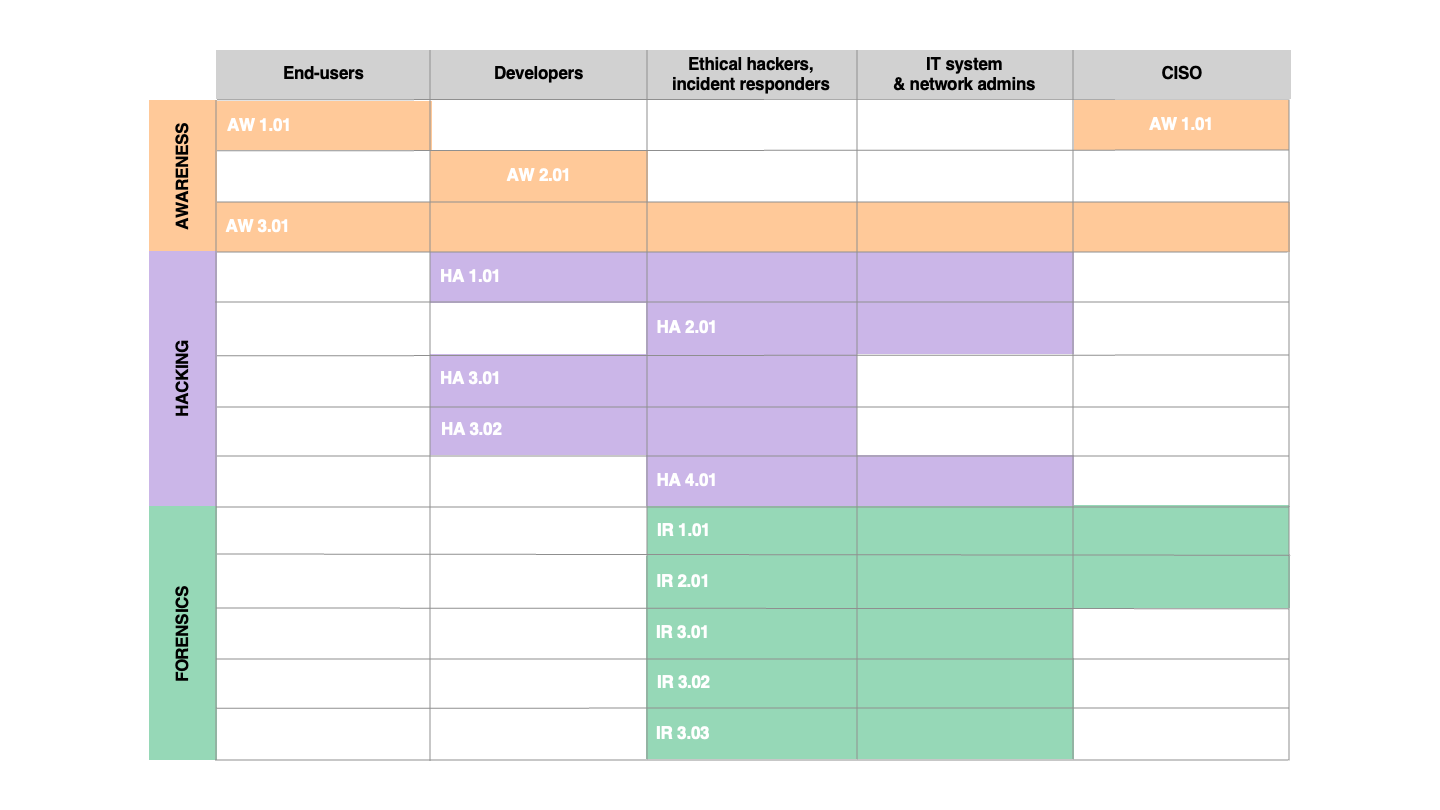
Building cybersecurity awareness
[AW 1.01] Cybersecurity Awareness for Users
Complex security measures can often be foiled by attacking the users of your information system. This 2-hours training, based on demonstrations and concrete examples, aims at providing end users with the correct tools and knowledge to respond to common threats such as social engineering, malicious software or the interception of communications. It is usually delivered at the customer's premises, in small groups but other formats can also be considered.
[AW 2.01] Cybersecurity Awareness for Developers
This training is aimed at raising awareness towards security issues for developers. It starts by presenting an attacker's methodology before turning towards the OWASP Top 10. Each category from the Top 10 is explained and demonstrated so that the participants properly understand the consequences of each issue. Remediation options are also proposed for each subject. Additional topics are covered based on current trendy vulnerabilities if they are not already covered by the Top 10.
[AW 3.01] Darknet awareness
This one-day course will introduce you to the concepts of the Darknet and allow you to delve deeper into the darkest corners of the Internet. The aim is to help you improve your monitoring and proactive security skills. In particular, you will learn how to search and communicate on the TOR network, and how to assess the impact of a leak from a third-party company on your business.
Incident Response and Forensic Analysis
[IR 1.01] Incident Response Management
This course is ideal for embarking on the long journey of incident response. Most of the process involves preparing in advance, and establishing procedures that you can rely on when the time comes. This halfday course is therefore an introduction to the concept of incident management, as well as the underlying best practices, norms and standards. It will enable you to lay the foundations of your defensive strategy from the point of view of preparedness.
[IR 2.01] Log Management
This one-day course covers the fundamentals of event logging on Windows and Linux, the different types of log, and the management and analysis of these logs. It is an ideal complement to the IR1.01 course and aims at examining what needs to be logged and how, so that you can improve your ability to respond to security incidents.
[IR 3.01] Incident Response & Forensic Analysis (Level 1)
This intensive hands-on one-day course is designed to introduce you to the investigation methods and tools you can rely on in the event of a security incident. It will take you into the world of incident response and forensic analysis, covering the different scenarios for acquiring RAM and hard disks, then focusing on triage through live analysis, as well as in-depth investigation through offline analysis.
[IR 3.02] Incident Response & Forensic Analysis (Level 2)
This intensive hand-om one-day course expands on the content of IR3.01 and introduces all the basic concepts you need to understand incident response and forensic analysis in a Windows environment. It covers advanced disk acquisition scenarios and will enable you to delve into the heart of the NTFS file system. You will also learn how to perform direct acquisitions of the operating system to extract valuable information from its many artefacts.
[IR 3.03] Incident Response & Forensic Analysis (Level 3)
This intensive hands-on one-day course complements the IR3.01 and IR3.02 courses by covering the fundamentals of mal- ware analysis on Windows. It aims to provide you with the methods and tools you need to carry out basic analyses, using both static and dynamic approaches. You will learn how to quickly assess the threat level of executable files and other Office documents.
Hands-on hacking
[HA 1.01] Web Application Security
Hands-on training which covers a broad scope of vulnerabilities that can be found in Web applications. The objective is to provide participants with the methodology and tools required in order to assess a Web application. It is tailored for developers or junior security engineers who want to start their journey in attacking and compromising Web applications. It does not dive in-depth into specific vulnerabilities, but rather covers a broad spectrum of issues to provide the participants with a basic understanding of all the relevant topics.
[HA 2.01] Attacking Windows environments with Metasploit Framework
This training presents the characteristics of the Windows security model as well as the most common attacks against corporate environments. Demonstrations and hands-on exercises allow participants to better understand how these attacks work and how to protect these systems effectively.
[HA 3.01] Attacking Mobile Applications (Android Edition)
| Comfortable with command line (Linux) Some experience with reverse engineering | 1 day | FR / EN | Level 3 |
Download the full description
This mobile training (designed for mobile developers or security engineers) covers common vulnerabilities that can be discovered in Android mobile applications. The participants will discover the methodology, and the tools used to attack and exploit mobile applications as well as apply them in diverse lab scenarios. This includes reverse engineering vulnerable applications and crafting malicious applications that exploit security vulnerabilities.
[HA 3.02] Attacking Mobile Applications (iOS Edition)
| Comfortable with command line (Linux) Some experience with reverse engineering | 1 day | FR / EN | Level 3 |
Download the full description
This mobile training (designed for mobile developers or security engineers) covers common vulnerabilities that can be discovered in iOS mobile applications. The participants will discover the methodology, and the tools used to attack and exploit mobile applications as well as apply them in diverse lab scenarios. This includes reverse engineering vulnerable applications and crafting malicious applications that exploit security vulnerabilities.
[HA 4.01] Windows Attack & Defense
| Comfortable with command line (Linux) Experience with Windows environments Familiar with pentesting & hacking tools | 2 days | FR / EN | Level 3 |
Download the full description
This training will familiarize system administrators and security professionals with modern Windows attacks and best security practices, such as Windows security components, network interception, Active Directory mapping, privilege escalation, lateral movements, credentials theft and common persistence techniques. After covering a large attack overview, the course introduces associated counter-measures such as credentials protection and much more. After the workshop, members will understand how to protect their infrastructure against modern attacks. Hands-on: This class is practice-oriented, lectures present realworld attacks that participants put into practice in various labs.



