
Managed Threat Detection [log] – Premium
The problem
Many SIEM implementations fail because massive amounts of data are fed into the SIEM, but out-of-the-box it only offers limited added value. The detection use cases that are often supplied in large numbers can often only be used to a very limited extent. Some can be used after extensive adjustments. With our standard use cases, we cover widespread attack scenarios and thus create immediate added value.
If SIEM installations are not continuously updated in order to be able to detect new threats, their usefulness decreases rapidly.
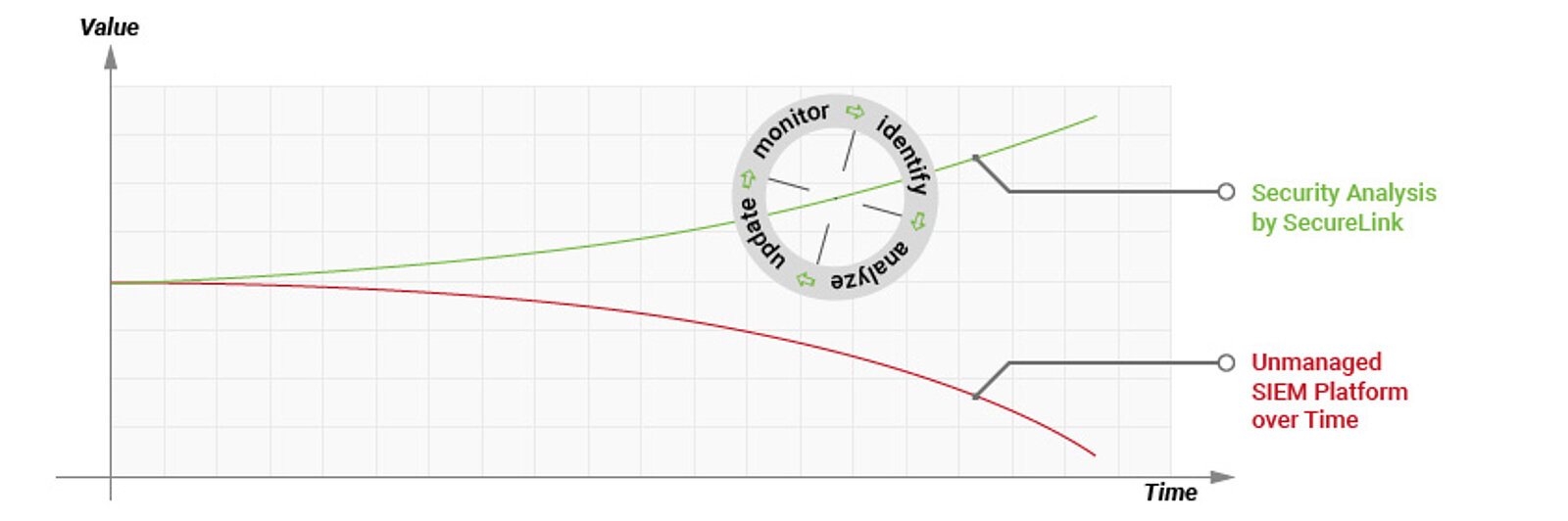
The solution: Managed Threat Detection [log] – Premium
Even if the analysis of security-relevant event data requires a high degree of automation, it is still not a completely automatable process. Only those who manage to combine the latest analysis technology with the know-how of human experts will continue to be one step ahead of the attackers and keep the upper hand.
This is exactly the approach we pursue in our Advanced Cyber Defense Center by combining the latest sensor technology and analysis methods with the expertise of our cyber security analysts and making them available to our customers in the form of our Security Analysis Service.
SecureDetect SIEM – Security Analysis is based on the analysis of security-relevant log data from our customers’ IT infrastructure. This log data is collected by a SIEM system that is integrated into this infrastructure.
A SIEM system ensures good transparency and visibility with regard to security-relevant events. But collecting data is one step; drawing the right conclusions from it is another. The collected data must be correlated and enriched with further information before it can be interpreted by human experts. Only then is it possible to derive the right knowledge from this in order to take the right measures to prevent or contain security incidents.
Our Advanced Cyber Defense Center is continuously developing new detection methods for so-called indicators, which are integrated into our standard use cases. Your investment in your SIEM system is thus permanently protected!
Use-case-based approach
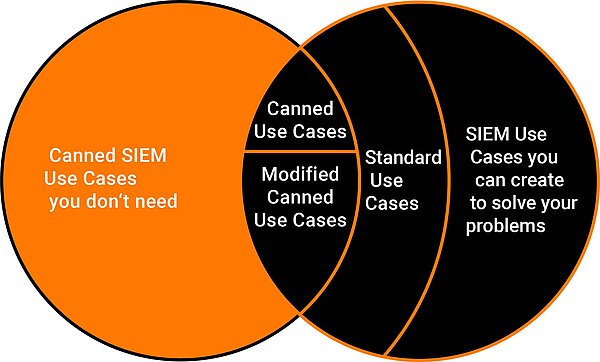
Our standard use cases cover common attack scenarios. They meet the requirements of various security standards and frameworks such as CIS Critical Security Controls, ISO / IEC 27001 or PCI-DSS.
Scope of services
- 8 × 5 or 24 × 7 service
- Use-case-based analysis approach for the reliable detection of security incidents
- Standard use cases included – Our standard use cases ensure immediate operationalization of your SIEM.
- Optional monitoring of add-on use cases – customer-specific detection scenarios are also seamlessly integrated.
- Optional threat hunting – The ideal complement to the deterministic approach of a SIEM to identify new attack vectors and to update detection scenarios and the necessary indicators.
Searching for clues in the data jungle
In the world of big data, countless endpoints, network infrastructure and the web, it is often difficult to filter the important information out of the noise. You don’t have to look far for the relevant facts about our SecureDetect Services. All you have to do is click on it and send it to us, and we’ll be happy to help!




